In new research published yesterday by SentineLabs, head of research Vitali Kremez reveals how a Russian-backed APT threat actor known as the ‘Gamaredon group’ has intensified its clandestine cyber warfare activities against Ukrainian national security and infrastructure targets, even as Russia and the Ukraine go through the external motions of conflict resolution in the wake of the armed conflict that broke out in the Donbass region in 2014.

Who Are the Gamaredon Group?
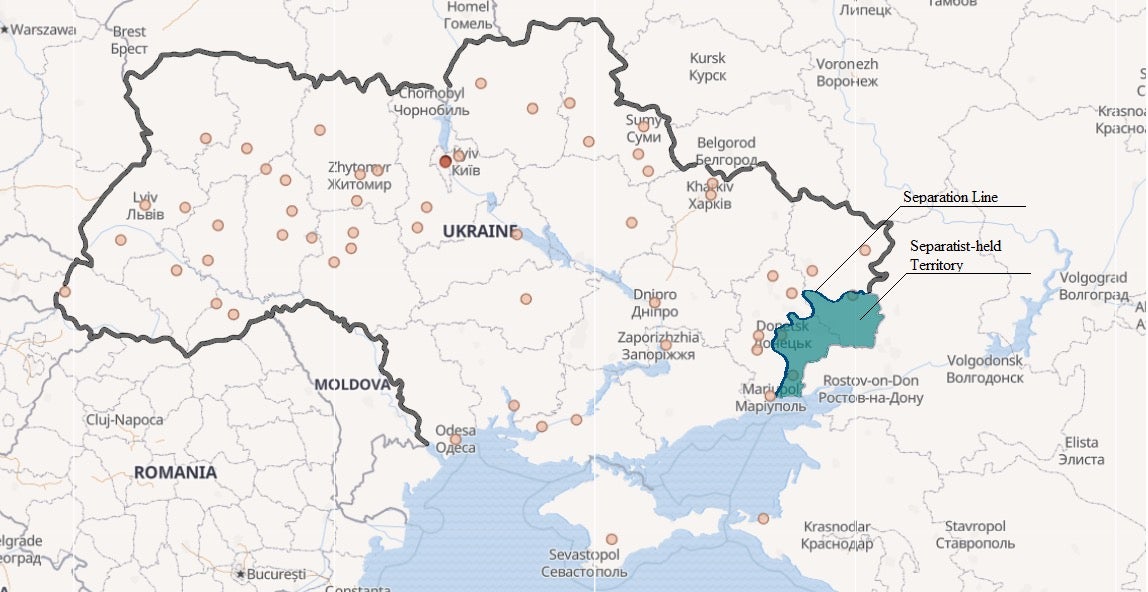
According to the report findings, the Gamaredon group functions as a proxy for Russian intelligence and pro-Russian groups with a remit to conduct attacks such as espionage and intelligence gathering on Ukrainian military forces. In the event that armed conflict were to break out again between the Ukraine and separatists, intel gathered by the Gamaredon group would help to give the pro-Russian forces a strategic edge.
But the group’s purpose is likely to extend beyond the Ukraine. The report quotes Secretary of the NSDC Security Council of Ukraine Aleksey Danilov’s claim that “the country has become a testing ground for Russian cyber attacks“?, and goes on to point out that Gamaredon’s activities allow the Russian military and other agencies to observe the potential of utilizing cyber warfare in a contemporary violent conflict. In other words, the group’s experience can feed into a wider understanding of how adversaries respond to its tools, tactics and procedures in order to iterate and improve those for potential use in future conflicts or against other foreign targets.
SentinelLabs telemetry shows that the group has attacked over 5000 individual entities across the Ukraine, with particular focus on areas where Ukrainian troops are deployed.
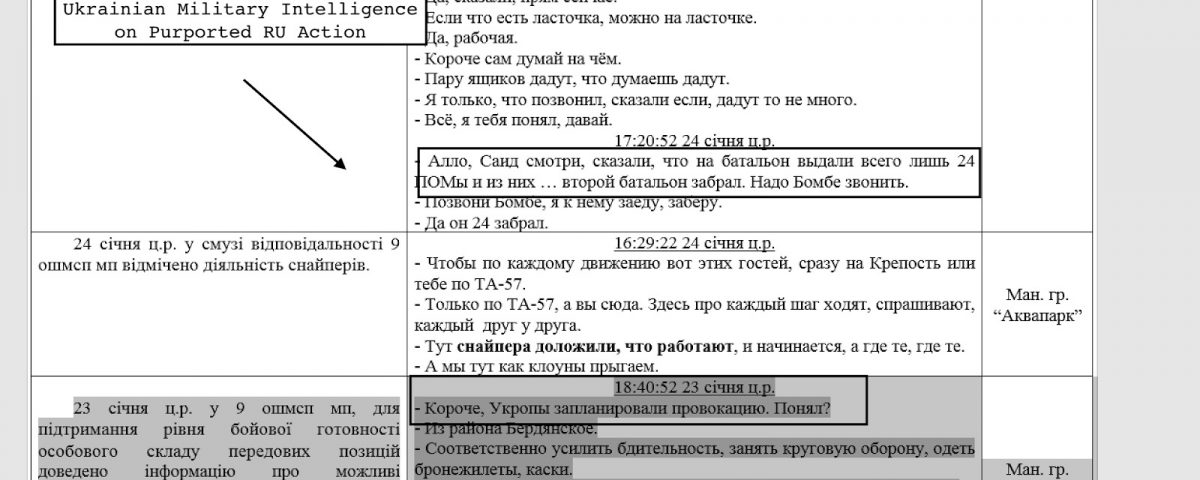
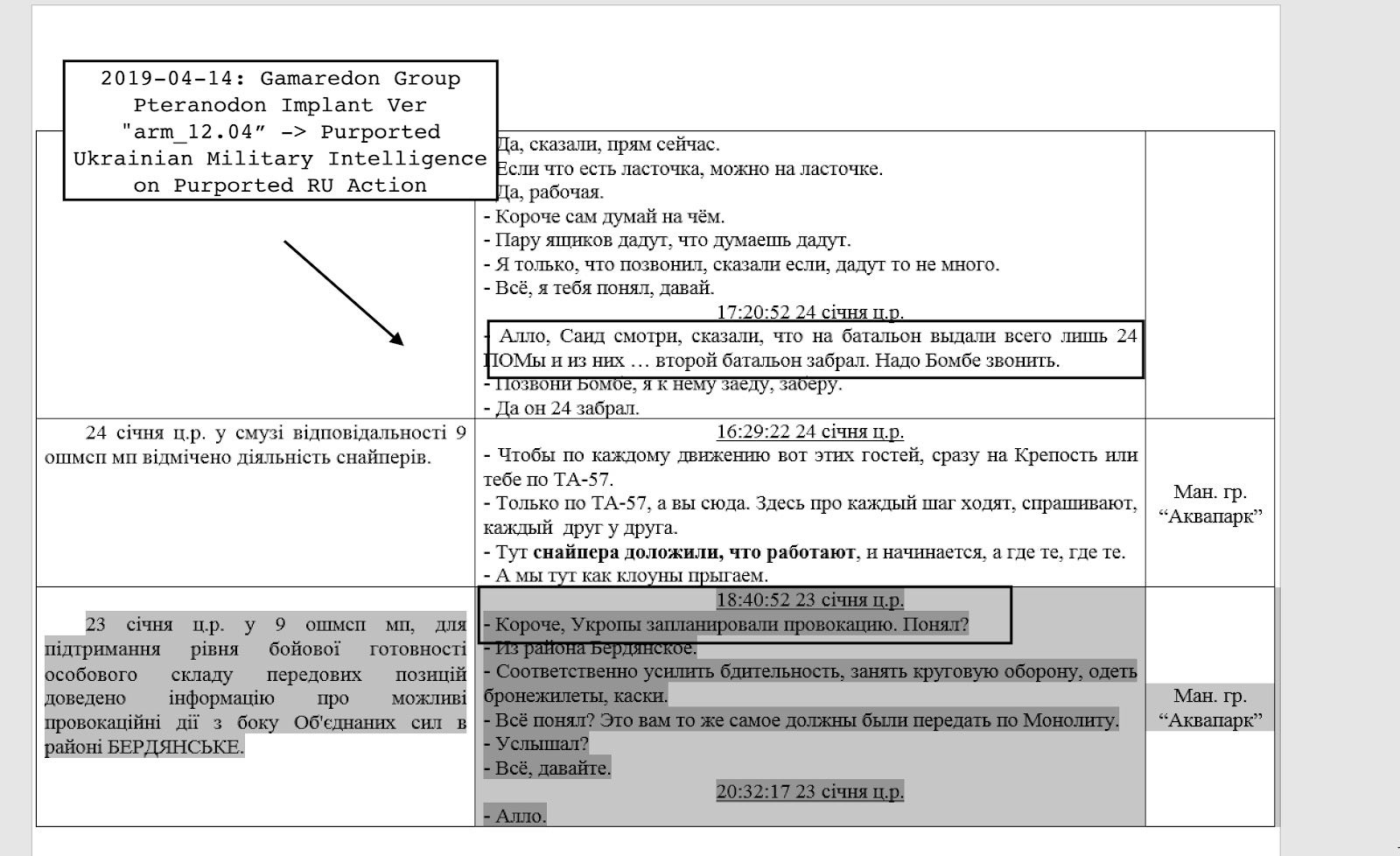
Multi-function Pterodo Custom Malware
The Computer Emergency Response Team of Ukraine (CERT-UA) has been warning for some time that the Pterodo-type malware it had been seeing on endpoints belonging to Ukrainian state authorities was likely a preparatory stage for a cyber attack. The malware gathered up system data and communicated with C2 servers via a backdoor, apparently waiting for further instructions.
However, the research showed that this toolset has had extensive updating. Social engineering campaigns serve to implant malware through obfuscated Excel and Word macros. The malware allows macro execution while disabling Visual Basic for Applications (VBA) warnings. It also uses a fake Microsoft digital certificate belonging to Microsoft Time-Stamp Service to achieve trust on the local system. More technical analysis is provided in the SentinelLabs report here.
What the Gamaredon Group Research Means to Enterprise
As the report makes clear, Gamaredon is very much a training exercise, and who better to test it on than a military adversary? While Gamaredon may currently be focused in a particular arena, it’s reasonable to assume that the lessons learned by this group in terms of espionage and data gathering are likely to be shared among other Russian intelligence agencies and cyber actors, many of whom we know are focused on both governmental and enterprise organizations in the U.S. and other countries.
SentinelOne customers are already fully protected from Gamaredon Pterodo malware, and a full list of IoCs and further technical details are available here. If you would like to see how SentinelOne’s autonomous AI solution can help protect your organization from attacks by Gamaredon and other APT groups, contact us today or request a free demo.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.