This year’s uptick in new ransomware attacks continues with the emergence of the MegaCortex malware, first seen in May and engaging in targeted attacks on corporate networks throughout June and July 2019. Although the infection vector isn’t known at this time, it is likely spread through phishing emails, poisoned attachments or trojan installers. Analysis shows that MegaCortex makes a deliberate attempt to avoid both enterprise security solutions and specific business management software products and delivers a particularly unpleasant ransom note on top. In this post, we dig in to the MegaCortex ransomware and take it for a test drive on one of our endpoints.

Background to MegaCortex Ransomware
MegaCortex ransomware continues the recent trend of targeted ransomware specifically looking to compromise and extort money from enterprise victims.
The ransom demand starts out at 2-3 BTC, which at today’s prices represents somewhere in the region of US $20,000 – $30,000. The attackers warn that the demand could rise to as much as 600 BTC (about US $6 million), presumably if the victim tries to hold off paying or if the attackers think the victim can be coerced into paying so much.
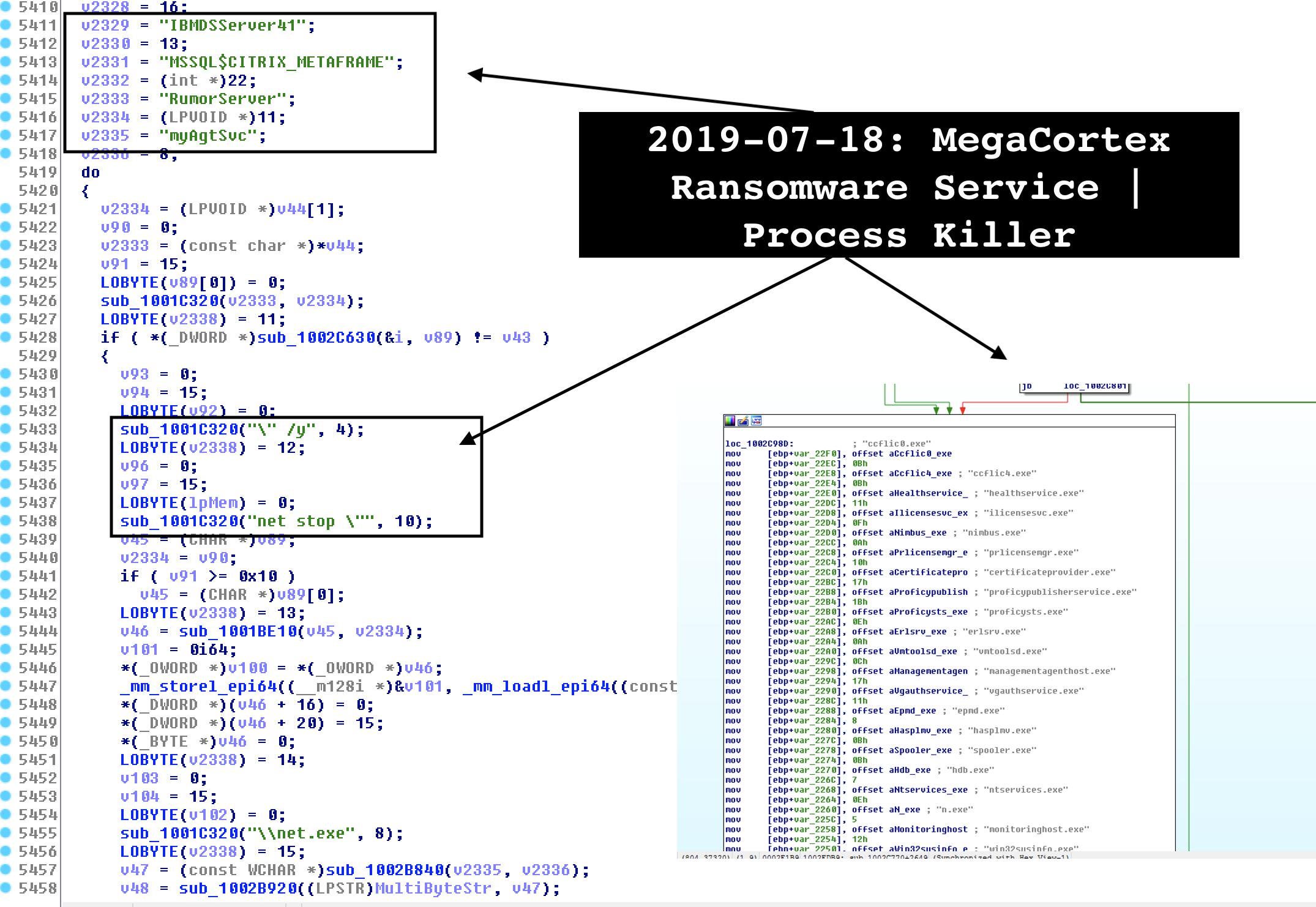
Analysis by researcher Vitali Kremez shows that MegaCortex has some interesting functions, including a process killer that targets a number of enterprise level programs such as the Proficy Suite Operations Management software and Gemalto digital identity services.
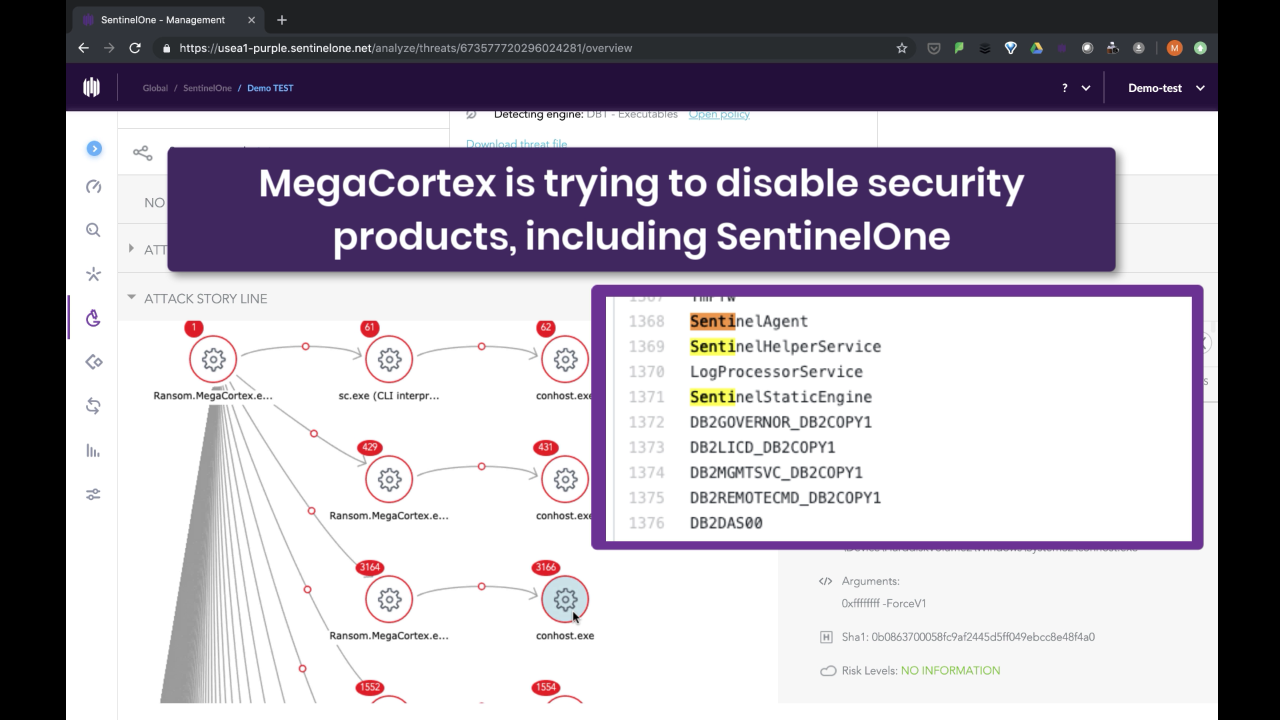
The MegaCortex ransomware also attempts to take a pot-shot at a number of SentinelOne processes, although as we will see below, the agent’s anti-tampering protection makes MegaCortex’s attempt to kill the SentinelOne processes quite unsuccessful.
Who is Behind MegaCortex Malware?
In order to get past basic security measures, the authors’ of the sample we obtained signed the file with a digital signature.
77ee63e36a52b5810d3a31e619ec2b8f5794450b563e95e4b446d5d3db4453b2
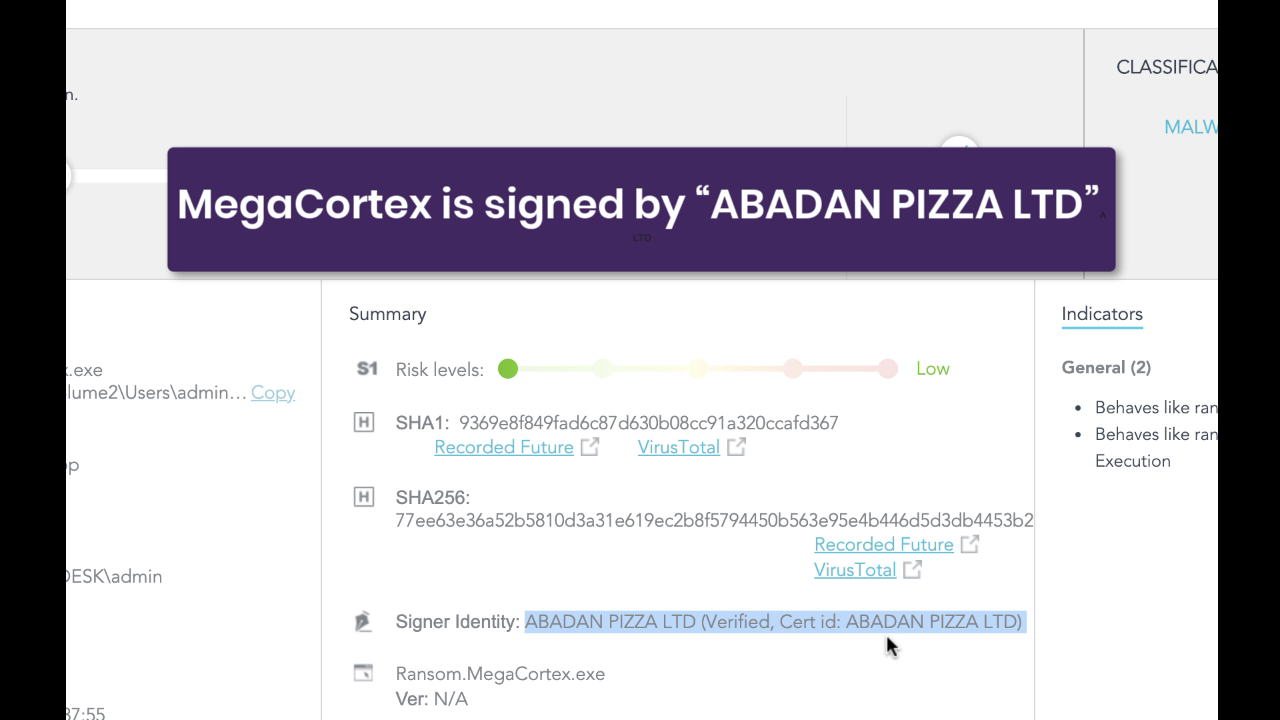
The sample was compiled on the 15th July, 2019, two days before appearing on VirusTotal, and bears a Thawte CA certificate, signed with the name “ABADAN PIZZA LTD”. The product is named “Pizza Napoletana”, described as a “Helper Library” (as we’ll see when we discuss the ransom note below, the authors’ appear to be quite the jesters…).
Abadan Pizza Ltd turns out to be the name of a UK registered company. It was originally registered, along with a number of other food-related businesses, to an address at 13, Mary Street in Sunderland, North East, England on May 3rd, 2017.

Five days later it changed its registered office to another small business address in Chester Road of the same city (pictured below) before changing it back to its original address in Mary Street in January of 2019. Although there are Italian restaurants in both locations, there doesn’t appear to be an actual shop front with the name ‘Abadan Pizza’ in either street at the time Google Maps drove by. Perhaps they moved into Gentlemen’s hairdressing, though, as there does appear to be an ‘Abadan Barbers’ shop at the second of the two registered addresses
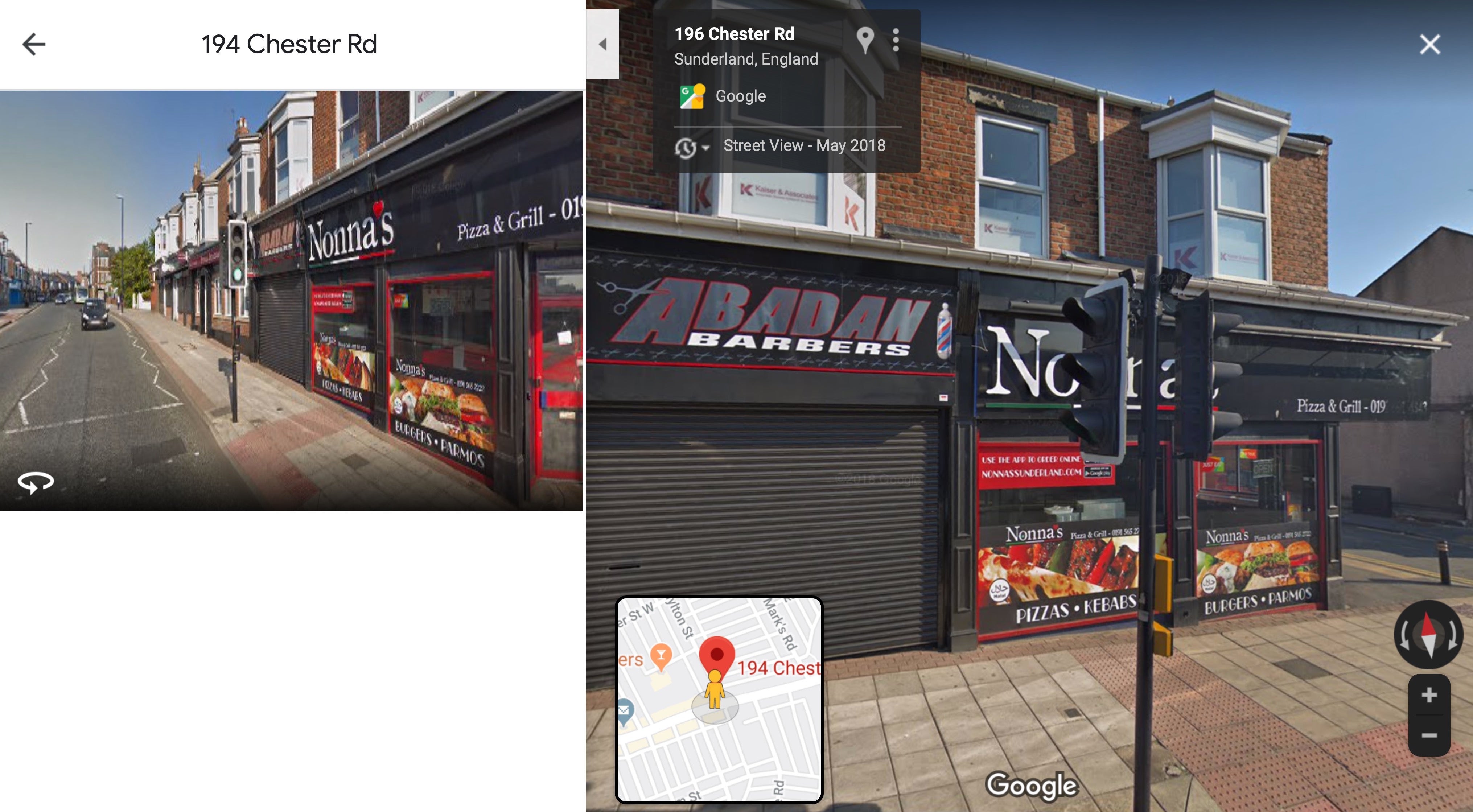
Of course, the link between the name of the business and the name used to sign the malware is likely entirely coincidental and we have no evidence to suggest that the business owners have any knowledge or involvement with the MegaCortex malware. More than likely, they are random victims of the malware authors’ odd sense of humor. It remains an interesting speculation, though, as to whether the malware authors’ picked the name out of a random internet search from halfway across the world or whether the malware authors are or were at some time located in the vicinity of the Abadan Pizza company’s registered addresses.
We Don’t Work For Food!
As we’ve noted, the amount of ransom demanded is clearly aimed at enterprise customers, but MegaCortex’s ransom note also displays an unusual amount of unnecessary grandstanding. Rather than just getting down to business and ensuring the victim has clear incentives and instructions to pay like malware strains such as RobinHood ransomware do, MegaCortex chooses instead to first taunt and then mock its victims, explaining that – candidly, if callously enough – any appeals to the criminals’ better nature would be a waste of everyone’s time. Perhaps playing on the name of their adopted code signatory, Abadan Pizza, the ransom note mockingly tells the victim that they “don’t work for food”.
Remember ! We don’t work for food.
You have to pay for decryption in Bitcoins (BTC).
If you think you pay $500 and you’ll get the decryptor, you are 50 million light years away from reality ?
If you don’t have the money don’t even write to us.
We don’t do charity !
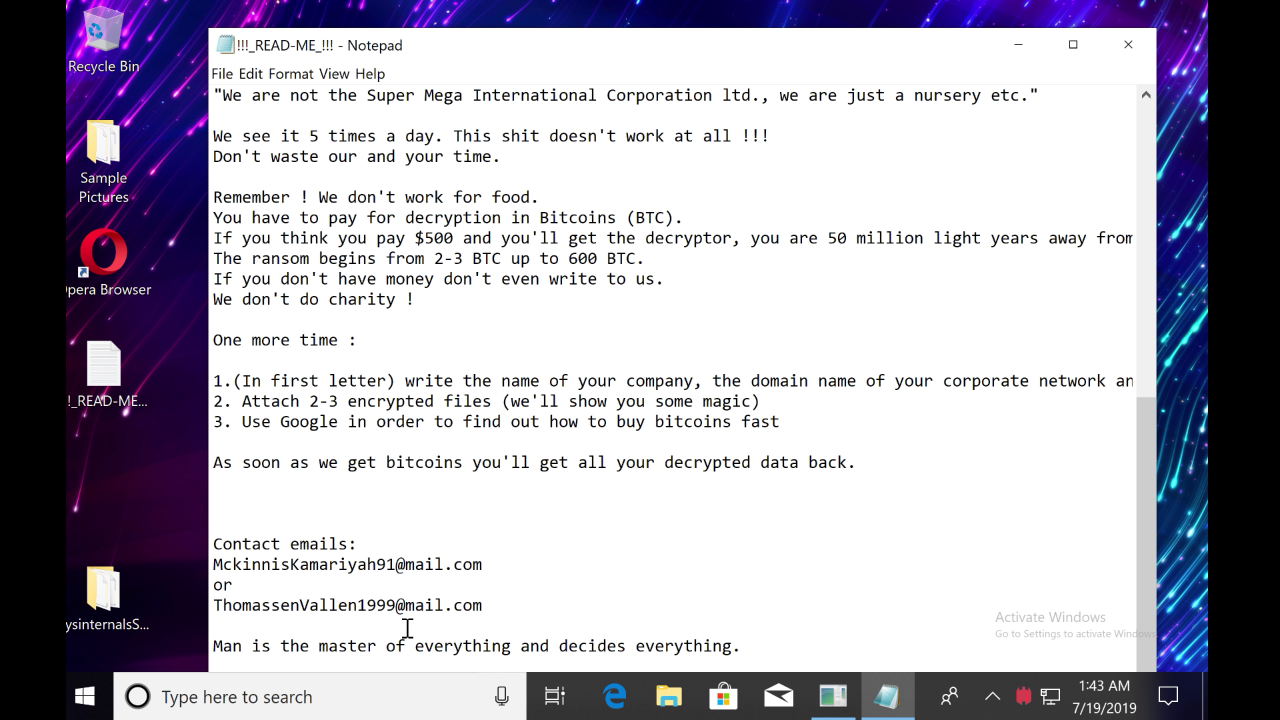
The developers of MegaCortex demonstrate a clear understanding of business software suites and knowledge of enterprise security solutions. This suggests that the actors are not as immature as the language in the ransom note may be trying to suggest. The grammar errors in the ransom note also look somewhat artificial and inconsistent with the overall level of linguistic competency on display.
Demonstration of MegaCortex Ransomware
Let’s take a look at what happens on a victim’s machine when infected with MegaCortex. We’ll set the policy of the SentinelOne agent to “Detect only” so that we can observe the malware in action. Typically, however, enterprise customers would use the ‘Protect’ policy in a real deployment, which would not just detect the malware but also block its execution.
With the policy set to allow MegaCortex to run, we first see on the agent side that the ransomware begins scanning for files to infect.
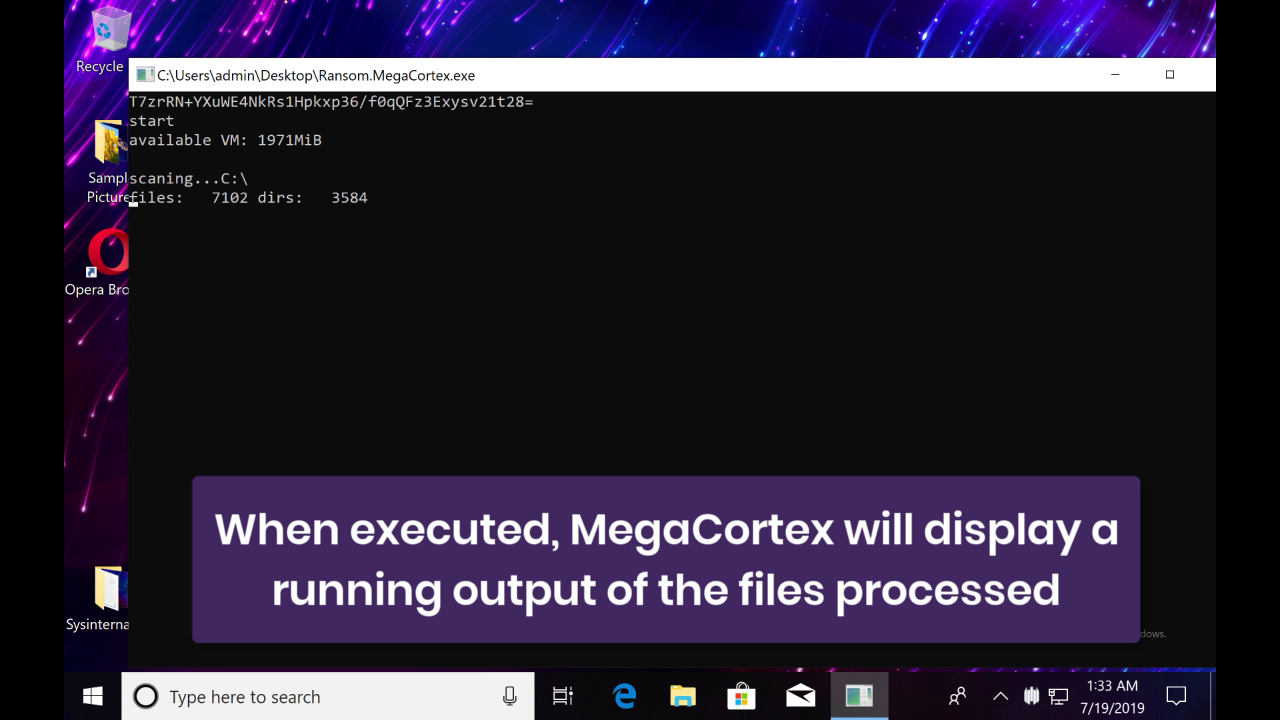
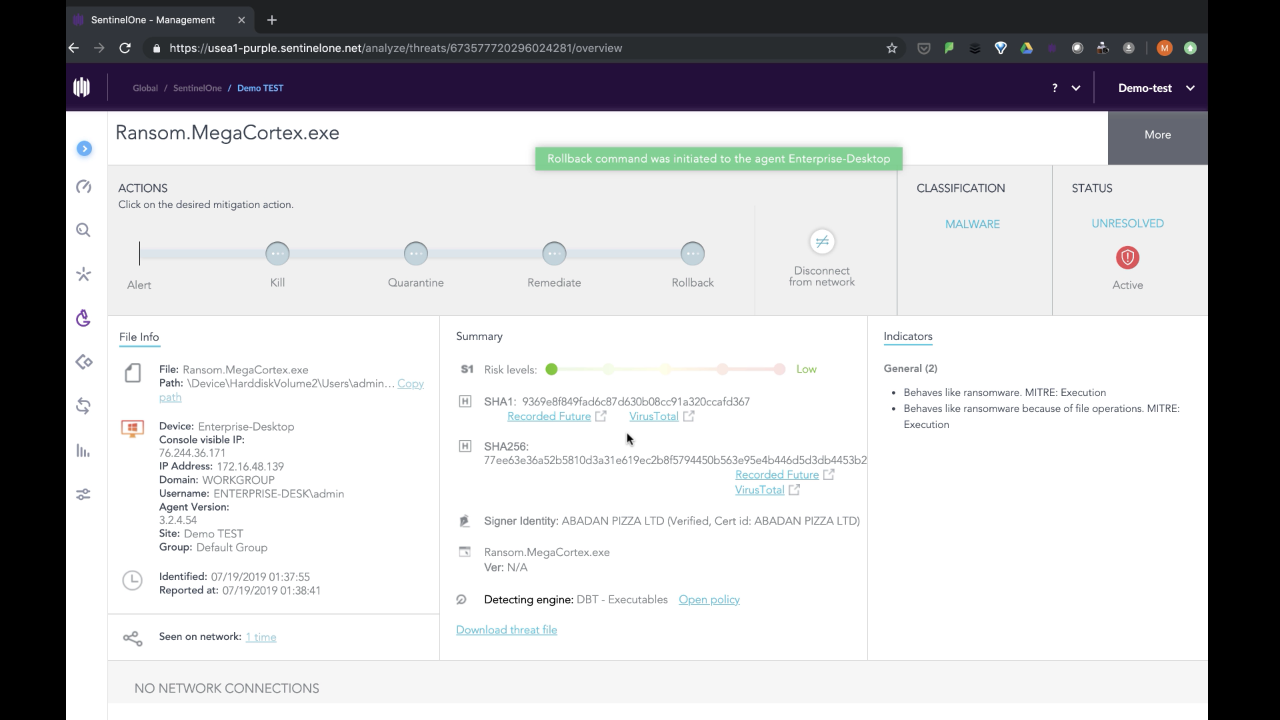
At this point, the SentinelOne agent, which the malware failed to evade, is detected by the behavioral engine.
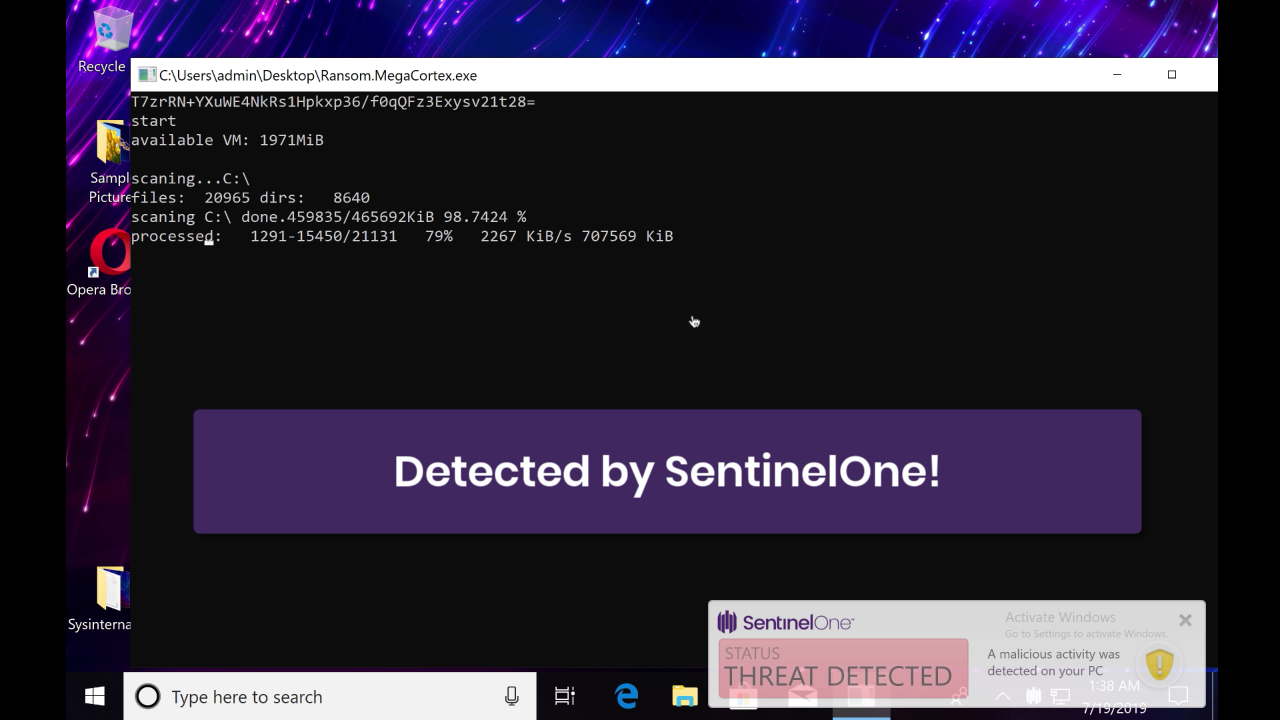
From the administrator’s or SOC analyst’s point of view, the SentinelOne management console alerts on the threat in the Dashboard. Looking at the analysis, the precise reason for the detection is given.
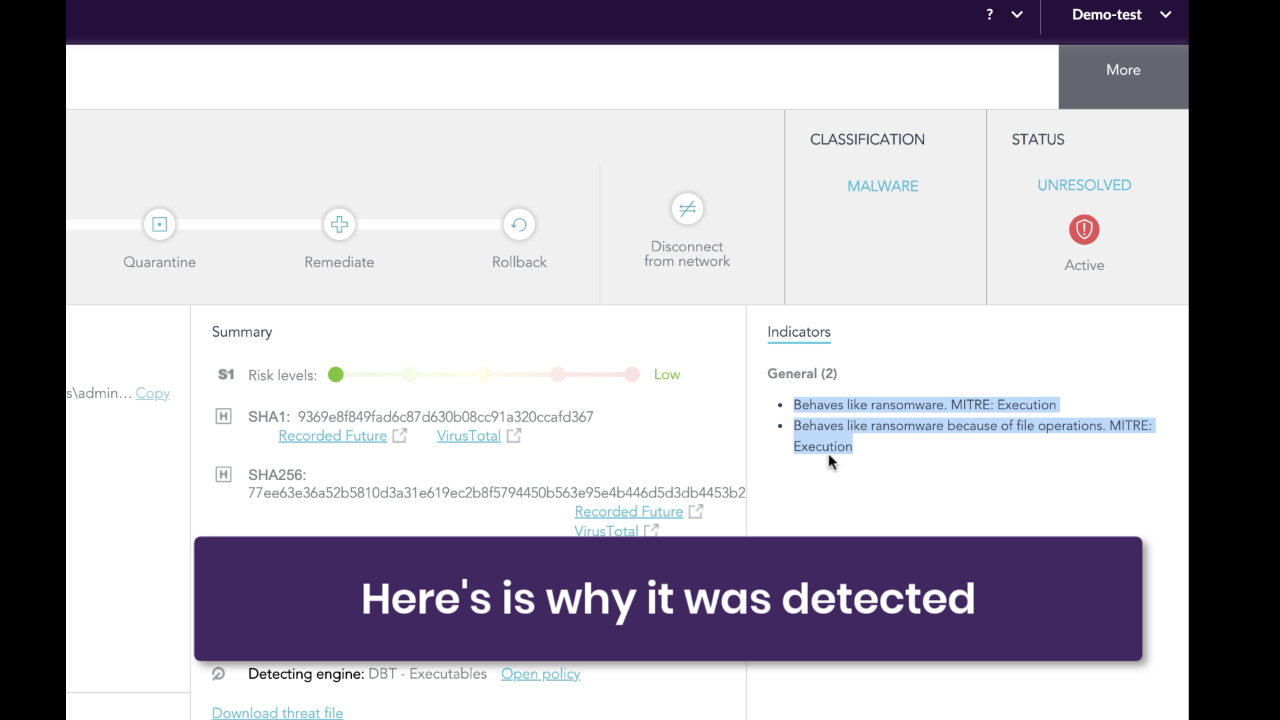
The attack story line also reveals MegaCortex’s failed attempt to circumvent the SentinelOne agent.
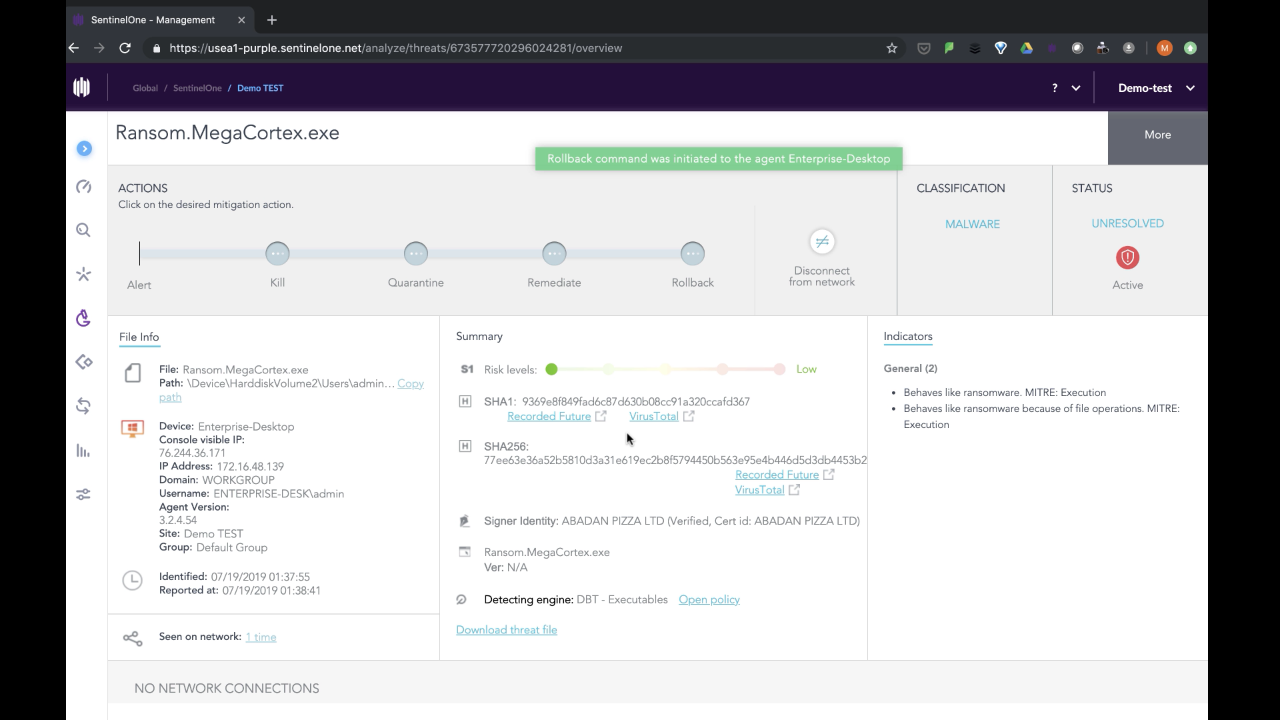
At this point on the agent side, since we were using the Detect-only policy, the user’s files have been encrypted by the malware. However, now that we’ve seen enough of MegaCortex, it’s time to remediate the machine. One click rolls back the infection and returns all the user’s files to their unencrypted state.
If you’d like to see the full demo in action, check out the video below.
Conclusion
Criminals motivated primarily by financial gain have returned to ransomware as their go-to choice of malware in 2019 as a result of both a resurgence in the value of Bitcoin and the decline of easy-money from cryptomining after the closure of Coinhive. This is a trend we expect to see continue throughout 2019 as ransomware attacks have proven devastatingly successful where enterprises are not protected by a comprehensive security solution like SentinelOne. If you’re not already protected by SentinelOne, now is a great time to try a free demo to see how our autonomous endpoint detection and response solution can keep your business safe.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.