Context-aware access allows you to define and enforce granular access policies for apps and infrastructure based on a user’s identity and the context of their request. This can help strengthen your organization’s security posture while giving users an easier way to access apps or infrastructure resources without using a VPN client, from virtually any device, anywhere.
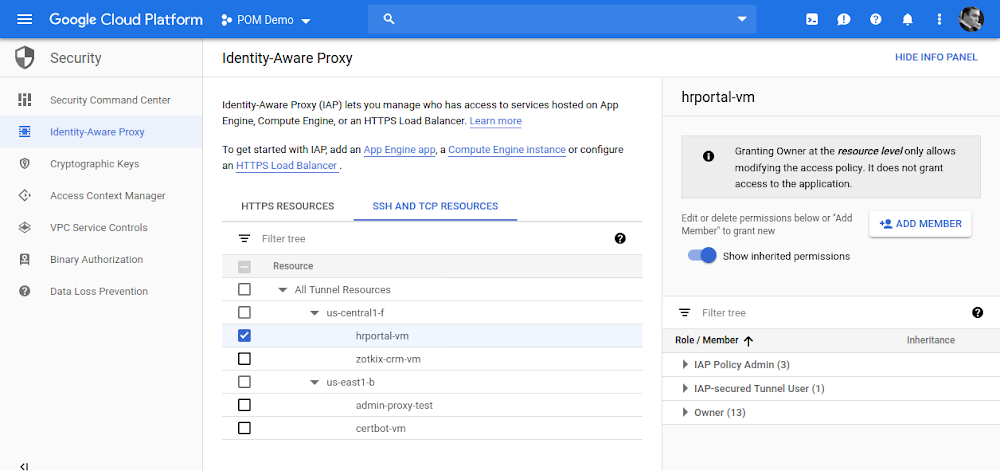
With the general availability of context-aware access in Cloud IAP for SSH and RDP, you can now control access to VMs based on a user’s identity and context (e.g. device security status, location, etc). In addition, VMs protected by Cloud IAP don’t require any changes and no separate infrastructure deployment–simply configure IAP and access to your VM instance is automatically protected with a planet-scale load balancer, complete with DDoS protection, TLS termination, and context-aware access controls.
One of our partners, Palo Alto Networks, has been using this capability to protect access to their cloud workloads. “Customers trust us with their data, so keeping it secure is our number one goal,” says Karan Gupta, SVP, Application Framework. “Context-aware access in combination with Palo Alto Networks endpoint protection enables us to control access to our infrastructure deployed in GCP following zero trust principles, helping to secure our public cloud workloads while making our work easier and keeping our costs low.”
Imagine you want to allow SSH access to VMs for a group of users in GCP. You can use Cloud IAP to enable access without exposing any services directly to the Internet simply by configuring its TCP forwarding feature.