While security is taking the front row for many organizations, we still see too many others getting breached, facing the realities of ransomware, data theft, and extortion. These gaps require security professionals to be more efficient, flexible, and ready to face the changes enterprises need to be competitive and grow. Cybercriminals can target any organization, and that is why we have seen organizations investing time and resources in extending their security capabilities in detection, response, and recovery.
Two significant factors contribute to an effective cyber threat defense. First, prevention capabilities are all about blocking initial access to attackers; second, efficient detection and response are needed should a device be compromised.
Looking at prevention more closely, one major challenge is that most security policies are typically generic. At best, there might be a difference between High-Value-Asset (HVA)-type endpoints versus standard endpoints, but all security policies treat endpoints as equals regardless of whether the endpoint is considered compromised or not. Complex security policies often degrade the end-user experience, while light policies increase the available attack surface.
But what if security policies could be situationally-aware and automatically dial-up or dial-back security enforcement depending upon the endpoint’s risk status?
If we could do this, organizations would be able to make risk-based decisions. Today, SentinelOne is introducing Singularity Conditional Policy, a new Zero Trust Network (ZTN) feature that dynamically applies more security controls to devices that may be compromised, and then automatically unwinds these prudently-applied limitations once the device is deemed threat-free. With Singularity Conditional Policy, SentinelOne supports organizations in implementing Zero Trust Network (ZTN) concepts.
Introducing Singularity Conditional Policy
Singularity Conditional Policy is the world’s first endpoint-centric Conditional Policy Engine. Organizations can choose what their security configuration for healthy endpoints should be and choose a different configuration for risky endpoints. With this capability, we empower organizations to dynamically change security configurations based on the risk level of the endpoint.
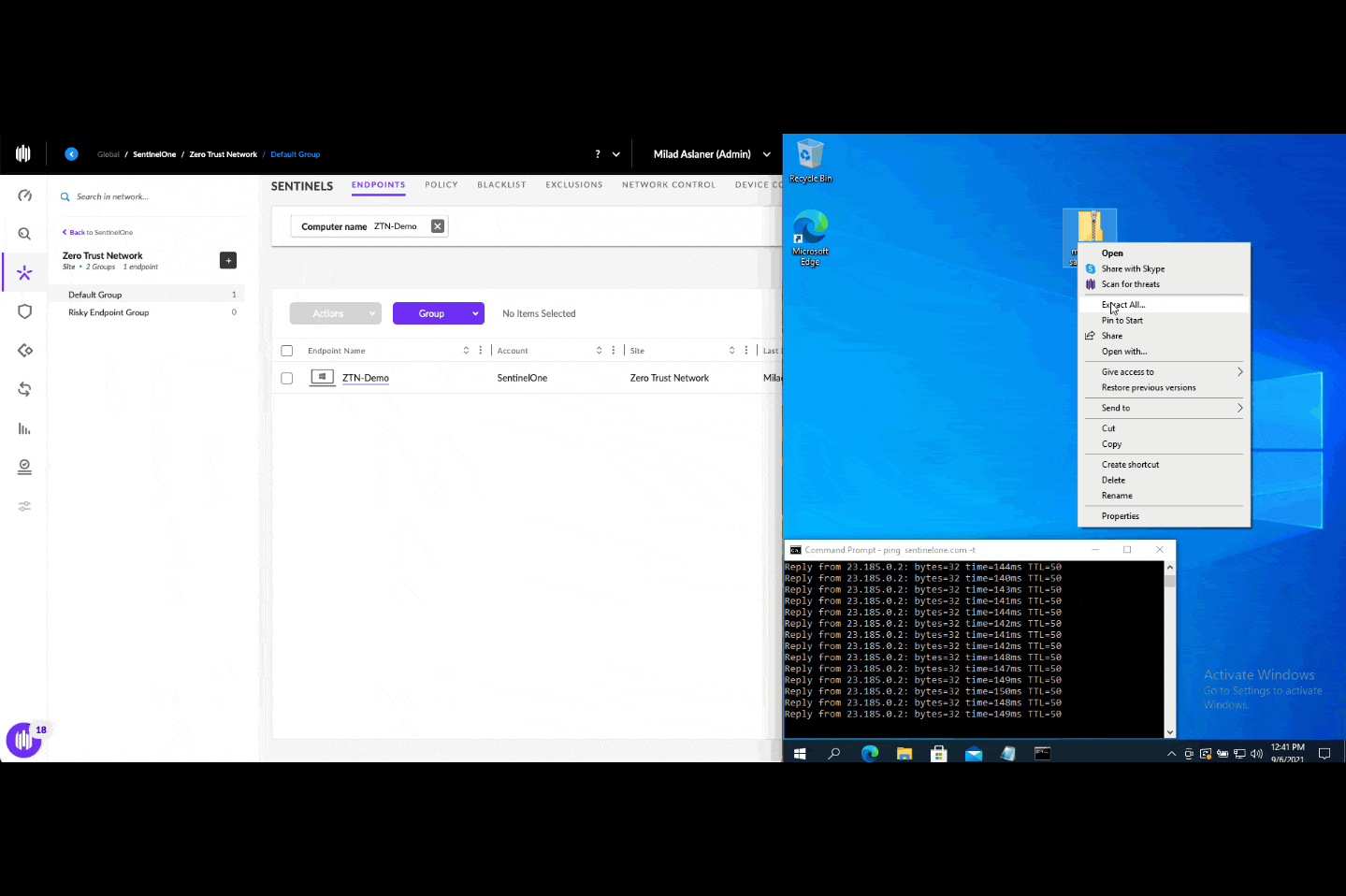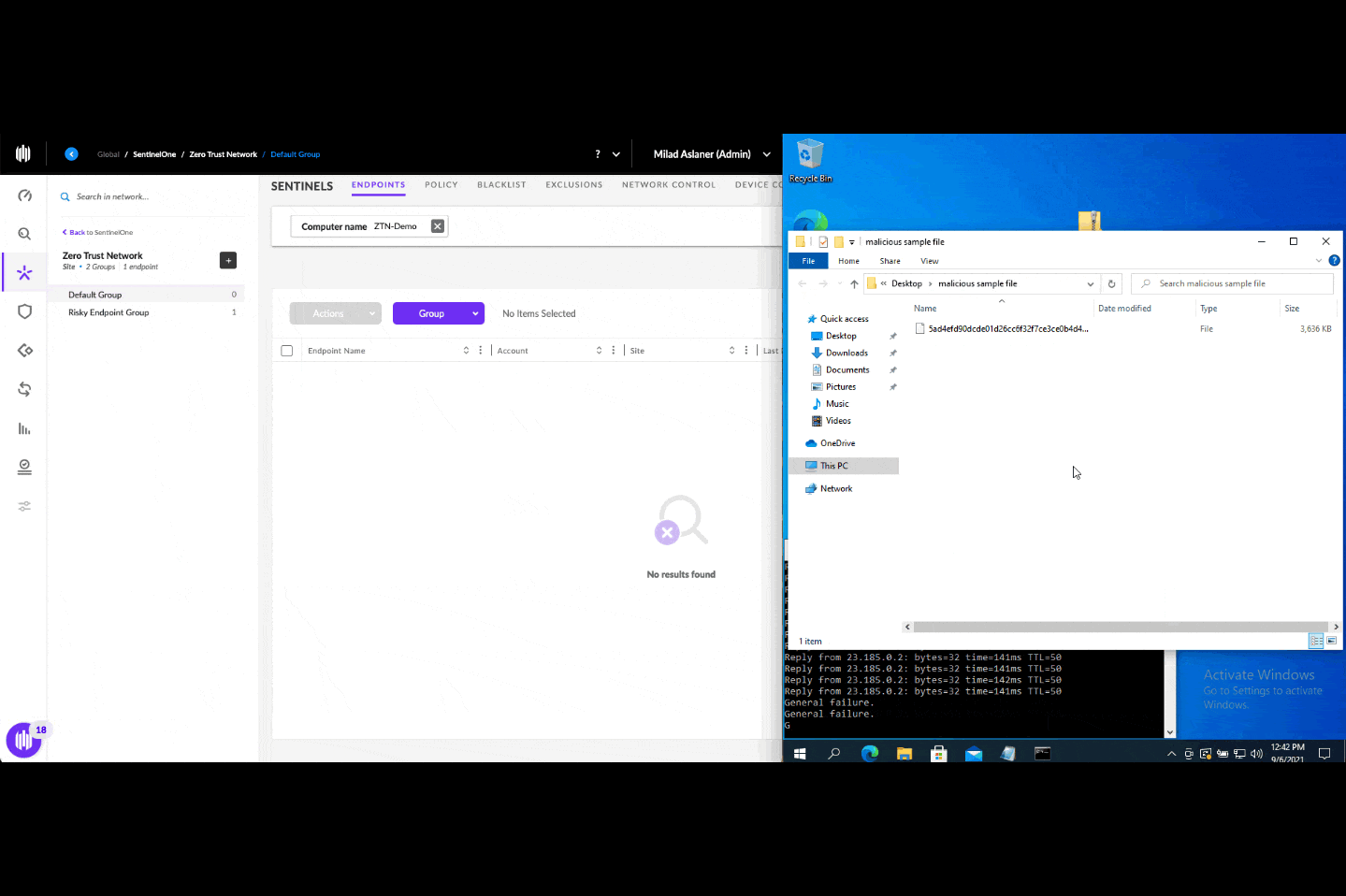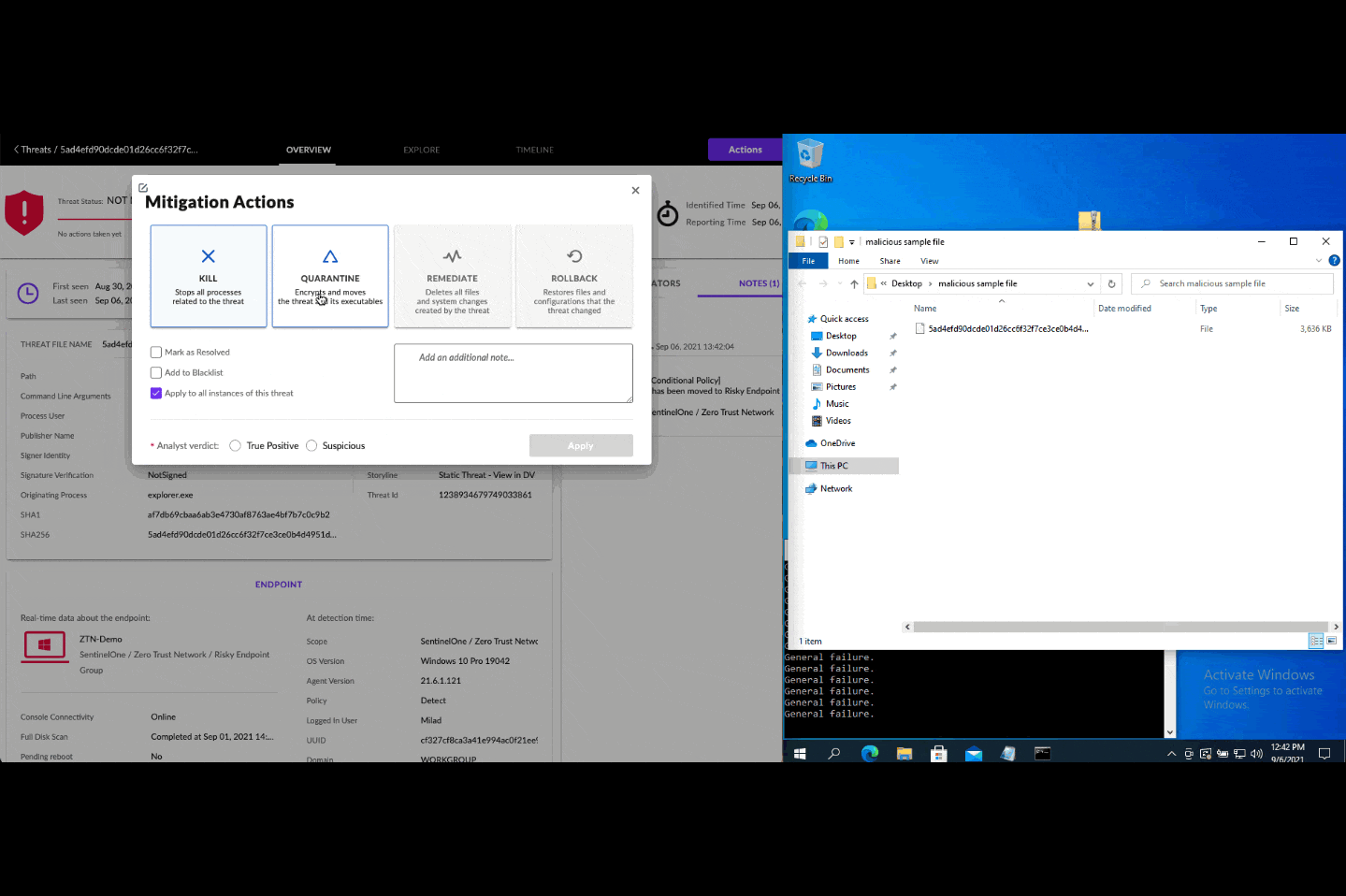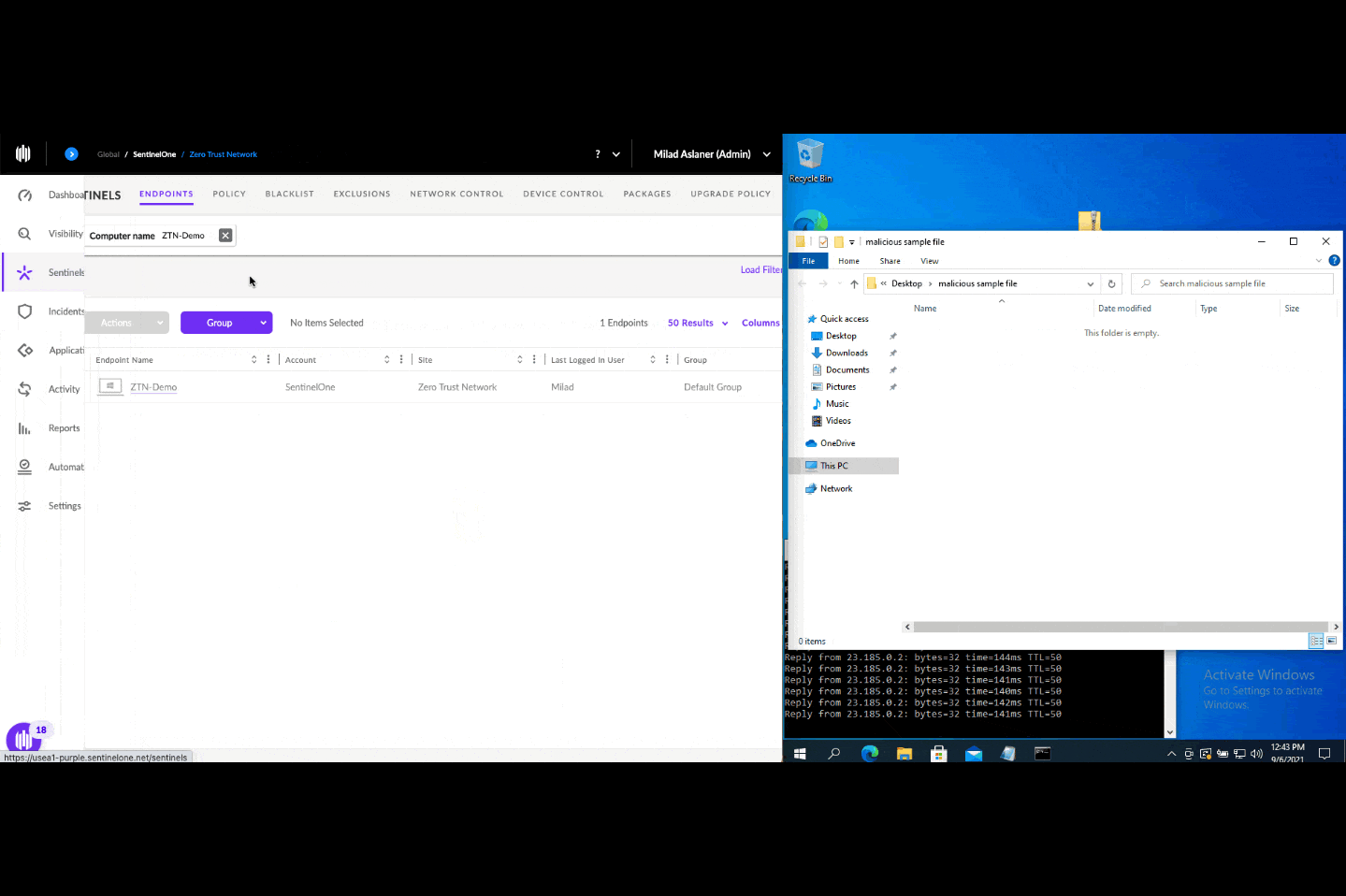
Endpoints are no longer trusted by default but rather are continuously verified for their health state. When an active threat impacts a SentinelOne-protected endpoint, Singularity Conditional Policy temporarily moves the endpoint to the risky endpoint group and applies the respective security configuration. Once the threat is remediated, the endpoint moves back to the healthy endpoint group and is assigned its old security configuration. In this way, Singularity Conditional Policy helps reduce the attack surface and prevent potential further damage.

Singularity Conditional Policy is available for all SentinelOne customers. To enable Singularity Conditional Policy, just follow these two simple steps.
1. Create an Endpoint Group and Configure Relevant Security Controls
In the first step, you create a new endpoint group where compromised endpoints will be transferred in real-time by the Singularity Conditional Policy Engine.
Once the new endpoint group is created, you can configure the relevant security policies.
For example, you might want to enable protection mode for suspicious activities, ensure that compromised endpoints can’t communicate with specific domains or IP ranges, and prevent usage of USB or Bluetooth peripherals.
2. Install Singularity Conditional Policy
Now that you have your risky endpoint group created and the security policies configured, you can visit the Singularity Marketplace and simply install the Singularity Conditional Policy app.
Real-Time Security Enforcement with Singularity Conditional Policy
Once this Zero Trust app is activated, you are all set: the Singularity Conditional Policy Engine is enabled. Moving forward, in the event that an endpoint is compromised, it will move in real-time to the risky endpoint group and increase the security enforcements. Once the threat is remediated, the endpoint will move back to its original group.
Summary
SentinelOne continues to lead the way with innovations aimed at keeping organizations safe while supporting the operational challenges of business growth. The Singularity Conditional Policy app is part of SentinelOne’s ZTN strategy helping organizations protect, detect, respond, and recover from cyber threats. Our endpoint-centric ZTN trust-but-verify approach makes it possible to evaluate the health state of endpoints and adjust security enforcements based on that state.
We can no longer assume that because the logged-on user is known to an organization, they should be safe and granted access to all corporate services and resources. Endpoints can no longer be treated equally without considering their risk profile.
Instead, security policies must be situationally-aware and dynamically enforced. Singularity Conditional Policy is SentinelOne’s first endpoint-centric Conditional Policy Engine that is now available to all SentinelOne customers. To find out more contact us or request a free demo.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.