
Upgrade Recommendations and Product Interoperability Checks Now Available in Skyline
October 21, 2019
Bringing Teradata Vantage to Google Cloud
October 22, 2019
 |
Ransomware-as-a-Service (RaaS) offerings have been a staple of the “underground” for many years now. From TOX to SATAN to Petya and beyond, we have seen services continue to appear and thrive. Often times they are short-lived, but that is not always the case. Services like DataKeeper and Ranion have been available for over two years now. These ‘services’ are an attractive way for enterprising criminals to create, distribute, and manage their ransomware (and subsequent profits) with almost no barrier to entry. That is, they require zero prior coding or development knowledge. They also offer instant results and are cheap to launch. Typically, these services either require an “up front” payment or a share of the profits once the victims pay. In this post, we take a journey into the dark web and explore a new RaaS offering that appeared for the first time earlier this month known as ‘Project Root’.

Ransomware As A Service: Meet Project Root
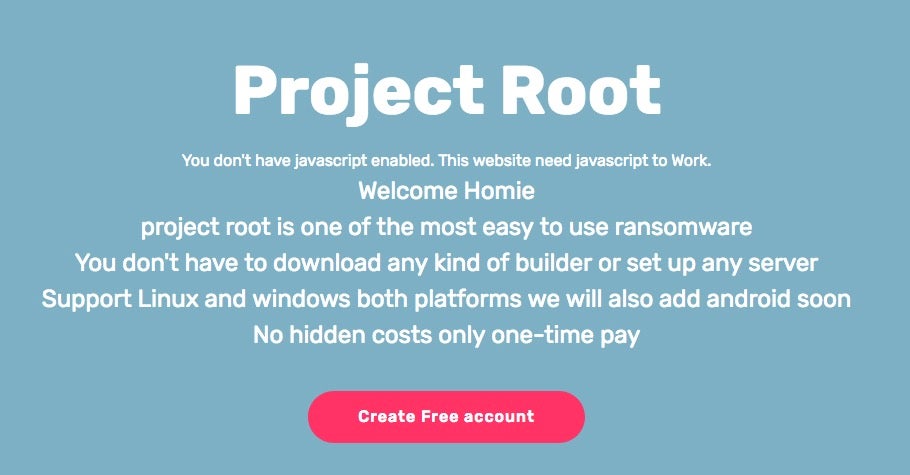
We recently came across a new offering known as ‘Project Root’. This service, like many others, requests a low, “up front” fee to get started. From there, clients can generate ransomware binaries on-demand. Both Windows and Linux are supported (for 32-bit and 64-bit architectures).
Project Root payloads are written in Golang, and thus resemble previous (similar) threat families like LockerGoga. Payloads written in Golang are often able to bypass both traditional signature-based detection as well as some static machine-learning detection engines given how few samples (and therefore extractable features) are found in the wild.
Project Root: How Much Does It Cost?
Project Root is available in two versions. The ‘standard” version (initially) costs $150 USD up front, payable in bitcoin (BTC), and allows for unlimited generation of “basic” payloads via their portal, along with the management and key distribution components. Updates to this version are ‘free’ for 6 months. Over the course of the last two weeks, the standard version price has fluctuated between $50 and ‘Free’. A “Pro” version exists which
allows for better ‘support , longer term of free updates, and increased evasion options. Buyers will also have full access to the source code for increased “customization options”.’

The “Pro” version has been advertised all along but appears to have officially “launched” as of October 17th.

How To Build Ransomware Binaries
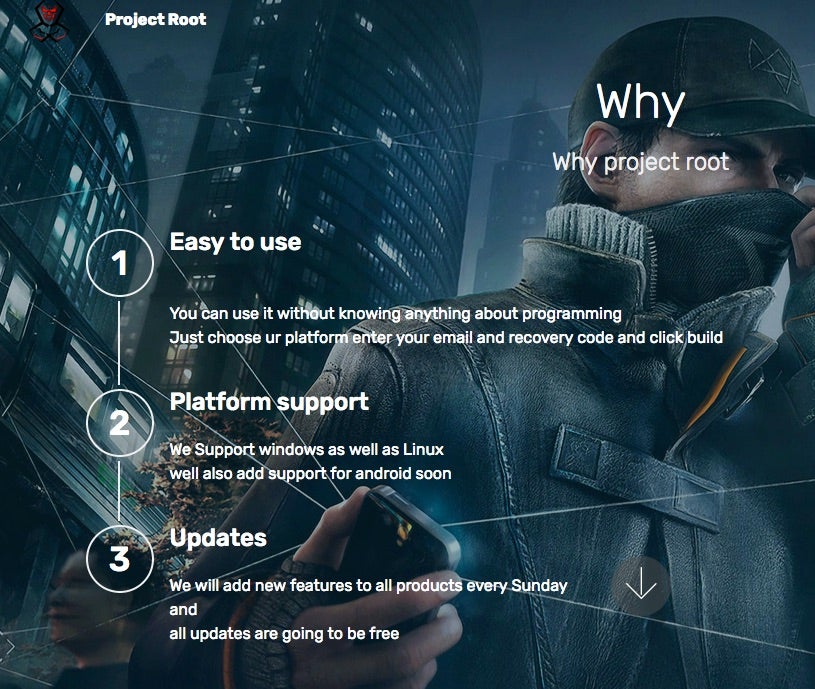
For users of the service, building binaries is very straightforward. The RaaS customers need only specify the desired architecture (x86 or x64) along with the platform (Linux or Windows). It should be noted that an Android version is promised for the future. Along with the above options, the user needs to supply a contact email address for the victim, along with a customized recovery key associated with the campaign.
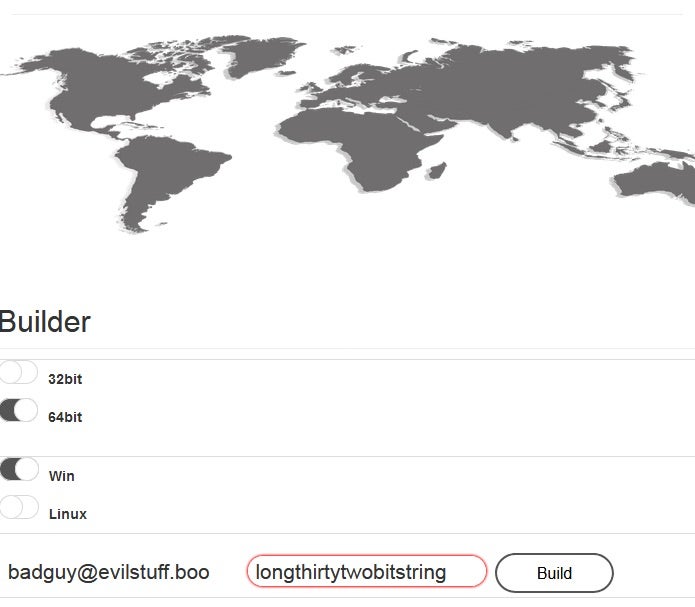
This builder interface is also used to access specific decrypters for either Linux or Windows platforms (also provided in x86 and x64 varieties)
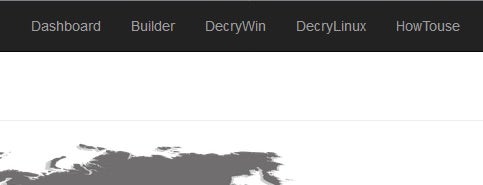
The “How to Use” section also serves as the service’s FAQ section. While seemingly straightforward, it does reveal that the actor behind this is most likely not a native English speaker.
Teething Trouble or Scamming the Scammers?
It is also interesting to note that until recently (on or around October 14th), the ransomware payloads we analyzed did not work. All the samples we investigated prior to October 14th did not proceed past the initial execution phase. No further activity occurs and the victim’s files are not encrypted. This was true across x86 and x64 samples. This is an interesting phenomenon that maybe does not get enough attention. All malware authors have a varying degree of skill, and their ability to ‘QA test’ their creations is equally idiosyncratic. It is possible that, during the early stage of the service’s launch, they were still working out kinks. Despite that, it appears that the service was happy to continue ‘selling stuff” and accepting payments from hopeful criminals.
There is quite a large ‘scam the scammer” market on the ‘Deep Web’ and other dark corners of the threat landscape. There are scammers out there that deliberately target lesser-skilled scammers to make a quick buck. There are many examples of this in recent history (Aspire Crypter and INPIVIX RaaS come to mind). Also, for every ‘legitimate’ service, there are dozens or more clones/phish sites that just serve to mine credentials, account data, and more. Even the relatively well-known ransomware services like DataKeeper, Ranion, and MegaCortex are shadowed by a confusing vortex of copy-cat sites which blur the line between the scammy sites and the legit services.
When we first encountered these executables, and located the corresponding portal for the RaaS service, this was our first thought. However, it turns out, if you are patient enough, sometimes the scams turn out to be ‘real’. Starting around October 14th onwards, the Windows and Linux payloads that we have been able to intercept and analyze are functional, so this does not appear to be an outright scam, which seemed like a distinct possibility early on.
Inside The Ransomware Payload
The generated Ransomware payloads are written in Golang.
Project Root’s payloads follow in the footsteps of other, similar, ransomware families also written in Golang such as LockerGogoa and shifr .
The samples we have analyzed to date are delivered in an unpacked state. Golang binaries tend to be somewhat large (over 1MB) and therefore you often see them mutated or compressed via a packer. Such is not the case with those generated by Project Root, and the size of the analyzed binaries range from 5MB to 6MB.
Functionally, there is nothing ground-breaking or novel about the executables generated via Project Root. Upon execution, the code will perform a few checks in an attempt to evade analysis. The executables are ‘sandbox-aware” and will fail to run in both VMware and Oracle VirtualBox. In addition to the local system/host checks, the ransomware binary will attempt to reach out remotely to verify network connectivity by contacting the following IP address:
ec2-3-18-214-41[.]us-east-2[.]compute[.]amazonaws.com (3[.]18[.]214[.]41).
If successful, the executable will communicate a base64 encoded string to the remote host. The encoded string contains identifiable details of the infected system. This is for tracking as well as infection/payment reporting on the portal side.
![]()
Files are encrypted using AES-256. The samples we have analyzed only appear to target the following 195 specific file types for encryption.
odt, ods, odp, odm, odc, csv, odb, doc, docx, docm, wps, xls, xlsx, xlsm, xlsb, xlk, ppt, pptx, pptm, mdb, accdb, pst, dwg, xf, dxg, wpd, rtf, wb2, mdf, dbf, psd, pdd, pdf, eps, ai, indd, cdr, jpg, jpe, dng, 3fr, srf, sr2, bay, crw, cr2, dcr, kdc, erf, mef, mrwref, nrw, orf, raf, raw, rwl, rw2, r3d, ptx, pef, srw, x3f, der, cer, crt, pem, pfx, p12, p7b, p7c, c, cpp, txt, jpeg, png, gif, mp3, html, css, js, sql, mp4, flv, m3u, py, desc, con, htm, bin, wotreplay, unity3d , big, pak, rgss3a, epk , bik , slm , lbf, sav , lng ttarch2 , mpq, re4, apk, bsa , cab, ltx , forge ,asset , litemod, das , upk, bar, hkx, rofl, DayZProfile, db0, mpqge, vfs0 , mcmeta , m2, lrf , vpp_pc , ff , cfr, snx, lvl , arch00, ntl, fsh, w3x, rim ,psk , tor, vpk , iwd, kf, mlx, fpk , dazip, vtf, 001, esm , blob , dmp, menu, ncf, sid, sis, ztmp, vdf, mcgame, fos, sb, itm , wmo , itm, map, wmo, sb, svg, cas, gho,iso ,rar ,mdbackup , hkdb , hplg, hvpl, icxs, itdb, itl, sidd, sidn, bkf , qic, bkp , bc7 , bc6 ,pkpass, tax, gdb, qdf, t12,t13, ibank, sum, sie, sc2save ,d3dbsp, wmv, avi, wma, m4a, 7z, torrent
Once encryption occurs, affected files are given a .Lulz extension. The desktop background is changed to an image which instructs the victim to refer to ‘Fuck.txt’ for instructions on how to proceed with decryption.
The background image is pulled from the following URL:
hxxps[:]//i.postimg[.]cc/pdbqqS5P/new.jpg

The ransom note simply provides instructions on whom to email for details on decryption along with a corresponding uniquely identifying key. At that point, it is up to the attacker to respond, accept payment, and provide details on how to proceed.
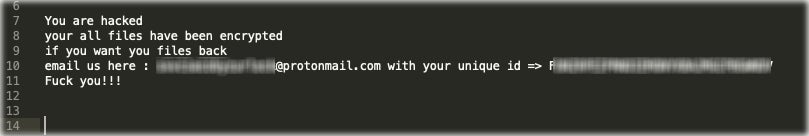
The threat also attempts to clear out local event logs (Windows version), as well as attempts to install a new root certificate. The certificate installation appears to still be problematic as we were unable to reproduce or observe that behavior during our analysis.
Defending Against Project Root and RaaS
SentinelOne Endpoint Protection is capable of fully preventing malicious binaries generated by the Project Root service across platforms. In scenarios where the threat has been able to make malicious changes, those can be fully reversed via SentinelOne’s “Rollback” feature.
Of course, aside from having a strong security solution in place, user education and a well-established Disaster Recovery Plan/Business Continuity Play (DRP/BCP) will go a long way here, too.
Conclusion
It is always good to stay aware and keep up to date with the types of malware and ransomware services that are currently available, as well as the efficacy of them. While there are many that launch as either deliberate scams or are simply poorly written, there are also many that function quite well and present a real threat to users. This service, Project Root, straddles the line between those two extremes.
Indicators of Compromise (IOCs):
| ade0d7fbdcb34d7cbd220beb9c3c2484f7ce05c11043bd5ed64df239f5039ba7 | Ransomware sample (x86) |
| 930b10c9413156bc91aafd0d3dd88e927b1c938707349070b35d2700a1b37f2f | Ransomware sample (x64) |
| 432ebc85724f52ff1bbe205b22c68c15675a0f03321a9abae04c87415f10fa37 | Ransomware sample (Linux) |
| 576ce4198bd883a01f50535588109a0a78b5af2ce3a1ee69842a34b237bfeed5 | Decryption Tool (x86) |
| 7292dd52392e36826a48f15be0e185a4d34a4716e4bed8e77704fb1c05aa8b48 | Decryption Tool (x64) |
| 70c518fd0bf8ba099b9e87c951e2b72f79a637334e981140f7e0d0616d0c6905 | Decryption Tool (Linux x86) |
| ff4b1f56244d0887d3fbc62956b742cb4b43048c92f68f4aa09bb54b8a415d12 | Decryption Tool (Linux x64) |
| h t t ps[:]//i.postimg[.]cc/pdbqqS5P/new.jpg | Network / HTTP Request |
| prootk6nzgp7amie[.]onion | RaaS Portal (TOR) |
| ec2-3-18-214-41.us-east-2.compute.amazonaws.com | RaaS Portal Mirror (Clearnet) |
| 6dd74824ce2f34df13ccba4b6567b00bfdf42daeecc9a12196eee4c8ade29224 | Ransomware sample (x64) |
| b226c3b4d8634f9ede3d526c5ee287287c20cf7173154c4db64ec5235800ddcd | Ransomware sample (x86) |
MITRE ATT&CK
- T1130 – Install Root Certificate
- T1486 – Data Encrypted for Impact (Ransomware)
- T1089 – Disabling Security Tools
- T1497 – Virtualization/Sandbox Evasion
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.





