As expected, WWDC 2019 kicked off on this week with major announcements about the next version of Apple’s desktop operating system, macOS 10.15 Catalina. Given the security issues that have arisen over the last couple of releases – from jaw-dropping bugs to repeated bypasses of built-in Mac security tools – it’s no surprise that Catalina has received plenty of attention from Apple engineers on the security front. 10.15 sees some major developments that will affect both the enterprise and developers of security solutions. In this post, we round up what’s been announced so far and explain how it could affect you.

1. Goodbye Kexts, Hello SystemExtensions
Starting with macOS 10.15 Catalina, security vendors are being asked to move to the new EndpointSecurity and SystemExtensions frameworks and away from kernel extensions, which are now formally deprecated. In Catalina, Apple have introduced system extensions to replace Kernel Extensions. The idea is to provide developers with similar functionality while running the code entirely in user space rather than directly in the kernel.
Importantly, in parallel with the way Apple changed Safari Extensions last year, system extensions must be part of a host application – standalone system extensions will not be allowed. This has the advantage that no installer or package will be necessary as the system extension is itself inside the host bundle. Similarly, uninstalling should be more convenient, as simply moving an app to the Trash deactivates the system extension, assuming the trashed app is the last or only copy on board.
One important change that takes effect immediately and which may impact enterprise workflows, particularly for fleets under MDM or managed profiles, is that while kernel extensions remain functional on macOS Catalina, installing new kexts now requires a restart.
Related to the deprecation of kexts is the new FileProvider API for cloud storage providers (Google, Dropbox, OneDrive, BoxDrive and so on).
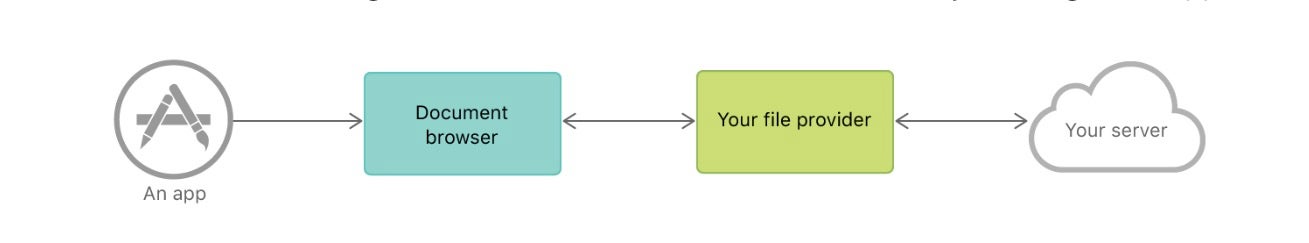
This new API will help cloud storage providers to transition away from kernel extensions and still integrate their services into the Finder. Without the need for kernel extensions, these providers will now be able to deliver their apps through the Mac App Store.
What This Means For Enterprise:
Deprecating kernel extensions is a big change, but likely a good one in the long run and more painful to developers than enterprise, unless you are running your own custom built kernel extensions. For anyone currently relying on kexts to deliver services, you still have a reasonably decent period of grace in which to start moving away and learning about the new EndpointSecurity and SystemExtensions frameworks. Let’s all hope this new technology that Apple is giving us with one hand is as powerful as the one it’s taking away with the other!
2. Not One Partition, But Two
In macOS Catalina, Apple have introduced a new filesystem partitioning architecture. In one partition is a dedicated, “read-only” system volume containing the OS itself. This is completely separate from all user data, and nothing – other than Apple signed code, such as updates – can overwrite operating system files. It’s basically System Integrity Protection taken to the next level. Instead of protecting locations in an unprotected partition, the entire partition is sealed off.
There’s potential for some initial confusion here as the mount paths are no longer quite as obvious. Where is user data located? Traditionally, it would be in /Users/<username>. On Catalina, it’s in /System/Volumes/Data/Users/<username>. Good-old fashioned root, / appears now to be a system-only volume.
What This Means For Enterprise:
Getting used to alternative path naming conventions may be a little uncomfortable at first, but in principle a clear delineation between partitions for system and user data is an excellent move which should make system restore and backup even more straightforward. Apple’s preview notes suggest that macOS Recovery will feature the ability to restore more easily from snapshots if things go wrong after installing a 3rd-party update, a feature that we’re sure relies on the new disk partitioning scheme.
3. Gatekeeper
Gatekeeper has been beefed up to provide more than just checks on an application’s source. In macOS 10.14 and earlier, Gatekeeper manages downloads according to source with settings that distinguish between the App Store only and App Store and identified developers. In macOS Catalina, those distinctions remain (with a further option available via the command line to run apps from any source), but Gatekeeper will now also a perform a malicious content scan and signature validation from time-to-time to check that code has not been tampered with.
Importantly, Apple says that all software, whether quarantined or not, will be scanned for malicious content. Whether this applies to code that is not run from bundles (such as scripts and binaries downloaded, say, via Curl) or not remains to be seen. The early signs are probably not. Moreover, the details of exactly how this scan works and what it actually scans for will have to await public release of Catalina later this year. Will it be more robust than the anaemic Xprotect? We certainly hope so.
What This Means For Enterprise:
Beefing up Gatekeeper is certainly welcome. We’ve long complained that it’s easily bypassed. What we’d really like to see is admin privileges applied to removing the quarantine bit that Gatekeeper relies on, but there’s no mention of that in the initial beta release. For those worried about needing to run unsigned code, Apple insist that they’ve no plans (as yet) to prevent users from running unsigned code on macOS if they wish.
4. Notarization
Along with the changes to Gatekeer, notorization is – as expected after the incremental changes seen during macOS 10.14 Mojave – now compulsory. Notarization is a set of automated scans that take place when a developer builds an app for distribution. The changes in Catalina mean that developers will be unable to build and distribute apps for use on 10.15 without notarizing them first.
What This Means For Enterprise:
The jury’s still out on the efficacy of notarization. While Apple’s intent is good, the lack of transparency over what the automated scans actually look for means it’s very difficult to know how much, if any, malicious content Apple’s notarization is actually blocking. Even worse, since a notarized app can easily be updated after installation to contain malicious code, there’s a feeling among developers that these extra hoops hit “the good guys” with extra burdens more than do anything to deter malware developers. Perhaps the changes to Gatekeeper that promise periodic re-scans may serve to ameliorate this, but it remains to be seen in practice.
5. Prompts Everywhere
In macOS Catalina, Apple have further extended the number and range of User prompts that can be generated when code attempts to access certain locations and functions.
In order to prevent attackers enabling FileVault with a secret key via fdesetup, a possible avenue for a ransomware attack, Apple have introduced a new prompt that requires user approval before FileVault can be used to encrypt the drive programmatically.
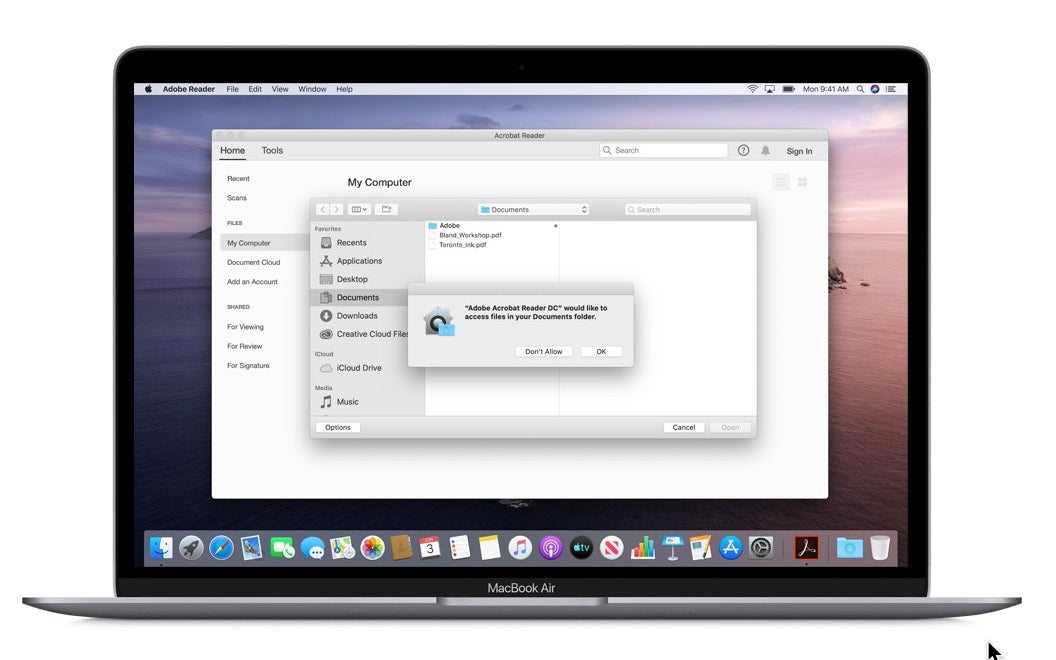
Programmatic access to user’s Desktop and Documents folders will now also require user approval, as will access to the Downloads folder, iCloud, mounted volumes and cloud storage folders like Dropbox, OneDrive and similar. As on Mojave, the list of approved apps can be viewed and managed in the System Preferences Privacy pane.
The prompt takes the form of a message “SomeApp would like to access files in your Desktop folder” with “Don’t Allow” and “OK” as the options; there is no password required for this approval.
There are also further controls applied to other directories typically used for system administration purposes, including /usr/lib/cron (occassionally used by adware as a persistence mechanism), /private/var/at and private/var/rc.
Attempting to install a new cron job, for example, should produce an alert informing the user that the program is attempting to write the crontab and wants permission to administer the Mac.
% crontab: installing new crontab
This command should generate the user prompt. If the user clicks “Don’t Allow” the command should fail with an “operation not permitted” error.
% crontab: tmp/tmp.1095: Operation not permitted
Since we’re discussing prompts, it’s worth noting that Safari also gets an extra prompt when the user tries to download from any site they haven’t previously downloaded from. If the user approves the site, it’s added to Safari’s Website preferences under a new “Downloads” item in the sidebar.
Other areas coming under TCC read protection in macOS Catalina are
In 10.14 Mojave, code that tries to access the user’s camera or microphone causes a user consent prompt. This mechanism is extended in macOS 10.15 Catalina to screen recording or keyboard input monitoring. Clearly, the intention here is to put an extra roadblock in the way of malicious software such as keyloggers and spyware tools.
Finally, Full Disk Access has been extended to include the Trash folders, creating yet another prompt for programs or code that attempts to move or read files the user has trashed.
What This Means For Enterprise:
It’s great to see Apple being proactive here, blocking off potential persistence mechanisms like cron and at jobs. However, relying on User prompts is a flawed approach. As we’ve pointed out in the past, if users are constantly asked to confirm access to regular files and folders they’re highly likely to develop an unthinking “click-through” habit that soon turns into “muscle memory”.
Dialog fatigue is a real issue here and arguably undermines the value of the protection in the first place. On top of that, if your enterprise is heavily reliant on a lot of automation scripts, expect large scale failures and the need for major rewriting when you transition over to 10.15. For enterprises that employ MDM and managed profiles, TCC whitelisting will be high on your priority of things to take care of.
6. Scripting Languages
Speaking of scripting, if you were expecting Python 3 or a newer version of Bash to finally make it to macOS 10.15, Apple instead pulled out a different surprise. In the beta release notes, Apple says:
Scripting language runtimes such as Python, Ruby, and Perl are included in macOS for compatibility with legacy software. Future versions of macOS won’t include scripting language runtimes by default, and might require you to install additional packages. If your software depends on scripting languages, it’s recommended that you bundle the runtime within the app. (49764202)
Use of Python 2.7 isn’t recommended as this version is included in macOS for compatibility with legacy software. Future versions of macOS won’t include Python 2.7. Instead, it’s recommended that you run python3 from within Terminal. (51097165)
Another unexpected turn was that Apple have moved the Terminal’s default shell from Bash to Zsh although you can change the default back to Bash if you wish.
What This Means For Enterprise:
If you’re using Python in the enterprise, there’s a good chance that you’ve already installed your own Python 3 runtime and are managing these dependencies yourself. Although we think it’s a shame that Apple didn’t just plump to ship a modern python implementation by default, we don’t expect this change to cause major issues. As for the shift to zsh, that was unexpected but probably reflects no more than the favourite default shell among Apple engineers!
7. Activation Lock & Other Security Features
There’s several other changes in macOS Catalina worthy of quick mention. First, 32-bit processes are now dead. This would be bigger news if Apple hadn’t been warning us about it for quite some time. As it is, no one (developers, especially) should be surprised to hear this. However, if you’re still relying on 32-bit apps, your only option is to stay off Catalina until you’re not.
For T2-equipped Macs, Activation Lock comes to the Mac to parallel what’s on offer for iOS. This allows you to erase (or reactivate) a Mac if it’s lost or stolen, making it inoperable by thieves and only recoverable by you. Similarly, the new FindMy feature allows a Mac to be located by piggybacking off other Apple devices in it’s vicinity, even when the machine is not booted.
We should also give a quick shout out to a couple of security-related changes to Mail, Apple’s native email client. In macOS 10.15 Catalina, it’s now possible to block a sender just by clicking the sender’s name and choosing “Block Contact”. We think this is a great way to help reduce corporate spam and other unwanted mail. Also unsubscribing from spam or overly-active lists also got a little easier as Mail now includes an in-line button to automate sending ‘unsubscribe’ messages to unwanted lists.
Conclusion
With macOS Catalina, Apple have made some big shifts in terms of security . It’s still too early to see how these shifts will play out or whether they will present any real obstacles to malware authors. We suspect that, as with Mojave, relying on User prompts will fail to trouble malicious software. Just how effective the new Gatekeeper and Notarization policies prove to be will depend very much on the details of their implementation, something we’ll be keeping an eye on here at SentinelOne.
Additional Resources
We would like to gratefully acknowledge the following sources that were helpful in compiling this article:
Apple macOS 10.15 Catalina Preview
Apple macOS 10.15 Catalina Beta Release notes
Rich Trouton’s WWDC 2019 Notes
mrmacintosh’s index of need-to-know changes
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.






