A Guest Post by Jeffrey Smith. Jeffrey founded Cyber Risk Underwriters to offer tech-backed cyber insurance and related products distributed by insurance agents and cyber security providers.
Insurance is easy to hate. You can’t touch it and it is difficult to understand. Cyber insurance is particularly confusing. The product is relatively new and evolving quickly, making it ever more difficult to understand for lay people and insurance professionals alike. To make matters more complicated, the ubiquitous nature of cyber risk can trigger some level of coverage in multiple business insurance policies. As a result, cyber insurance is often misrepresented and confused with other types of insurance. It is not only alleged that the policy doesn’t pay claims, but InfoSec professionals are concerned that the purchase of a cyber insurance policy threatens funding for existing cyber security efforts.

Business Insurance is Confusing
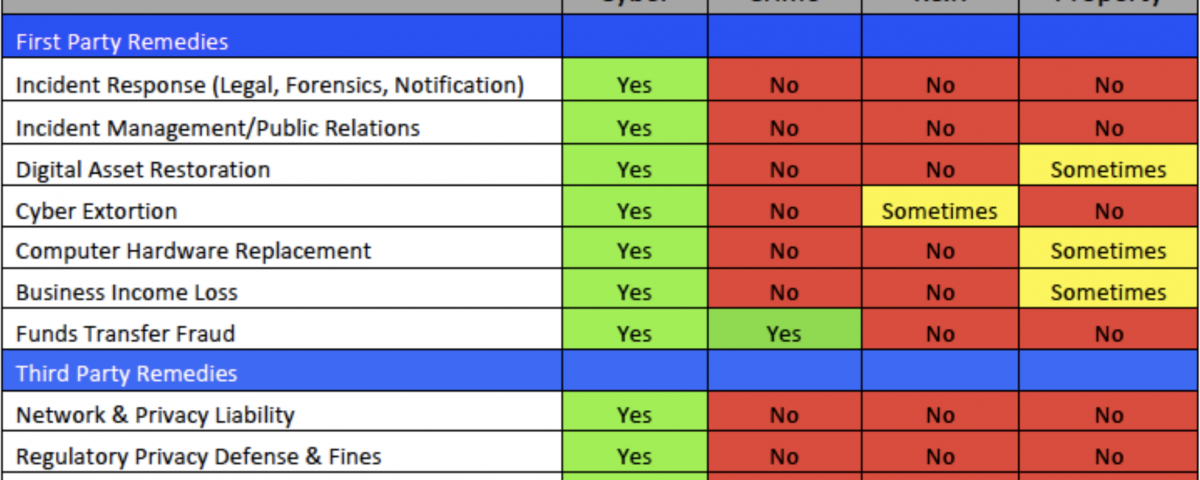
The source of the most confusion results from the fact that multiple business insurance policies may provide coverage for some aspect of cyber loss. The table below indicates typical coverage overlaps found in various business insurance products. Oft-cited claim disputes such as Mondelez, National Bank of Blacksburg and others do not involve stand-alone cyber insurance.
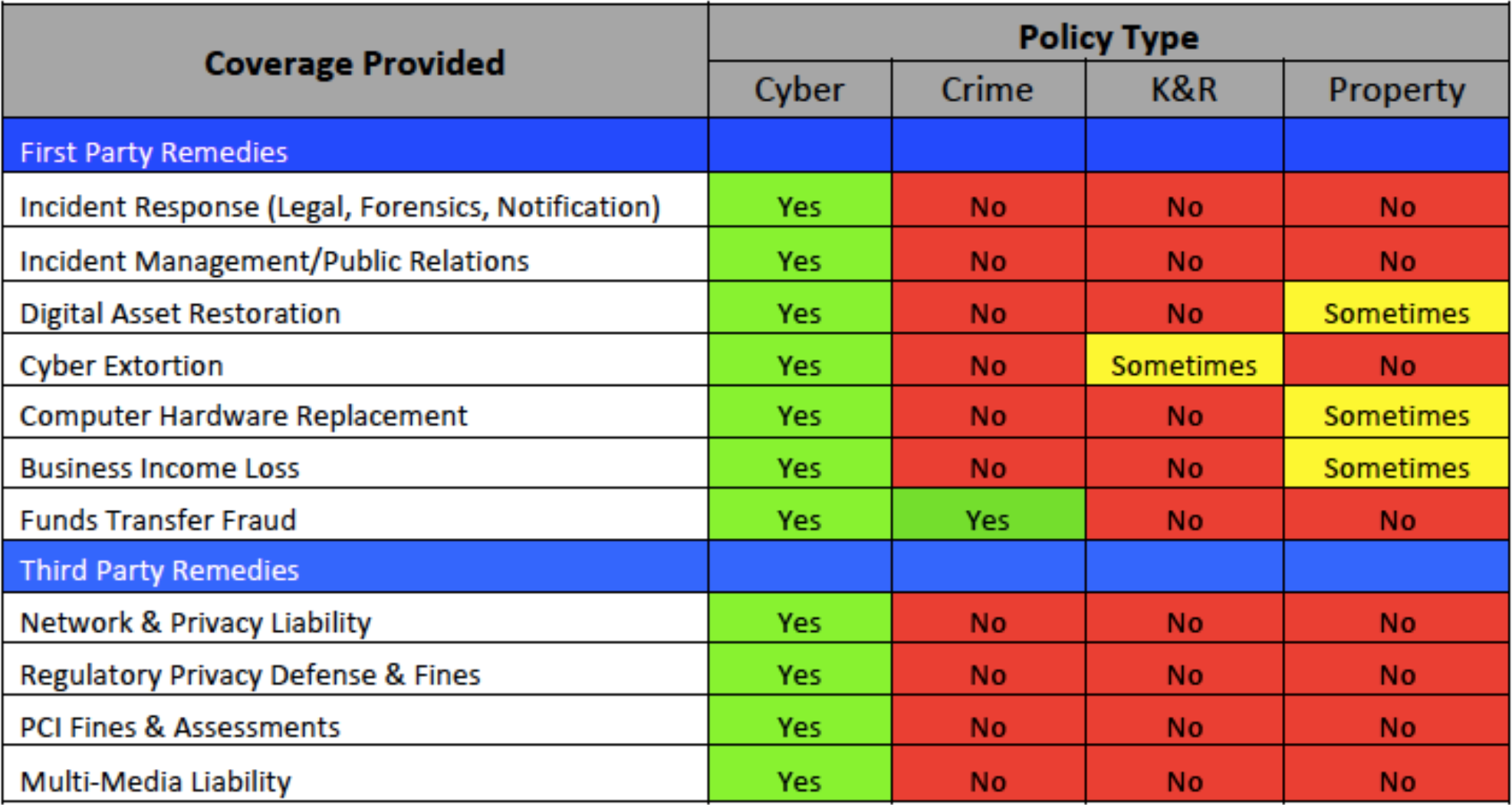
These companies did not purchase stand-alone cyber insurance. As such, they are pursuing recovery under other insurance policies that often contain limited coverage grants consistent with exposure overlaps. Since these other insurance policies are not designed to respond to all cyber events, the insurers are going to the mat to restrict payments to the bespoke and limited coverage provided. Crime, kidnap and ransom, and property insurance are the most notable ‘other’? insurance policies; however, overlaps are also found in other policies such as professional liability, management liability and general liability products.
Human Error & Failure to Maintain
We often hear that cyber insurers try to find ways to avoid paying claims, citing human error or an insured’s failure to maintain a threshold of security efforts. From our experience, 85% of paid cyber insurance claims involve human error. These typically include not following existing procedures, clicking on malicious links, and falling victim to sophisticated social engineering attacks. Not unlike legacy cyber security software, early versions of cyber insurance policies were not very good compared to current products.
As an example, many early cyber policies included a ‘failure to maintain’? condition that precluded coverage in the event the insured did not maintain specific security controls. Today’s cyber underwriters are better equipped to evaluate exposure, so today’s policies no longer include this restriction. However, it is important to keep in mind that if you indicate on the insurance application that you encrypt all information at rest, and it is discovered that no such process existed, your claim may be denied. As long as you are honest during the application process, a single error or omission in application of stated security protocols will not preclude a coverage response by your cyber insurance policy.
Cyber Insurance Is Not a Replacement for Security Practices
The idea of course, is not to experience a cyber claim. As mentioned here before, cyber insurance should not, under any circumstance, be seen as a replacement for a robust security posture, which requires modern cybersecurity technologies, trained teams and tested procedures.
Sentinel One is among the less than 1% of InfoSec vendors to stand behind product performance (for more information on product guarantees, check this out). However, Infosec technology vendors do not provide financial guarantees for all costs associated with human error or failure of product performance.
The primary role of cyber insurance is to provide financing of breach costs and liability resulting from a cyber event. In our view, cyber insurance is the last puzzle piece of any cyber risk management process.
Conclusion
High profile claims such as Mondelez, National Bank of Blacksburg, DLA Piper and others wrongly suggest stand-alone cyber policies do not pay. Product confusion and the use of brokers without cyber expertise often result in false expectations for claims recoveries. Make sure to use insurance brokers with specific cyber insurance expertise. Use your broker to review policy coverage parts, conditions and exclusions prior to purchase. Get quotes from multiple insurers. If you want to use one of your vendors for incident response, try to negotiate that into the deal. A good policy includes bespoke coverage for cyber-terrorism events (such as NotPetya) and is devoid of any ‘maintenance’? conditions as found in older policy versions.
It is common sense to use all available tools to protect from catastrophic peril. While not the most important part of your cyber security platform, a carefully crafted cyber insurance policy is a great addition to your existing cyber risk management program.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.