Introducing Batch on GKE–modernizing HPC with Kubernetes in the cloud
November 15, 2019
Leave manual cluster resizing behind with Cloud Dataproc’s autoscaling
November 15, 2019
The Good
Some of the tech industry’s leading names, Intel, Mozilla, Red Hat and Fastly have united to form the ByteCode Alliance. The aim of this new industry partnership is to build on and develop the work of a previous joint project involving Google, Microsoft and, again, Mozilla among others, namely WebAssembly. The new ByteCode Alliance intends to ensure that the WebAssembly ecosystem is put on a sound, security-first footing. The problem they’re hoping to solve is one most organizations will recognize: you either develop or adopt a modular application that in itself passes your security audit, but which has multiple dependencies, importing code from package registries like npm, PyPI and others. Security audits on those dependencies is a herculean if not impossible task, and there’s a real danger of opening the door to supply chain attacks. The ByteCode Alliance wants to ensure that WebAssembly – billed as “the foundations that the future of the internet will be built on” – can provide developers with a reusable set of components that promise to make running untrusted code safer in any environment.
The Bad
Both old and new threat actors have emerged into the limelight this week. First, Lizard Squad popped their reptilian heads out of obscurity with two DDoS attacks on the UK’s Labour Party. Barely active since 2014, when the group claimed responsibility for attacks on North Korea, Sony and even Taylor Swift, Lizard Squad this week said they were behind two DDoS attacks on Labour Party servers. Although unsuccessful at knocking the party’s servers offline, the group – who support Brexit and are avowedly anti-Labour – promised more attacks from a “botnet connected to millions of devices around the world”.
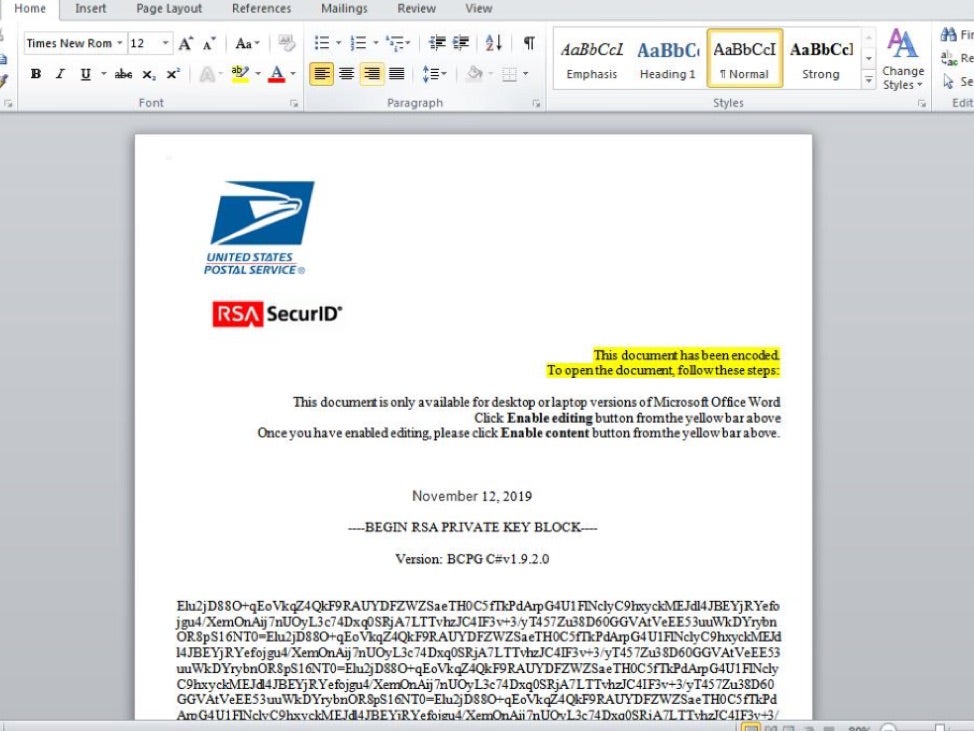
Meanwhile, a previously unknown threat actor has emerged targeting companies in Germany, Italy and the US. Their MO is straight out of Hacking 101: phishing emails carrying poisoned Word documents. The malspam, however, is carefully crafted to look like genuine email from government agencies such as the US Postal Service, the German Federal Ministry of Finance and the Italian Ministry of Taxation. Campaigns seen by researchers during October and November were low-volume and highly targeted. IT services companies, manufacturing and healthcare have been the primary targets to date. Victims that fell for the phishing lure were treated to Maze ransomware, the Cobalt Strike attack kit and the IcedID trojan for payloads.
The Ugly
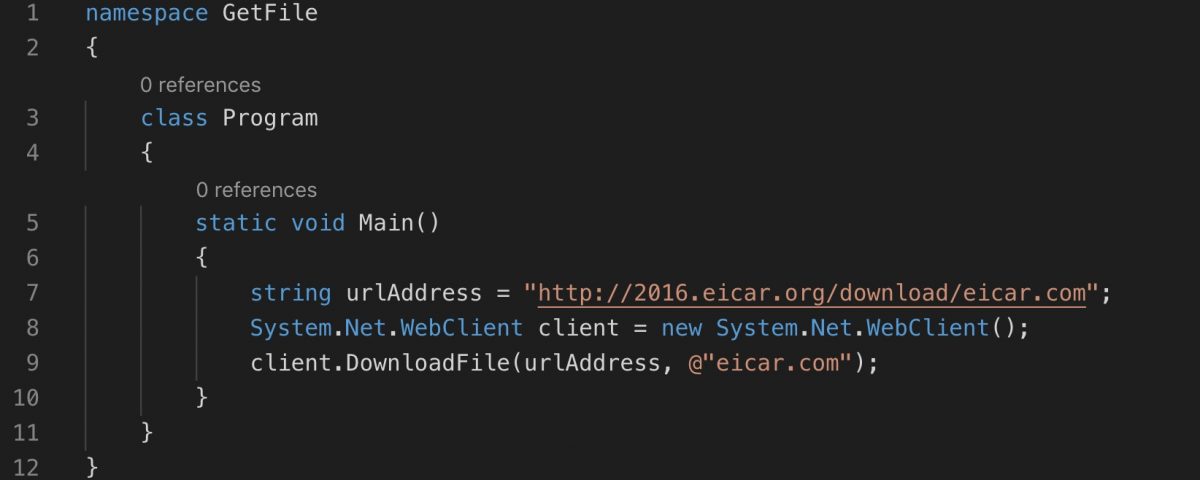
The dangers of a security solution whitelisting privileged processes is one thing, but Windows Defender has taken things to a whole new level of unsafe by simply whitelisting file names. As this POC by Grzegorz Tworek simply and reliably shows, Windows Defender’s real time scanning appears to give a green light to any executable called msiexec.exe. Tworek’s POC couldn’t be simpler. Compile an executable that does nothing other than download the eicar test file, and watch Defender ATP kick in and flag the downloaded file as malicious.
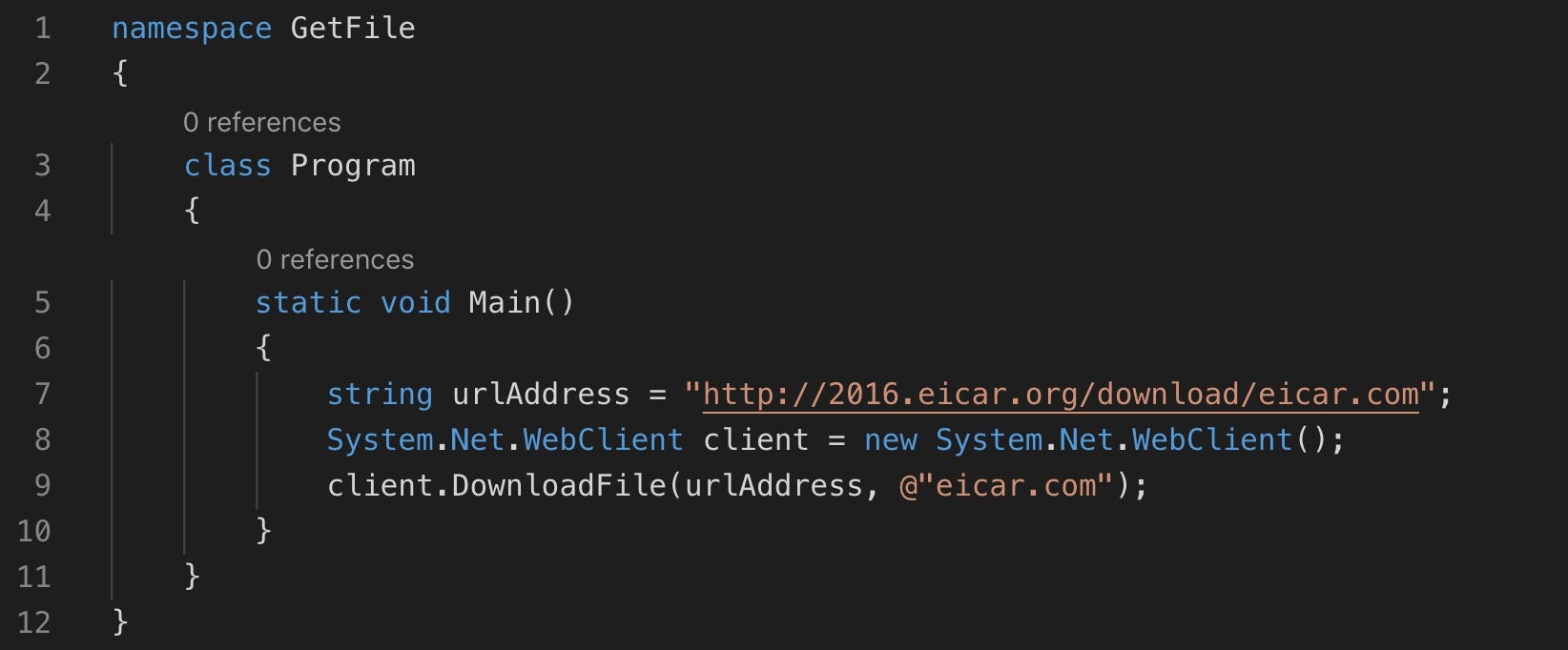
Repeat the experiment but this time compile the code and name the output file msiexec.exe. When you execute it this time, the eicar test file is again downloaded but ignored by Windows Defender. Cybersecurity doesn’t get much uglier than that!
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.