While ransomware has been making all the headlines recently, criminals have been reaping far more rewards under the radar through Business Email Compromise (also known as ‘Email Account Compromise’), netting at least 17 times more per incident than ransomware. BEC/EAC, a relatively low-tech kind of financial fraud, yields high returns for the scammers with minimal risk. In this post, we take a look at how the Business Email Compromise scam works and how you can defend your organization against it.

How Serious Is Business Email Compromise?
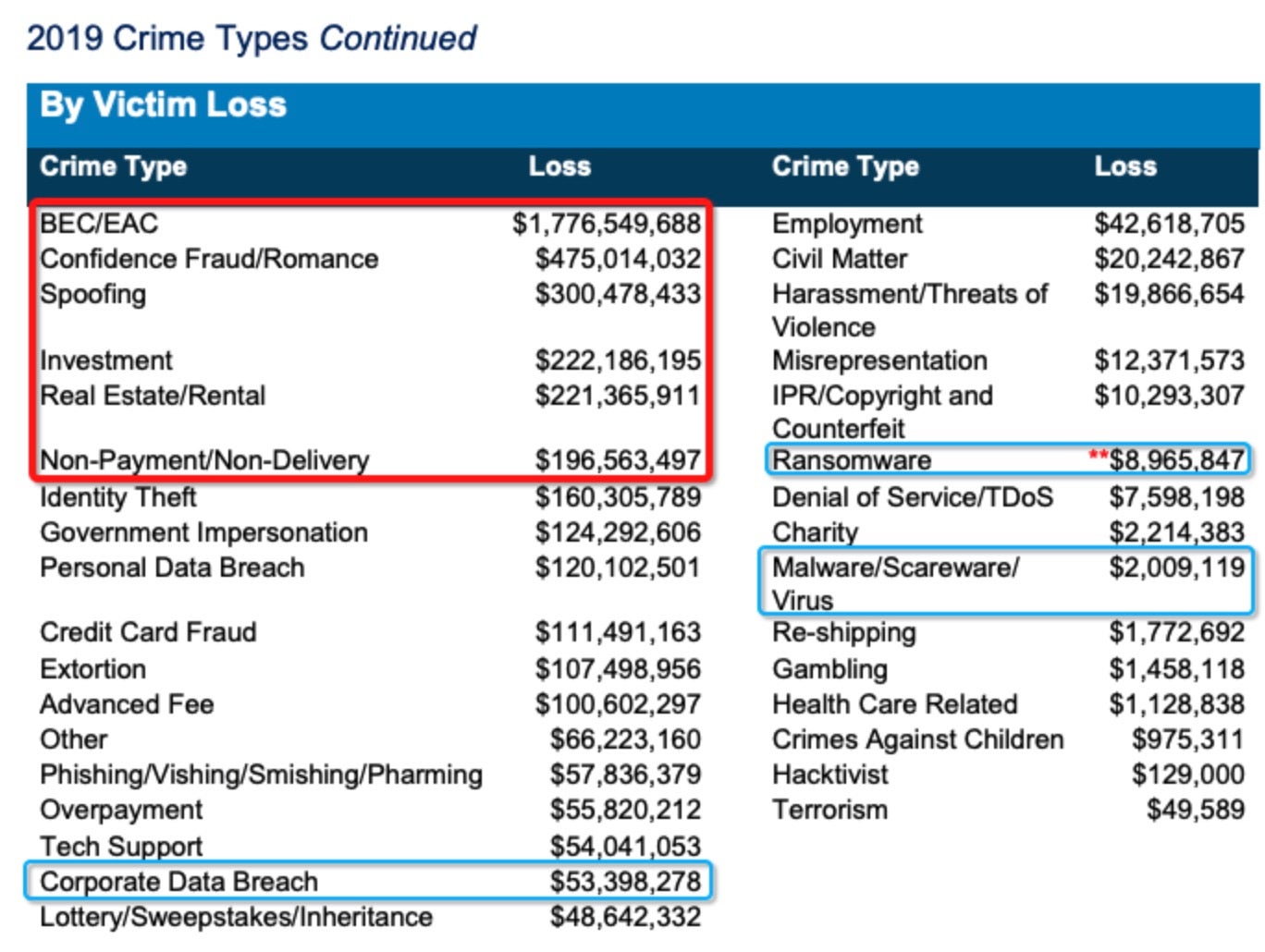
Business Email Compromise was the number one source of financial loss due to internet related crime in 2019, and by some margin. To put it in context, stats from the FBI suggest that losses due to ransomware averaged out at around $4,400 per incident and totalled just shy of $9 million in the U.S across 2019. In contrast, losses due to BEC were around 17 times higher, at $75,000 per incident, and amounted to a total financial loss north of $1.7 billion for the same period.
Of all financial losses due to internet crime recorded by the FBI during 2019 – in sum, around $3.5 billion worth – BEC accounted for around 50% of the total.
What is Business Email Compromise?
Business Email Compromise is a type of fraud in which organizations are tricked into making wire transfers to a third party that they falsely believe is a legitimate external supplier from overseas.
The scam begins by either compromising or spoofing the email account of an executive or senior manager who is able to authorize other employees, such as those in Finance or Accounts Payable, to make wire transfers.
The first part of the scam typically involves either a targeted phishing (aka spear-phishing) attack or credential theft through keyloggers. For example, a C-Suite executive may be targeted with a phishing attack that installs a Remote Access Trojan (RAT) to harvest credentials and other useful business information.
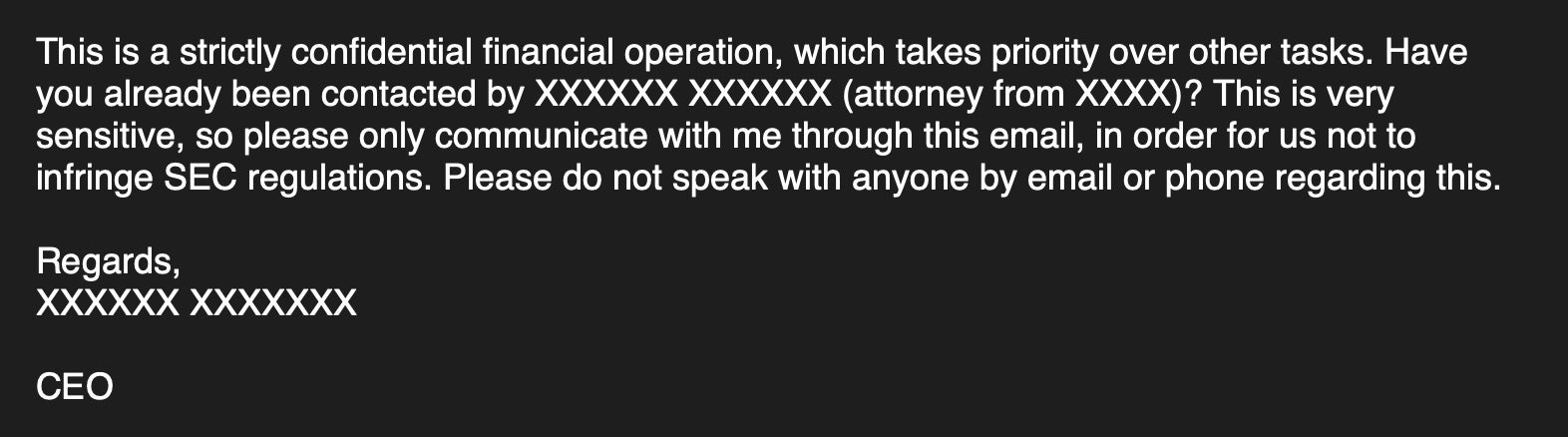
After that, the account is used to instruct other employees to complete a wire transfer request from a fake supplier. For example, a spoofed or hijacked account of a C-Suite executive may be used to send an internal email that reads something like the following:
Overseas banks, often in China, are used by the criminals to receive the funds.
Necessarily, there is an element of social engineering involved as the attackers need to convince someone to push the wire transfer through. Social engineering may also be used in order to steal passwords and compromise or spoof the initial account.
How Can You Defend Against BEC?
As we’ve seen above, Business Email Compromise revolves around three interrelated factors: email, people, and wire transfers.
Confirm Your Wire Transfers
Your company should always confirm wire transfer requests by some medium other than email: verify the request via a phone call through a known legitimate company number (not one provided in the email), a workplace communication channel like Slack, or even better face-to-face in person or via tele-conferencing software.
Ideally, your company should put in place a policy for secondary confirmation for wire transfers such that everyone knows the drill. Demands not to initiate communication through any other medium than email (itself hardly a confidential means of communication) should be treated with suspicion.
Enable Multi-Factor Authentication
Protecting your users email accounts from compromise should also be high on your priority list. Although not perfect, 2FA and MFA will prevent by far and away the majority of account takeover attempts. Hardware security keys like Yubikey and others are worth considering for certain use cases.
How to Detect Malicious Emails
Having a strategy to protect your users against malicious emails is the third, and absolutely vital, pillar of your defensive strategy. Email has long proven to be the malicious actor’s best friend. It’s been estimated that anywhere between 80% – 95% of all enterprise attacks propagate through email, so this is definitely where you need to concentrate your efforts.
Aside from the actual textual content of an email, which can be used to socially engineer individuals to take actions that may be harmful to their own or their organization’s interest, there are two main technical risks associated with emails: malicious attachments and links.
Strategies for Dealing with Malicious Attachments
In Business Email Compromises, attackers may use attachments to run executable code that can drop a RAT in order to install keyloggers, backdoors and other post-exploitation tools to help steal credentials and useful data such as contacts and previous email correspondence. BEC scammers typically spend some time profiling their victims in order to craft content that is as convincing as possible to pull off the social engineering aspect of the scam. For that reason, it’s important that you look at a range of options for preventing attachments from executing code.
Attachment filtering can be used in a number of ways to help mitigate code execution. For example, email scanning software could be used to change file formats of attachments so that they cannot execute hidden code.
While this may be effective to a certain extent, it suffers from the drawback that it may prevent users from carrying out ordinary business tasks with documents that need to be edited or returned in their original format. Given that impact, user-resistance could be high.
A better solution would involve content disarm and reconstruction (CDR), which deconstructs the attachment and removes harmful content. This has the benefit of being both highly effective and meeting low user-resistance, since the process is transparent at the user level.
Dealing with Macros, Archives and Whitelists
It’s also a wise idea to disable or restrict Macros, as many attacks make use of Microsoft Office’s VBA scripting language to call out to C2 servers and download malicious payloads.
Also, ensure that your email scanning software deals with archives properly. Compressed files can bypass some unsophisticated scanning engines if they do not decompress files fully. Attackers have been known to append archive files to other files like images, which some security software might overlook.
Be careful with (or avoid) whitelisting files by extension: it’s a simple trick for attackers to bypass such whitelisting rules by renaming executable files with non-executable file extensions. If whitelisting attachments is a must, at least use a policy that whitelists by file typing – scanning the file to examine its format – to avoid the easiest of bypasses.
Dealing with Links and Sender Verification
For emails that contain malicious links, one strategy used by some organizations is to defang hyperlinks in emails so that they are unclickable. This forces the user to copy and paste the link into a browser, a conscious process that provides an opportunity for users to pause and consider what they are doing.
Again, however, the issue is that whenever security impacts productivity and convenience, you will meet some user resistance. This security measure has the twin drawbacks of being both inconvenient and fallible, in the sense that introducing the delay still does not guarantee the user will not visit the link, so proceed with this policy with caution.
Another strategy to consider for dealing with emails is sender verification, such as through DMARC and SPF/DKIM. These technologies can help flag up fake sender identities (i.e., spoofed accounts), but they may not help in cases where the account belongs to a legitimate member of an organization but has been compromised by an attacker.
Finally, ensure that you are protecting against both malicious attachments and malicious links by arming your endpoints with an AI-driven security solution that can detect and block malicious code as it attempts to execute regardless of its origin: file or fileless, link or Macro.
Conclusion
Verifying wire transfers and enabling multi-factor authentication are simple, effective ways to get ahead of scammers intent on Business Email Compromise. On top of that, consider the practicality of the techniques we’ve mentioned above as part of a layered, defense-in-depth approach.
While Business Email Compromise scams target the weakest link – busy staff trying their best to be productive – an automated, behavioral security solution like SentinelOne can also ensure that attempts to install RATs, keyloggers and other malware are stopped in their tracks.
If you would like to see how SentinelOne’s Singularity platform can protect your enterprise from all attacks, including Business Email Compromise, contact us or request a free demo.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.