You’ve likely heard the names: Emotet, Trickbot, Dridex. These are some of the most notorious botnets currently on the loose in cyberspace, infecting and enslaving hundreds of thousands of machines. Last month, the UK’s Labour party was hit by two DDoS attacks from threat actor group Lizard Squad, who claimed to have control of a botnet connected to “millions of devices”. And earlier this year, a Brazilian botnet of 400,000 IoT devices conducted a massive attack against one site issuing more than 200,00 requests per second over a 13-day period. The threat from botnets is one of the most serious issues facing enterprises today. In this post, we take a closer look at what botnets are and how they work.

What is a Botnet?
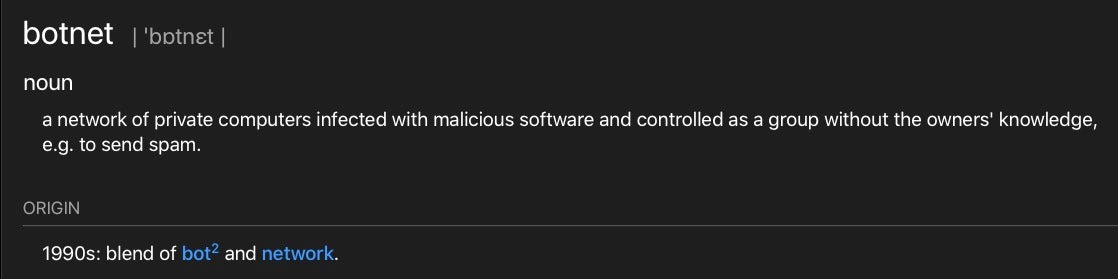
A botnet, in simple terms, is a network of infected computers that are controlled as a single entity by a malicious actor. That means the actor can have all the computers in the infected network carry out the same instructions at the same time.
This power to perform actions at massive scale, to coordinate the behaviour of hundreds of thousands of internet-connected machines, is what makes botnets so fearsome. If combined with wormable properties, the botnet can not only act at scale but also infect other machines on the same corporate network and enslave those, too, thus providing the botnet with autonomous growth.
What Are Botnets Used For?
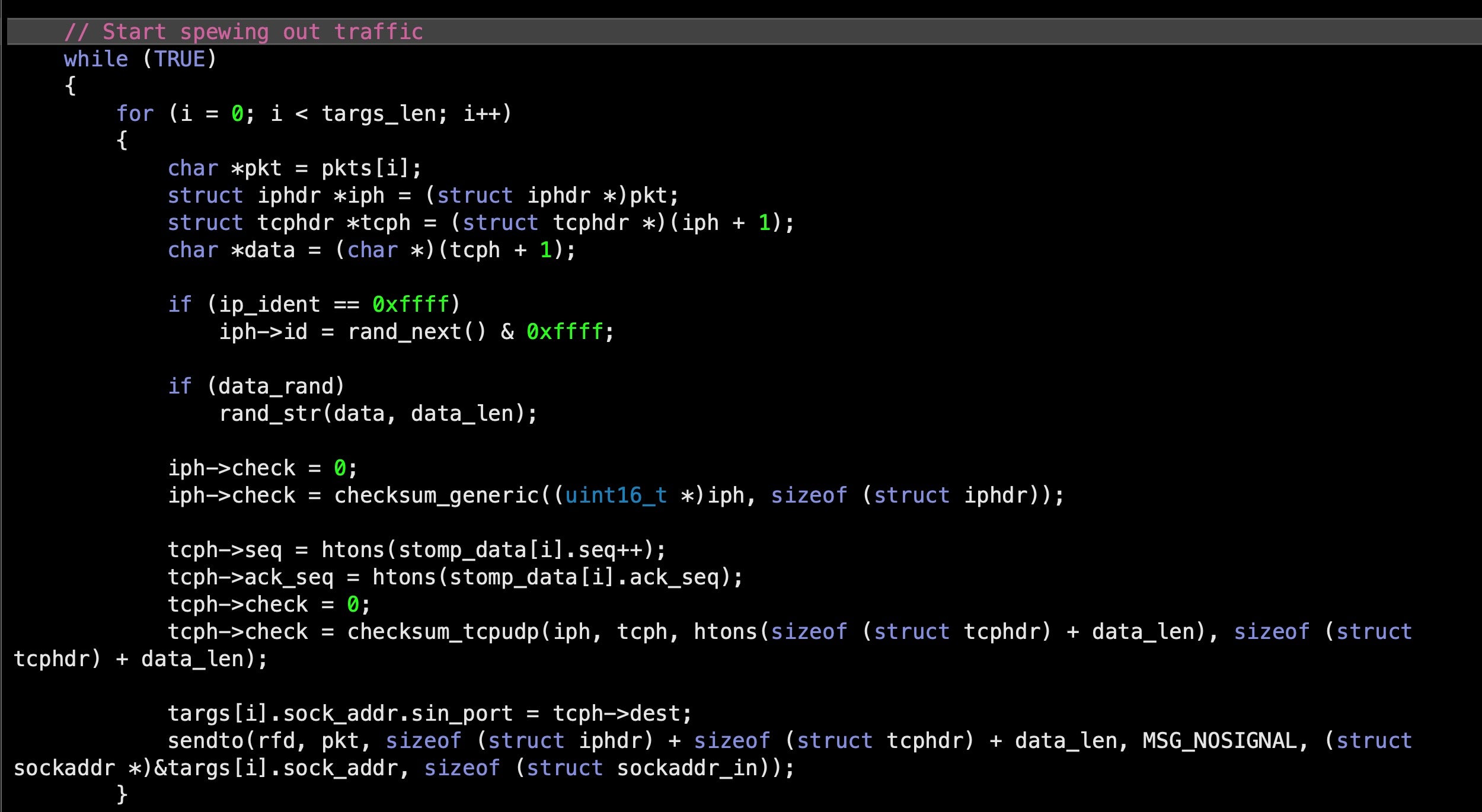
One of the most common uses of botnets is to carry out DDoS (Distributed Denial of Service) attacks against enterprise servers and websites. A DDoS attack occurs when a large number of devices all try to connect to a server at the same time. This can overload the server’s ability to deal with all the incoming packet requests and knock it offline, thus making it inaccessible to genuine customers wishing to use the service.
There have been several high-profile examples of such denial of service attacks. Mirai malware, whose author “Anna Senpai” notoriously released the source code on Hackforums website leading to a multitude of copycats, is one of the most successful botnets used for DDoS. Mirai was used to target independent security blogger Brian Krebs after he exposed two individuals behind a previous DDoS attacks on Github and DNS provider, Dyn.
The Mirai botnet was used to specifically infect Linux IoT devices like security cameras, printers, routers and other simple internet connected appliances.
Botnet-powered DDoS attacks are a problem that can affect others beyond the immediate target, too. As most websites are themselves hosted behind other ISPs or content delivery network providers like Akamai, Cloudfare, Fastly and so on, if these servers can’t handle the extra traffic, other clients of these providers can also experience denial of service. In the Krebs attack, Akamai were forced to drop the Krebs website to protect other Akamai customers.
DDoS isn’t the only thing that botnets are used for. Another IoT botnet, BCMUPnP, managed to enslave 100,000 home and small office routers most likely with the intent of issuing spam mail. Pumping out spam is also one of the Emotet botnet’s favored tasks these days, along with delivering malware, trojans, and ransomware. Botnets have also been used in financial breaches (GameOver ZeuS), credential stuffing attacks and targeted intrusions.
Also see: Looking into Ransomware as a Service (Project Root) | Behind Enemy Lines
Botnet malware will usually also contain some self-updating and administration functions in order to allow the bot owner to add or remove functionality, communicate with peers, exfiltrate data, change persistence methods and take countermeasures to defeat legacy AV and malware signature detections.
How Do Botnets Work?
Generally, botnets utilize one of two different network architectures, either following a client-server model with communications occurring over protocols like IRC or HTTP or a Peer-to-Peer (P2P) decentralized network model.
In the client-server model, all the bots in the network connect to one or more command and control servers run by the bot master. This model allows for fast and direct communication with the bot clients, but suffers from a structural weakness: all the bots must know the internet address of the C2 servers, and that means law enforcement can easily learn the location of the servers and take them down.
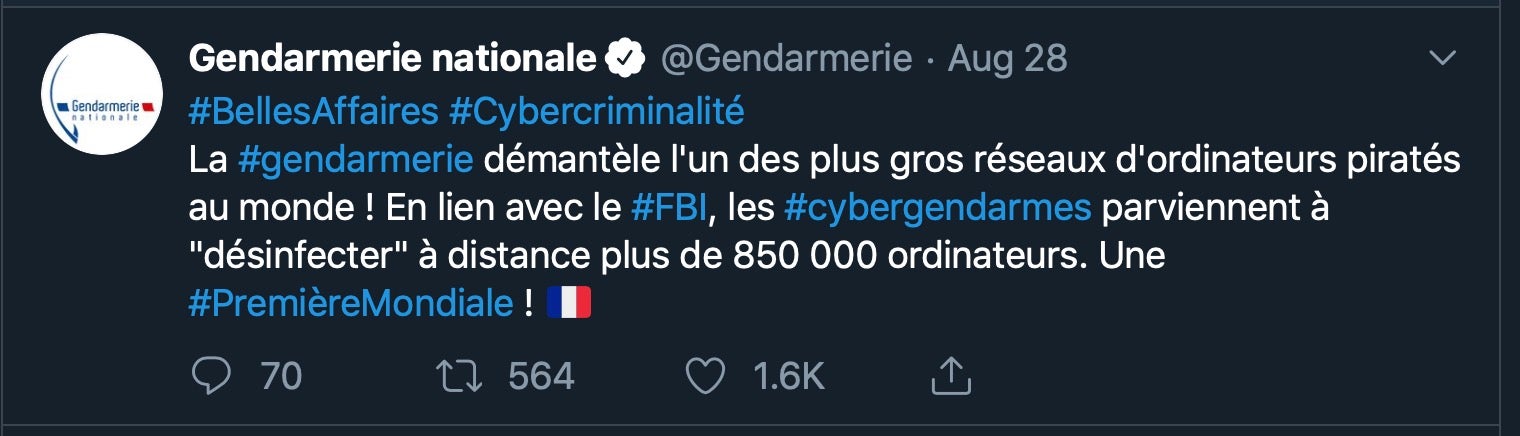
That’s precisely what happened earlier this year when the French police working with the FBI found that the C2 server for the RETADUP botnet, with 850,000 infected computers enslaved, was located in the Ile-de-France region. The authorities gained secret access to the server through the hosting provider and replaced the botnet server’s code with their own. So as not to alert the criminals, the authorities copied the original malicious code but added a secret function that caused all the bots to disinfect themselves as soon as they connected with the C2.
“The gendarmerie has dismantled one of the largest networks of pirated computers in the world! In collaboration with the FBI, French cyber police managed to “disinfect” more than 850,000 computers remotely. A world first!”
Peer-to-Peer offers a more secure architecture from the threat actor’s point of view. This decentralized network set up has been likened to a “terrorist cell” network, where noone in a given cell knows the identity of anyone else in other cells. The cell – a small group of bots – has a known “head” or “node” – in a P2P botnet that’s usually a bot with a public internet address – that other bots in the cell (which perhaps live behind a NAT or firewall) can connect with. Since there is no central command from which to issue instructions, the bot owner issues digitally encrypted commands that are shared among the peers. Encrypted with the owner’s private key, only commands the bot master sends will be decrypted (using the bot master’s public key) and acted on by the bots. This use of asymmetric encryption prevents others from hijacking the bots in the decentralized network.
With patience, it is possible to build up a map of a P2P network and disrupt it. The Joanap botnet, believed to be run by North Korean threat actors, was disrupted in early 2019 after the FBI ran servers that mimicked Joanap peers in a technique known as peer poisoning. This allowed them to collect IP addresses of infected bots and notify the victims and their internet service providers.
How Are Botnets Created?
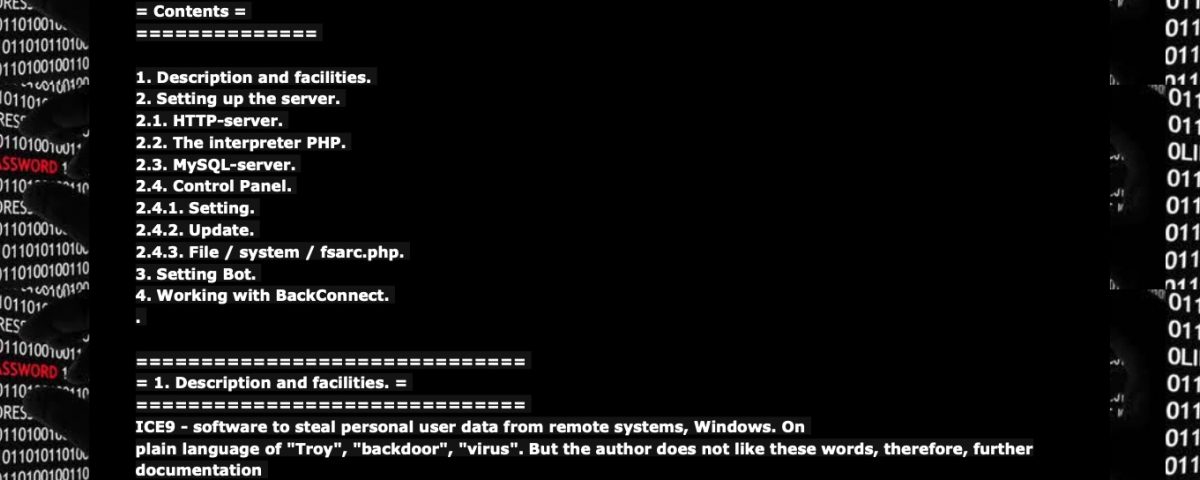
To create a simple C2-style botnet, the bot herder or bot master will need to set up a server to provide the command and control structure. This is usually a web application built on top of a LAMP environment utilizing PHP and MySQL.
Once the backend is set up, the would-be bot master then needs a bot builder. The builder’s primary function is to pack a third component, a malware payload, and embed it with configuration information and the C2s address or addresses.
Kits for creating botnets can be found “for sale” on the dark net or provided in a “Software as a Service” (SaaS) model. ICE9 (Ice IX) and Neutrino are two well-known examples.

Once the package is assembled with a malicious payload, C2 addresses and configuration files, the last step is to distribute the package to victims. Typically, botnet infections take the form of malicious attachments in phishing emails, as this vector is still the most sure of success even today. Another way that a new bot herder can gain initial clients is to buy the services of other, already established, botnets to deliver their payload.
Are Botnets Illegal?
As botnets are just themselves networks of computers, there isn’t anything illegal about creating a botnet of computers you own or have permission to control. Researchers, for example, may be interested in creating their own “botnet labs”. However, it is considered a criminal offence to install malware on a computer belonging to others without their permission. It is also a criminal offence to then direct that computer to conduct other activities if those are illegal, too, so bot herders may face more than one charge if caught by law enforcement agencies.
Mitigating Botnet Attacks
As we have seen, botnets are just networks of computers that are infected with malware. For that reason, the most effective deterrent to botnet infection is a robust behavioral AI security solution that can prevent malware payloads from executing on the device. Firewall control may also be useful for detecting botnet communications across the network.
Conclusion
Due to their ability to coordinate attacks at massive scale, as well as deliver diverse payloads and infect other machines, botnets are a significant threat to individuals, enterprise and government organizations. With botnets now targeting the increasing number of IoT devices flooding both public and private networks, it is essential to ensure that you have EDR protection on endpoints and full visibility into every device on your network.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.