Last month today: GCP in June ’19
July 2, 2019
To run or not to run a database on Kubernetes: What to consider
July 3, 2019An active EDR solution will protect your network and endpoints against most threats, but no one can claim a security solution is 100% guaranteed to stop every attack. A determined hacker or threat actor that specifically targets an organization will usually have spent considerable time doing research and reconaissance into a potential target. Malware developed by APTs, which has a habit of leaking into the world of cyber criminals, not to mention zero days stockpiled and sold on to unknown actors by private security outfits, can also be used in an attempt to evade modern security software.
A good security posture, therefore, requires defenders to be vigilant and to use a layered defense model. In a defense-in-depth approach, one such layer is threat hunting. If your security team isn’t already actively searching for threats, read on to learn about the essentials of threat hunting and how it can supplement your organization’s security strategy.

What is Cyber Threat Hunting?
Threat hunting can be defined as a practice designed to help you find adversaries hiding in your network before they can execute an attack or fulfil their goals. Unlike most security strategies, threat hunting is a proactive technique that combines the data and capabilities of an advanced security solution with the strong analytical and technical skills of an individual or team of threat hunting professionals.
Threat hunting is quite a different activity from either incident response or digital forensics. The purpose of DF/IR methodologies is to determine what actually happened after a breach has already come to light. In contrast, when a team engages in threat hunting, the aim is to search for attacks that may have already slipped through your defensive layers.
Threat hunting also differs from penetration testing and vulnerability assessment, too. These attempt to simulate an attack from the outside, whereas threat hunters work from the premise that an attacker is already in the network and then try to look for indicators of compromise, lateral movement and other tell-tale artifacts that may provide evidence of attack behaviour.
What Do You Need to Start Threat Hunting?
As we’ve seen, threat hunting is all about aggressively seeking out hidden IOCs and covert behavior by assuming a breach has occurred, and then searching for anomalous activity. To do that, analysts must separate the unusual from the usual, filtering out the noise of everyday traffic in search of as yet-unknown activity.
Doing that effectively begins with comprehensive visibility into your network, along with rich data from your endpoints. Device telemetry should include things like encrypted traffic, file hashes, system and event logs as well as data on user behavior, denied connections trapped by firewall controls and peripheral device activity. Ideally, you want tools that allow a clear overview of all this data with powerful search capabilities that can contextualize what you see to minimize the amount of manual sifting through raw logs.
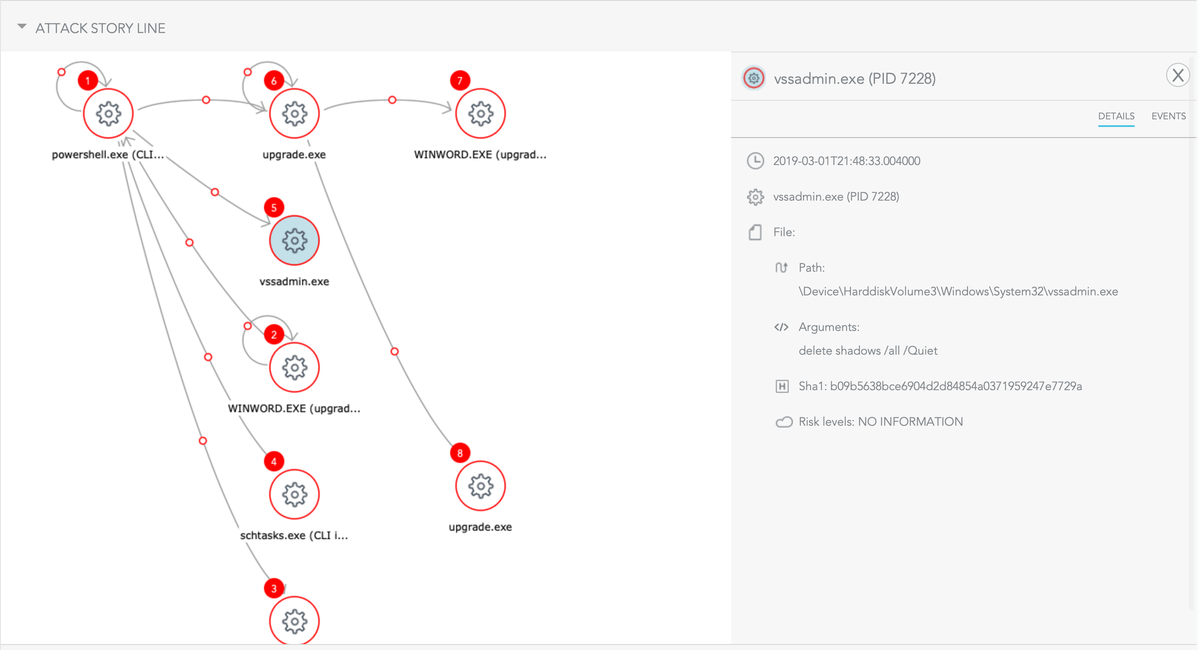
Features that can report unmanaged endpoints, IoT devices, mobiles and discover running services on your network are a major boon, as are utilities that you can incorporate into your browser to speed up threat hunting and research.
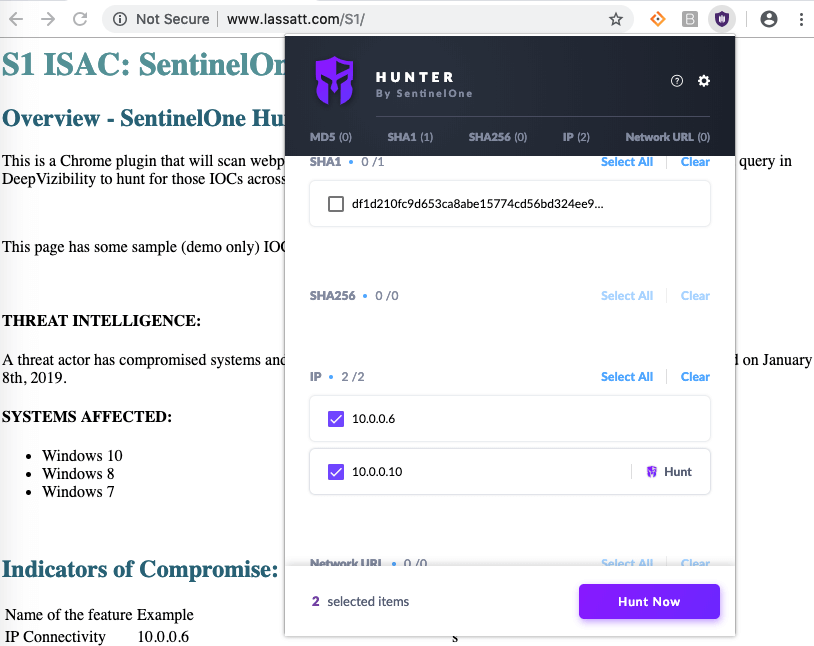
Threat hunting requires proper reporting tools to provide analysts with quality data, but it also presupposes that they have full confidence in the security solution protecting their network. Threat hunting is a time-consuming business, and your analysts can’t afford to waste time manually catching threats that your EDR solution should have found for them autonomously. Detecting advanced threats is the most difficult challenge security teams face, particularly if the organization is limited by a cyberskills staff shortage or stuck with a security solution that swamps them with masses of alerts or a high degree of false positives.
Another vital tool for analysts is good threat intelligence. There are a number of public or OSINT (open source intelligence) feeds where hunters can keep up to date with the latest IOCs such as malicious IP addresses, newly announced CVEs and sample hashes of the newest malware. For example, the SANS institute keeps a compiled list of suspicious domains. The Mitre ATT&CK framework is also a powerful tool to help threat hunters learn about the tools, tactics and procedures (TTP) used by advanced threat actors. You can, for example, search the Mitre ATT&CK database for groups that are known to target your sector or industry and learn about the techniques they have used. Armed with this intel, you can start to threat hunt across your network for evidence of that group’s TTPs.
How Do You Know What to Look For?
Using OSINT tools and frameworks like Mitre ATT&CK only works effectively if you know what you’re looking for, and that brings us to one of the essential components of threat hunting: hypothesis formation and testing.
Threat hunters need a solid understanding of the organization’s profile, business activities that could attract threat actors (such as hiring new staff or acquiring new assets, companies, etc), and baseline usage. For example, attackers will often want to blend in with ordinary users and try to acquire user credentials such as from a phishing or spear phishing campaign.
Having an understanding of users’ typical behavior is a useful baseline for investigating anomalous file access or log in events. Combining that with understanding what company data is of value to attackers and where it is located can lead to hypotheses such as “Is an attacker trying to steal data located at xyz?”. This in turn could prompt data collection that answers questions such as:
“Which users have accessed location xyz for the first time in the last n days?”
Advanced threat hunting techniques will try to automate as many tasks as possible using statistical analyses. Monitoring user behavior and comparing that behavior against itself to search for anomalies, for example, is far more effective than running individual queries, though both techniques are likely to be required in practice. Both are made easier if your have tools like SentinelOne that have a rich-set of native APIs enabling full integration across your security software stack.

How Often Should You Threat Hunt?
Some businesses choose to hunt for threats only on an ad hoc basis. This might be when a certain event is triggered (e.g., an access attempt on a particularly sensitive service or file location) or just when staff have available free time from other duties. While ad hoc hunting allows organizations with restricted staff and budgets to still engage in this extra layer of defense, it has the drawback of only allowing minimal hunts for a limited set of behaviors and is the least effective way to employ the strategy.
Scheduled threat hunting, where time is dedicated for staff to conduct hunts at regular intervals, is an improvement and can allow organizations to prioritize searches at different times and improve efficiency. However, scheduled threat hunting has the drawback that it offers a certain amount of dwell time for advanced attacks to try to operate in-between those intervals, so the shorter the interval the better.
Ideally, organizations with the sufficient staff and budget should engage in continuous threat hunting in which the network and endpoints are proactively engaged to uncover attacks on the network as part of a sustained effort.
Who Should Conduct Your Threat Hunting?
It’s probably clear by now that threat hunting is a specialist task. It requires an analyst who can use a variety of tools, understand and analyze the risks your organization faces, and is versed in the methods and tools used by advanced attackers.
While hiring in-house threat hunters can be a great way to go, organizatons need to have the budget for it and access to people with the relevant skills. For many enterprises, a more realistic approach can be to engage threat hunting services from MSSPs (Managed Security Service Providers) for some or all of their threat hunting work.
Conclusion
Threat hunting allows you to get out in front of the latest threats by proactively hunting for malicious activity. Advanced solutions like behavioral AI will stop most attacks in their tracks and are prerequisites to provide the visibility threat hunting requires, but malicious actors are always innovating and looking for ways around enterprise security. Organizations need to be vigilant to prevent vectors such as insider threats and highly targeted attacks. Adding the expertise of human analysts can provide that extra layer of security for your organization.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.