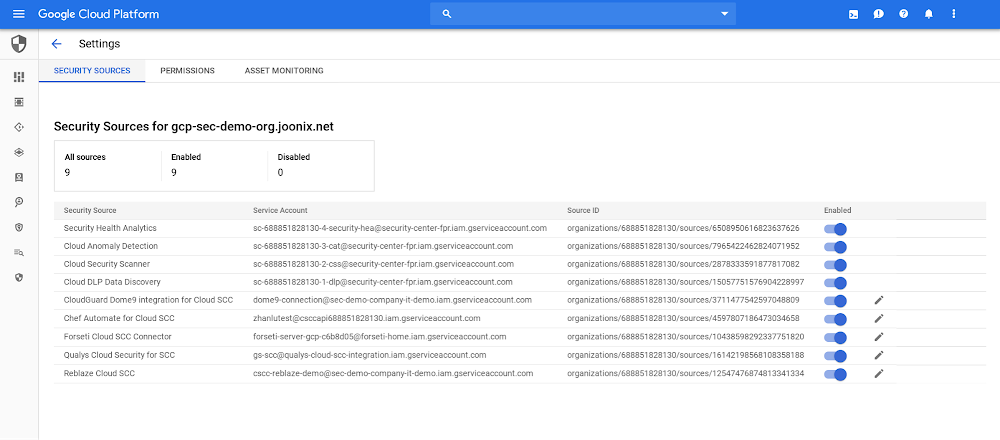
As the number of platforms you build and run your applications on increases, so does the challenge of understanding what applications you have deployed and their security state. Without visibility, it can be difficult to know if there are any latent vulnerabilities in your applications–much less how to fix them.
Today, we’re excited to announce the general availability of Cloud Security Scanner for Google Kubernetes Engine (GKE) and Compute Engine, joining Cloud Security Scanner for App Engine. Now, no matter where you run your applications on Google Cloud, you can quickly gain insights into your web app’s vulnerabilities and take action before a bad actor can exploit them.
Web application vulnerabilities can occur during the development process. Some of these vulnerabilities include the incorrect setup of an app’s security framework, the incorrect implementation of an app into a production environment, or systems that weren’t patched or updated.
Cloud Security Scanner can surface a wide range of web application vulnerabilities as findings; here are a few examples of its capabilities:
- Identity and notify you of common external vulnerabilities in your applications such as Flash Injection or mixed content
- Detect vulnerabilities such as cross-site scripting bugs due to JavaScript breakage
- Alert you of accessible GIT and SVN repositories
- Surface mixed content vulnerabilities that a man-in-the-middle attacker could exploit to gain full access to the website that loads the resource or monitor users’ actions.
- Notify you if an application appears to be transmitting a password field in plain text, displaying HTTP header issues, including misspellings, mismatching values in a duplicate security header, or invalid headers