7 best practices for running Cloud Dataproc in production
June 10, 2019
Microsoft Azure Developer Camp – St. Louis
June 11, 2019As attackers have proven time and time again, a single weakness can compromise a system or network if defenders aren’t both informed and watchful. When it comes to leveraging vulnerabilities on the device, one area that is frequently overlooked is Bluetooth. This low-powered wireless technology is on every endpoint, widely used in Internet of Things (IoT) devices, is often active and is usually discoverable by default. What threats does Bluetooth wireless technology present and what can you do to prevent them? In this post, we take a look at Bluetooth vulnerabilities that affect the enterprise. We’ll also explain how you can mitigate risks from Bluetooth to ensure your network’s weakest link isn’t an unprotected wireless connection just waiting to be discovered.

What’s the Problem With Bluetooth?
It’s easy to think of Bluetooth as a relatively harmless technology from a security point of view. It’s widely believed that its apparent “10 metres” short range means attackers have to be in very close proximity in order to exploit it and that there’s not much they could do with it even if they were. Both those assumptions are wrong. Let’s see why.
Recall that Bluetooth has been around for over 20 years now and is widely used in almost every device that holds personal data, and many that don’t. From PCs, mobile phones, and car entertainment systems to headphones, keyboards, TVs and even toasters, if a device requires short-range local network connectivity to transfer data, files, photos or audio, Bluetooth is the default technology of choice.
Bluetooth connections are encrypted, but that has not stopped researchers finding vulnerabilities allowing them to eavesdrop on connections between phones and headsets. Bluetooth can be used to transfer files from one device to another, so if an attacker could access a device via the Bluetooth protocol they could also potentially access sensitive information on that device.
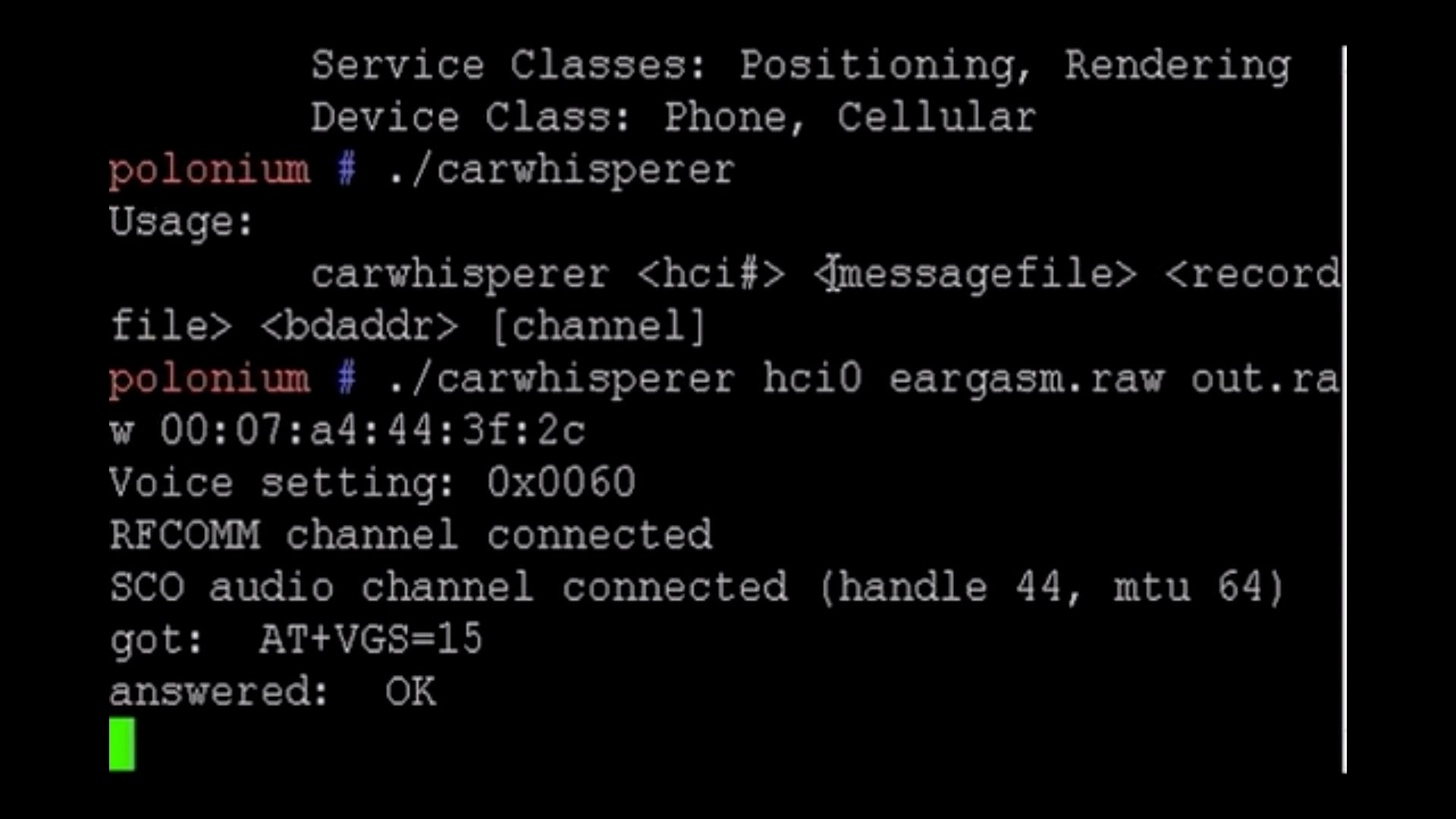
And that problem with range? SANS senior instructor Joshua Wright showed how Bluetooth discoverability can be extended to over a mile by using a directional antenna, standard equipment that can be bought in any hardware store. Wright’s demonstration used carwhisperer to listen in to a person’s conversations and even inject his own audio while they were using a Bluetooth headset.
And remember that range can also be extended by piggybacking Bluetooth signals off other devices or by using Bluetooth beacons. Such technologies are legitimately used both for security features (e.g., in Apple’s Find My service) and marketing campaigns.
![]()
Could attackers use these or other techniques to compromise your data, devices and networks? Let’s take a look.
Bluetooth Security Issues Are Out There
Bluetooth security issues are out there and affect potentially billions of devices, including both Apple and Android smartphones, Windows and Linux computers and anything else running unpatched Bluetooth firmware, such as the millions of IoT or so-called ‘smart’ devices.
The two biggest issues known to-date are BlueBorne and BleedingBit. BlueBorne is a collection of vulnerabilities first revealed in September 2017 that can allow an attacker to take over a device, infect it with malware or establish MITM attacks. While patches were made available for PCs and smartphones by the time the BlueBorne vulnerabilities were made public, millions of devices running older software remain at risk. This includes unpatched Windows and Linux machines, Apple devices not on iOS 10 or later, and around an estimated 1 billion unpatchable Android devices (any Android device running an OS earlier than Marshmallow).
Bluetooth mesh networking, an innovation that arrived in the same year as the BlueBorne vulnerabilities were discovered, allows many-to-many connections and ramps up the seriousness of BlueBorne: mesh networking means an attacker could easily jump from one device to another and build a Bluetooth botnet.
More recently, in November 2018, two critical chip-level vulnerabilities in Bluetooth Low Energy chips made by Texas Instruments were discovered. These chips are so widely used that the researchers who discovered them and dubbed them “BleedingBit” stated:
The Texas Instrument chips are so common that an attacker could simply walk into a lobby of a company, scan for available Wi-Fi networks and begin the attack, on the assumption the BLE vulnerability is present.
Importantly, BleedingBit does not require attackers to be “paired” with the target device or have any prior knowledge of the device’s information. All that is required is that the target device has Bluetooth enabled and that the attacker is within range.
It is crucial for enterprise security teams to be aware of these kinds of vulnerabilities because they can give an attacker full control over the infected device.
While BlueBorne and BleedingBit have attracted the biggest headlines, they’re not the only vulnerabilities discovered in the modern Bluetooth protocol. Eagle-eyed observers of Apple’s Security updates will have noticed that in July 2018, Apple delivered patches to its platforms to protect against an attack that could allow a malicious actor to force pair with a device.
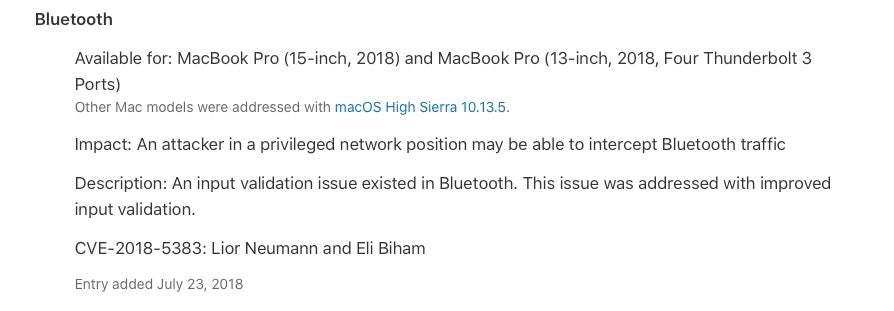
The vulnerability allowed an attacker to discover the encryption key used on the victim’s device and use that to decrypt and forge data without alerting the user.
CVE-2018-5383 didn’t just affect Apple devices though. Versions of the Android operating system were also vulnerable to attack, which was due to a design flaw in the Bluetooth protocol. Windows machines only escaped being implicated because at the time Microsoft were still deploying an even less-secure earlier version of the protocol.
It is also worth mentioning that malware is taking greater interest in harvesting Bluetooth device information. Malware developed by the “ScarCruft” group was recently found to be exfiltrating Bluetooth related information from infected machines, including the device’s MAC address, class, connection status and authentication status.
Bluetooth Device Control
What mitigations are available to ensure your devices are protected from Bluetooth attacks?
For devices that are equipped with Bluetooth but do not actually need or use its functionality, be sure to reduce your attack surface with an unbeatable strategy: turn that Bluetooth off! If that’s not an option, your first step is to ensure that all devices are fully patched.
To prevent eavesdropping by tools such as carwhisperer, ensure that Bluetooth-enabled devices like headsets cannot be paired with a default pairing code or use device control if your security software has that feature.
Enterprise admins and security teams are also advised to implement Bluetooth device control across all the organization’s endpoints to address the more serious bugs and vulnerabilities noted in the previous section.
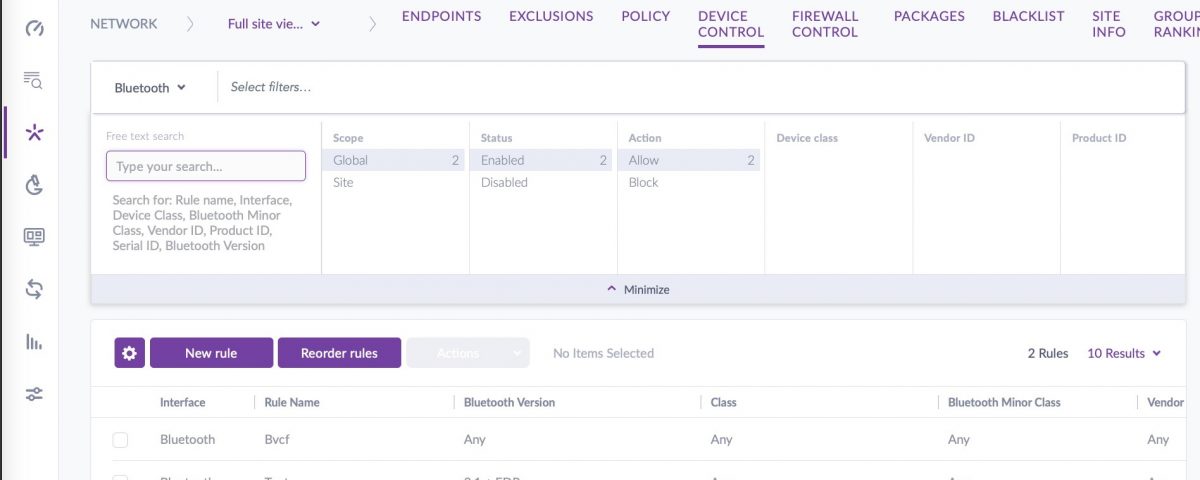
Within the SentinelOne management console, this is easily achieved via the Network view and the Device Control tab. You can create a default policy to start with and then customize it or build your own custom rules from the ground up.
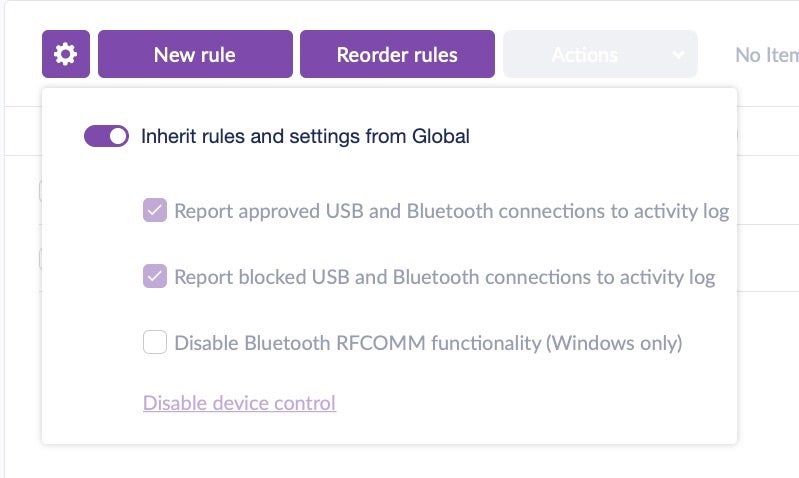
With Bluetooth Device control, you’ll now have visibility into what Bluetooth connections are occurring on your endpoints. You also have the ability to restrict pairing to only devices you choose, or to block specific devices. The control can be as coarse or as fine-grained as you wish, with options to specify device class, minor class, Vendor ID and more.
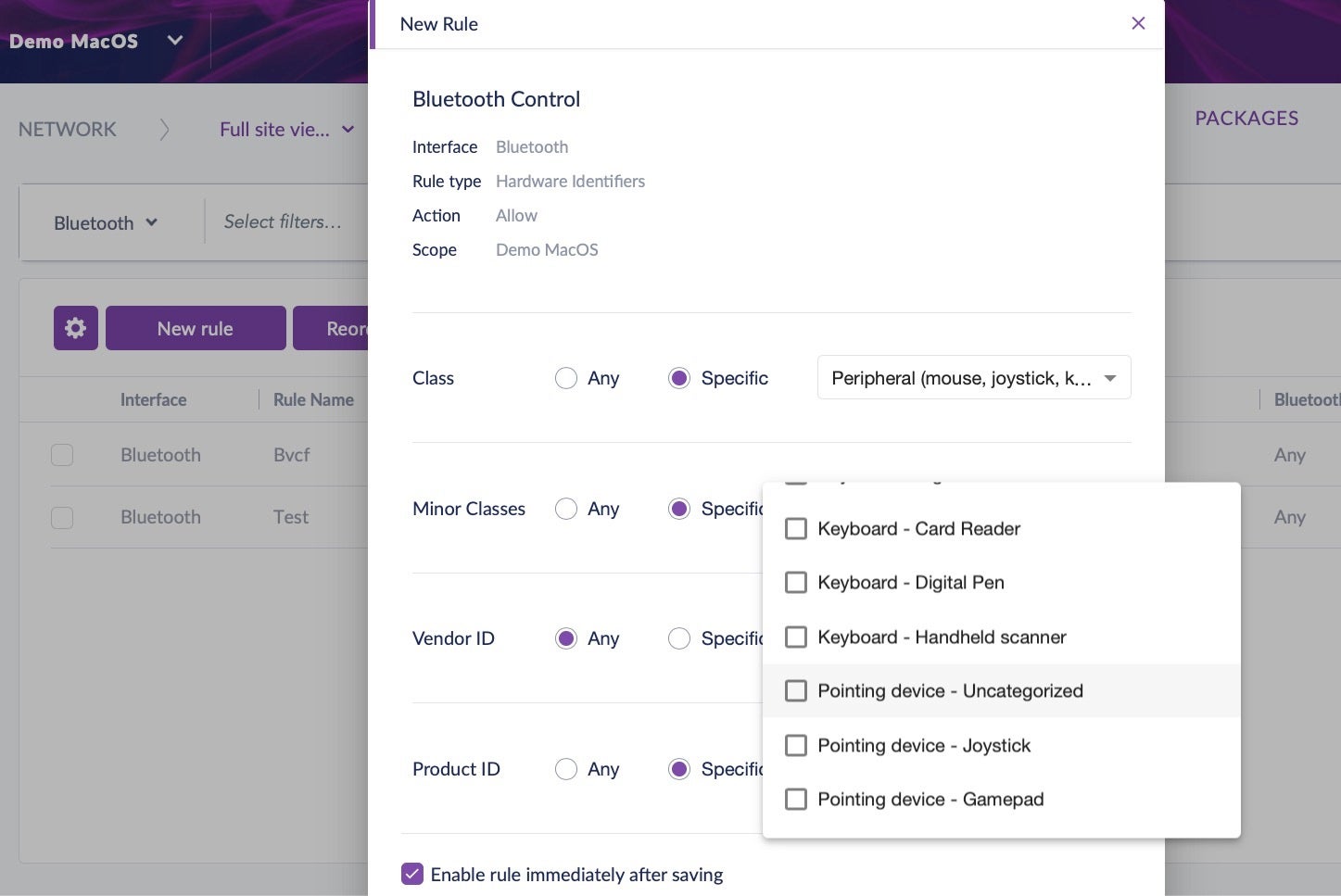
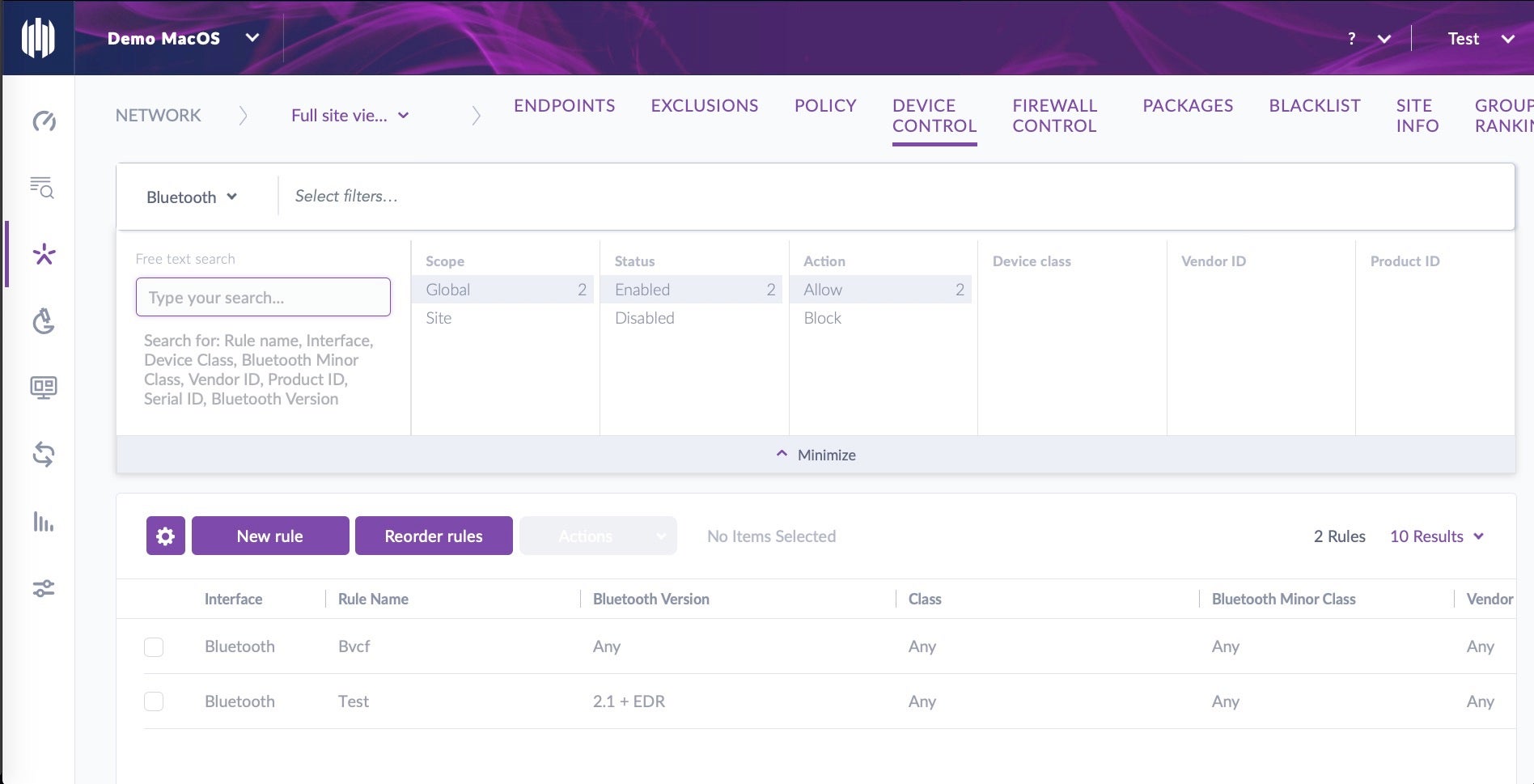
Once you have policies in place, you can search across your network by choosing the “Device Control” tab and choosing “Bluetooth” from the drop down menu in the filter bar.
Conclusion
Bluetooth vulnerabilities may seem like an unlikely avenue of attack to some, but if there’s one thing we have learned from studying malicious actors it is that they never miss a trick. They will always go for the low-hanging fruit where possible, but where not, they won’t hesitate to exploit any vulnerability available.
The technological barrier to compromising a network via Bluetooth is not particularly high for an adversary that’s determined to gain access to your network, even if the risks are somewhat greater than just launching a simple phishing campaign. And one important advantage of Bluetooth attacks over the usual methods of compromise? They can even reach air-gapped systems if those systems have Bluetooth turned on for keyboard or other peripherals.
As we noted above, SentinelOne customers can mitigate all these risks effectively from within the management console by using a Bluetooth device control policy. If you’re not a SentinelOne customer already, you can see our Bluetooth and USB device control in action for yourself by requesting a free demo.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Read more about Cyber Security
How Hackers Use Social Media To Profile Targets
EternalBlue | The NSA-developed Exploit That Just Won’t Die
What Microsoft Just Announced and Why It is So Important
Malicious Media | Why Your Endpoints Need Device Control
How Secure Is Open-Source Software?