|

The Good
There was good news this week for everyone concerned about the widening cybersecurity skills shortage. Thanks to an expansion in the US Department of Labor’s industry-recognized apprenticeship programs (IRAPs) and an extra $183.8 million in funding, 23 higher ed institutions and groups along with their private-sector partners will receive support to provide 85,000 apprenticeships across several fields, including information technology. On the back of that, Florida International University have announced Cyber-CAP, a program that will train 800 cybersecurity apprentices over a period of four years.

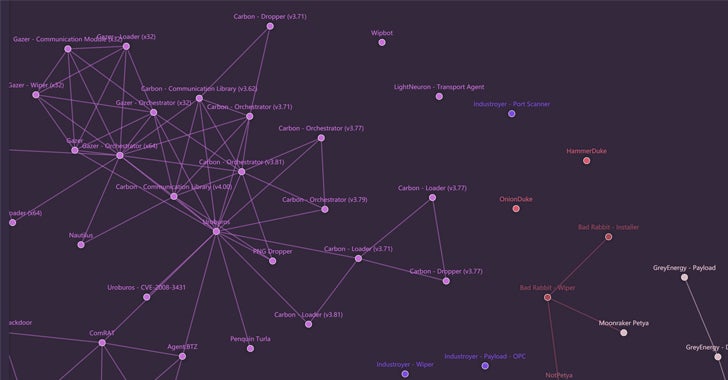
This week also saw release of a new public tool that should be of interest to threat researchers concerned with Russian APT groups. The sheer number and diversity of Russian-backed hacking groups with shared tooling has always presented an additional obstacle to attribution. Now, a new web-based interactive map can be used by anyone wishing to learn more about the connections between various groups, tools and campaigns. The map currently tracks 2000 malware samples and some 22000 connections between them.
The Bad
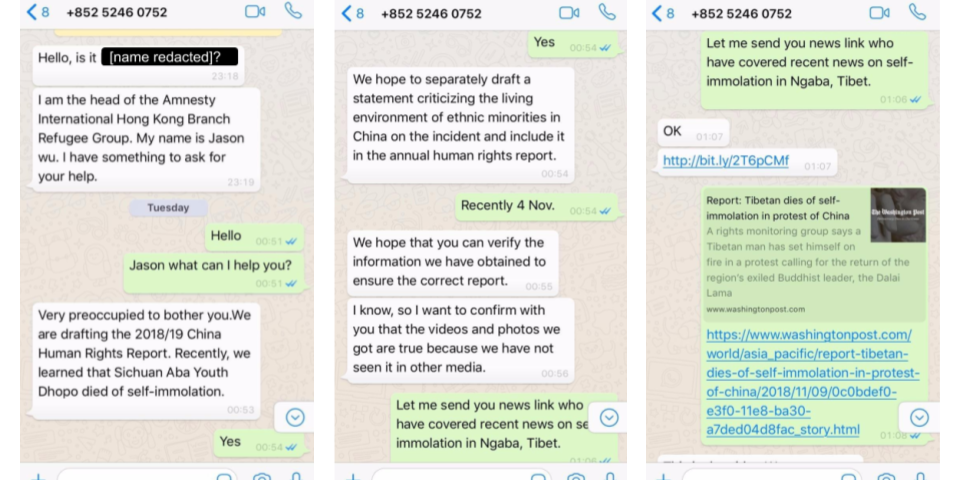
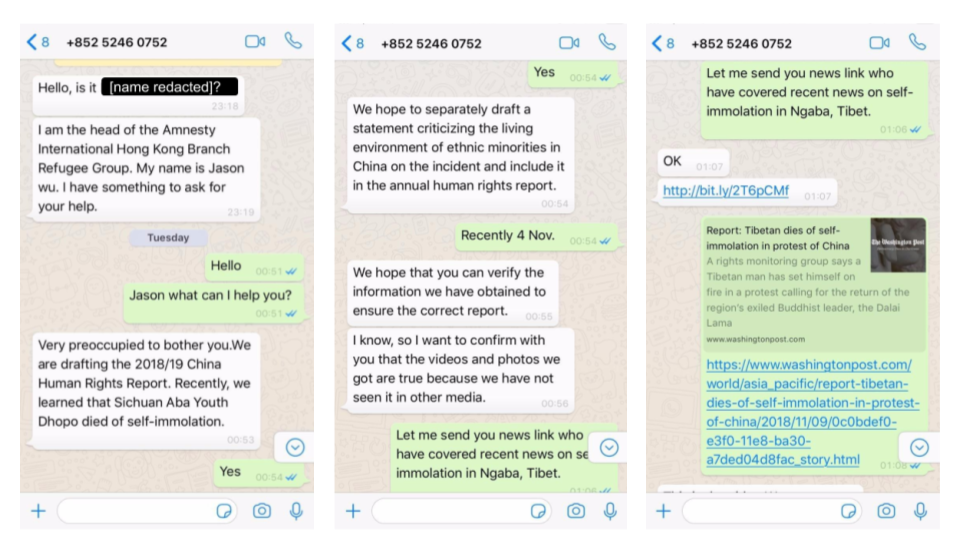
A sophisticated and targeted campaign using one-click mobile exploits was revealed this week by researchers in collaboration with the Tibetan Computer Emergency Readiness Team (TibCERT). The campaign involved sending malicious WhatsApp messages to members of Tibetan groups using both Android and iOS devices. Although the exploits involved publicly-known vulnerabilities rather than exploiting any new zero days, the researchers were able to link the threat actor to an earlier campaign that targeted the Uyghur ethnic minority. That points the finger at a likely Chinese-backed APT group. Activists in Hong Kong take note.
The Ugly
Phishing remains the number one vector of compromise, so it’s unfortunate to see yet more open redirects become available for attackers to exploit. In a thread entitled Here’s a phishing URL to give you nightmares…, Reddit user wanderingbilby explained how he stumbled over an adobe.com domain being used to redirect the unwary to a compromised WordPress site hosted on Microsoft’s windows.net. The trick is easy to pull off. Add whatever (legitimate!) domain you like in place of <target domain> in this one and Adobe will kindly redirect it for you.
https://t-info.mail.adobe.com/r/?id=hc43f43t4a,afd67070,affc7349&p1=<target domain>
It’s hardly a new vector: as other Reddit commentators were quick to point out, spammers have been seen exploiting open redirects via LinkedIn, Google and many other domains for some time. What it does highlight is that simply training your users to examine the primary domain in a link is neither a reliable nor sufficient method of protection.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.