When it comes to infrastructure security, every stakeholder has the same goal: maintain the confidentiality and integrity of their company’s data and systems. Period.
Developing and operating in the Cloud provides the opportunity to achieve these goals by being more secure and having greater visibility and governance over your resources and data. This is due to the relatively uniform environment of cloud infrastructure (as compared with on-prem) and inherent service-centric architecture. In addition, cloud providers take on some of the key responsibilities for security doing their part in a shared responsibility model.
However, translating this shared goal into reality can be a complex endeavor for a few reasons. Firstly, administering security in public clouds is unlike what you may be used to as the infrastructure primitives (the building blocks available to you) and control abstractions (how you administer security policy) differ from on premise environments. Additionally, ensuring you make the right policy decisions in an area as high-stakes and ever-evolving as security means that you’ll likely spend hours researching and reading through documentation, perhaps even hiring experts.
To partner with you and help address these challenges, Google Cloud built the security foundations blueprint to identify core security decisions and guide you with opinionated best practices for deploying a secured GCP environment.
What is the security foundations blueprint?
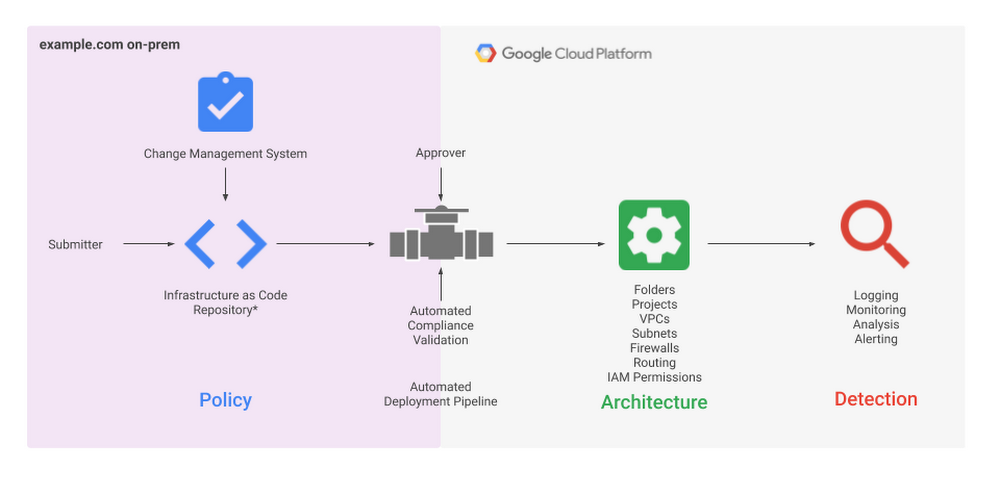
The security foundations blueprint is made up of two resources: the security foundations guide, and the Terraform automation repository. For each security decision, the security foundations guide provides opinionated best practices in order to help you build a secure starting point for your Google Cloud deployment, and can be read and used as a reference guide. The recommended policies and architecture outlined in the document can then be deployed through automation using the Terraform repository available on GitHub.
Who is it for?
The security foundations blueprint was designed with the enterprise in mind, including those with the strongest security requirements. However, the best practices are applicable to any size cloud customer, and can be adapted or adopted in pieces as needed for your organization. As far as who in an organization is going to find it most useful, it is beneficial for many roles:
- CISOs and compliance officers will use the security foundations guide as a reference to understand Google’s key principles for Cloud Security and how they can be applied and implemented to their deployments.
- Security practitioners andplatform teams will follow the guide’s detailed instructions and accompanying Terraform templates for applying best practices so that they can actively set-up, configure, deploy, and operate their own security-centric infrastructure.
- Application developers will deploy their workloads and applications on this foundational infrastructure through an automated application deployment pipeline provided in the blueprint.
What topics does it cover?
This security foundations blueprint continues to expand the topics it covers, with its most recent release in April 2021 including the following areas:
- Google Cloud organization structure and policy
- Authentication and authorization
- Resource hierarchy and deployment
- Networking (segmentation and security)
- Key and secret management
- Logging
- Detective controls
- Billing setup
- Application security
Each of the security decisions addressed in these topics come with background and discussion to support your own understanding of the concepts, which in turn enables you to customize the deployment to your own specific use case (if needed).
The topics are useful separately, which makes it possible to pick-and-choose areas where you need recommendations, but they also work together. For example, by following the best practices for project and resource naming conventions, you will be set up for advanced monitoring capabilities, such as real-time notifications for compliance to custom policies.
How can I use it?
While the security foundations guide is incredibly valuable on its own, the real magic for a security practitioner or application developer comes from the ability to adopt, adapt, and deploy the best practices using templates in Terraform, a tool for managing Infrastructure as Code (IaC). For anyone new to IaC, simply put, it allows you to automate your infrastructure through writing code that configures and provisions your infrastructure. By using IaC to minimize the amount of manual configuration, you also benefit through limiting the possibility of human error in enforcing these components of your security policy.
The Terraform automation repo includes configuration that defines the environment outlined in the guide. You can apply the repo end-to-end to deploy the full security foundations blueprint, or use the included modules individually and modify them so that you can adopt just portions of the blueprint. It’s important to note that there are a few differences between the policies for the sample organization outlined in the guide and what is deployed using the Terraform templates. Luckily, those few differences are outlined in the errata pages that are part of the Terraform automation repo.
So what should I do next?
We hope you’ll continue following the journey of this blog series where we’ll dive deeper into the best practices provided throughout the topical sections of the guide, discuss the different ways in which the blueprints have helped enterprises secure their own Cloud deployment, and take a look inside the Terraform templates to see how they can be adopted, adapted, and deployed. In the meantime, take a look at this recent Cloud blog post which announces the launch of the blueprint’s latest version and discusses the key security principles that steer the best practices.
If you’re ready to dive straight into the security foundations guide, you can start at the beginning, or head to a topic in which you’re particularly interested. Reviewing the guide in this way, you will be able to see for yourself the level of detail and discussion, and most importantly, the direct path it provides to move beyond recommendations and into implementation. We don’t expect you to try and apply the blueprint to your security posture right away, but a great first step would be to fork the repo and deploy it in a new folder or organization. Go forth, deploy and stay safe out there.