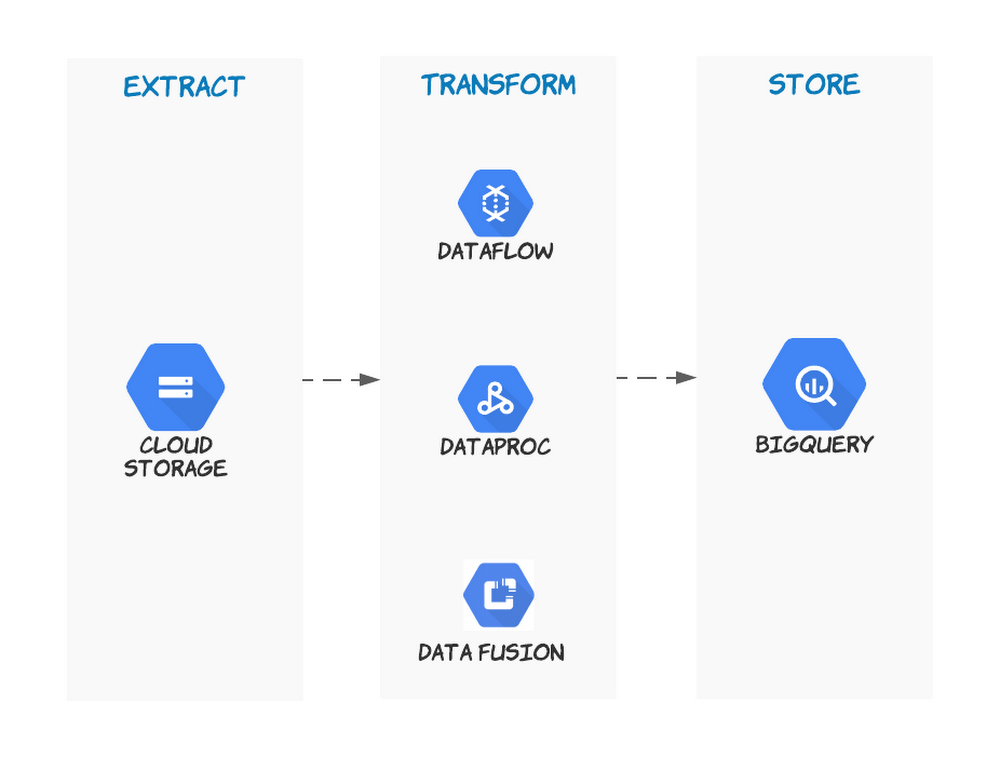
Orchestrating your data workloads in Google Cloud
June 17, 2021
Are we there yet? Thoughts on assessing an SRE team’s maturity
June 18, 2021The Good
This week saw another big victory in the battle against ransomware with the arrest of a large swath of individuals associated with the Clop ransomware operation. Law enforcement officials from the Ukraine, United States, and the Republic of Korea conducted over 20 searches across the Kyiv area, including personal property of the defendants. It is reported that the individuals in question are responsible for nearly $500 million in financial damages.
The Clop ransomware team has been in operation in various forms since 2018. Since then, they have targeted a number of high-value entities including Software AG, Qualys, and TAM International. More recent operations involved the exploitation of Accellion FTP software and appliances. It is reported that the apprehended individuals were primarily involved with the money laundering side of operations. Ultimately, this means that the primary actors behind Clop are still at large. However, this is still a significant blow to their infrastructure and finances.

This week’s good news in the battle against cybercrime was not solely about Clop though. A Russian individual tied to the operations of the Kelihos botnet has also been convicted. Oleg Koshkin maintained a “crypting” service that obfuscates malware payloads so as to evade detection by legacy AV software. Koshkin was convicted of providing a critical service that enabled other cyber criminals to infect thousands of computers around the world.
The Bad
While most well known underground forums have banned discussions and commerce around ransomware, there are still some small outliers that continue. We recently came across two new families being offered to would-be criminals, M3rcury and Camelvalley. In both cases, it appears that these tools are in the very early stages of active development.
M3rcury lists the following as its primary features:
- Removal of backups (shadow copies and other backups)
- Hybrid RSA AES-256 encryption
- UAC bypass
- Sandbox Detection
- Evasion of heuristic analysis
- Heavy obfuscation
- Scantime packed and crypted
- Single file decryption to get victim trust
All that and more for 150.00 USD!
Camelvalley is advertised at the same price with similar features, and they go so far as to call out the fact that other forums are backing out of the ransomware world. In their original post, they state:
The Camelvalley Ransomware comes out with plenty of interesting features, and even a solid Anti-Ransomware protection bypass that makes your cyberattack even more easier. The main goal of this project is to let you use less time on working on the ransomware itself and focus more on the evasion and hacking.”

M3rcury is written in Go and supports both 32 and 64 bit payloads. Camelvalley does not state the same, but it would be a fair assumption. In addition, CamelValley is said to have robust support for multithreaded encryption, uses a combination of RSA 2048 and ChaCha20 encryption algorithms, and makes use of the old RIPlace technique.
As stated before, both of these new ransomware offerings appear to be in the very early stages of development. Whether they emerge to become a true threat in-the-wild remains to be seen. The important thing to remember is this corner of the crimeware market will never go away.
The Ugly
This week the source code for the Paradise Ransomware was leaked across hacking and underground forums. The leaked archive contains all that is required to compile Paradise components from scratch. Upon compilation, users have the configuration builder, decryptor tool, and encrypter (the actual malware).
Paradise was never a particularly interesting family of malware. However, it is important to note that the leaked code does work. In the hands of a crafty individual, it is possible to generate new ransomware samples with a handful of configuration options. The ransomware generated from this leak is detected and prevented by most modern security software. It is, however, possible for individuals to modify the source to their needs, so time will tell what becomes of this.

Also in the world of data breaches, it was another busy week. We saw disclosures from Eggfree Cake Box, Carnival Corp, Intuit and more. These attacks are only getting more frequent and more aggressive. We also have ransomware actors sometimes forgoing the encryption step altogether and simply stealing data and holding it hostage. It is imperative that time and resources be spent on a robust, working, and tested disaster recovery plan. When was the last time cold storage was checked and verified? When was the last time you tested a restore of your backups? You should be able to answer questions like these, in addition to ensuring strong user hygiene and powerful modern endpoint security controls.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Read more about Cyber Security
- Gootloader: ‘Initial Access as a Service’ Platform Expands Its Search for High Value Targets
- Customize Your EDR To Adapt To Your Environment With SentinelOne STAR
- Securing the Enterprise – “I Thought We Had That Configured?”
- 12 Things To Know About macOS Monterey and Security
- Securing Hybrid Cloud Containerized Workloads in AWS ECS Anywhere
- 5 Questions to Consider Before Choosing the Right XDR Solution
- When Apple Admits macOS Malware Is A Problem – It’s Time To Take Notice
- SentinelOne is a Leader in the 2021 Gartner Magic Quadrant. Here’s Why.
- XDR Data Retention | Making Sure Your XDR Platform Outlasts Your Adversaries
- The Hunt For The Right Security Solution




