Least privilege for Cloud Functions using Cloud IAM
July 26, 2019
Understand GCP Organization resource hierarchies with Forseti Visualizer
July 26, 2019
The Good
The NSA, which has something of a reputation for offensive security practices, is to launch a defensive division called the Cybersecurity Directorate on October 1st. Its mission will be to focus on protecting the US against foreign cyber threats and involve collaborating with other US government departments such as US Cyber Command, the FBI and Homeland Security. There’s also a stated promise that the new Directorate will share information “with our customers so they are equipped to defend against malicious cyber activity”. Wondering just who the NSA’s customers are? That’d be the Five Eyes partners and other government departments, including the President. It’ll be interesting to see if the new Directorate takes a similar approach to US Cyber Command and shares some of that intel with the public and the rest of the security industry.
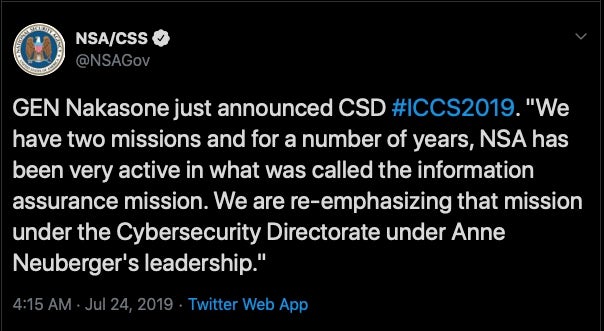
However, don’t let the new emphasis on defense fool anyone into thinking the NSA are getting all warm and fluffy. After making the announcement, NSA director General Nakasone implicitly warned any potential foreign enemies that “The American public should rest assured that there will be consequences for taking the US on.”
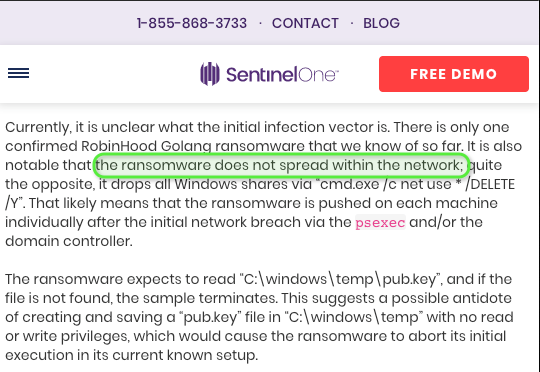
More good news for the NSA this week as confirmation of news @VK_Intel first broke on this blog back on May 9th came in that their (ahem…the) Eternalblue toolkit was not in fact involved in the Baltimore ransomware incident. City of Baltimore Mayor Bernard C. “Jack” Young confirmed the ransomware attack they experienced (Robinhood ransomware) was not caused by BlueKeep nor Eternalblue.
The Bad
Another day, another data breach…it’s not uncommon to hear of data breaches these days that leak millions of user records, so the estimated 5 million people affected by a breach of the Bulgarian tax office might not seem like big news until you factor in that Bulgaria’s total population is only around 7 million people. That pretty much means every tax paying adult in the country has been affected, and reports indicate the data is already circulating online. Things may get worse for the Bulgarian government, too. Since the nation is a member of the EU and enforces GDPR data laws, it may end up having to fine itself for breach of its own cyber security regulations. Leaking the personal data of your entire adult population seems to bring new meaning to the term “nation state hacking”.
The Internet of Things (Iot) has been in the news again this week, and that rarely bodes well for security. A Brazillian botnet of 400,000 infected IoT devices has been conducting a massive DDoS campaign over 13 days against an entertainment service provider. Meanwhile, ICANN and IBM have separately warned that the massive growth of IoT devices using DNS to locate remote services could put serious stress on DNS infrastructure and result in unintentional DDoS attacks. What might happen, for example, if hundreds of thousands of devices simultaneously run DNS lookups as they try to download an automatic software update? The reports also sound the alarm over the potential for cloud-connected IoT devices to serve as an infection vector to deliver malware to corporate cloud servers.
The Ugly
It had to happen sooner or later: someone’s dropped a working exploit for BlueKeep. No, we don’t mean the Chinese language slides that surfaced last week. US government contractor Immunity have developed a working exploit and included it in their penetration testing suite, Canvas. The move has divided researchers, with some arguing it’s best that defenders can test their networks knowing that there’s bound to be some actors that have already developed private exploits, and others suggesting that publishing a working exploit will unleash a “WannaCry” style storm. For the time being, Immunity’s exploit is closed source and only available to their customers. Watch this space!
Bugs! Nobody likes them and we all love to see them squashed, but if there’s one thing worse than a bug that you have to patch it’s a patch that introduces a showstopping bug. Some Apple Mac users still running macOS 10.13 High Sierra are reporting kernel panics when their Macs sleep after applying the latest security update from the Cupertino outfit. Apple have since removed the update from their software catalog, but that’s cold comfort for those that have followed security best practice to “update early, update often”.
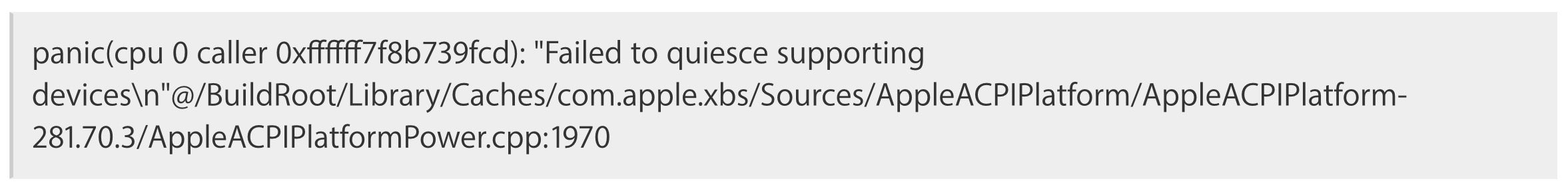
Even after reverting the system via a snapshot, it appears the issue remains, which suggests the update may have patched the device firmware (technically, the culprit is suspected to be a patch to the T1/T2 chip and appears not to affect models without it). Nothing to be done except wait for Apple to release a fix.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.