You will undoubtedly recall the names Shadow Brokers, who back in 2017 were dumping software exploits widely believed to be stolen from the US National Security Agency, and WannaCry, the notorious ransomware attack that struck only a month later.
Two years is a long-time in cybersecurity, but Eternalblue (aka “EternalBlue”?, “Eternal Blue”?), the critical exploit leaked by the Shadow Brokers and deployed in the WannaCry and NotPetya attacks, is still making the headlines. Although a recent claim by the New York Times that Eternalblue was involved in the Baltimore attack seems wide of the mark, there’s no doubt that the exploit is set to be a potent weapon for many years to come. In this post, we explain why and take a closer look at Eternalblue.

What is Eternalblue?
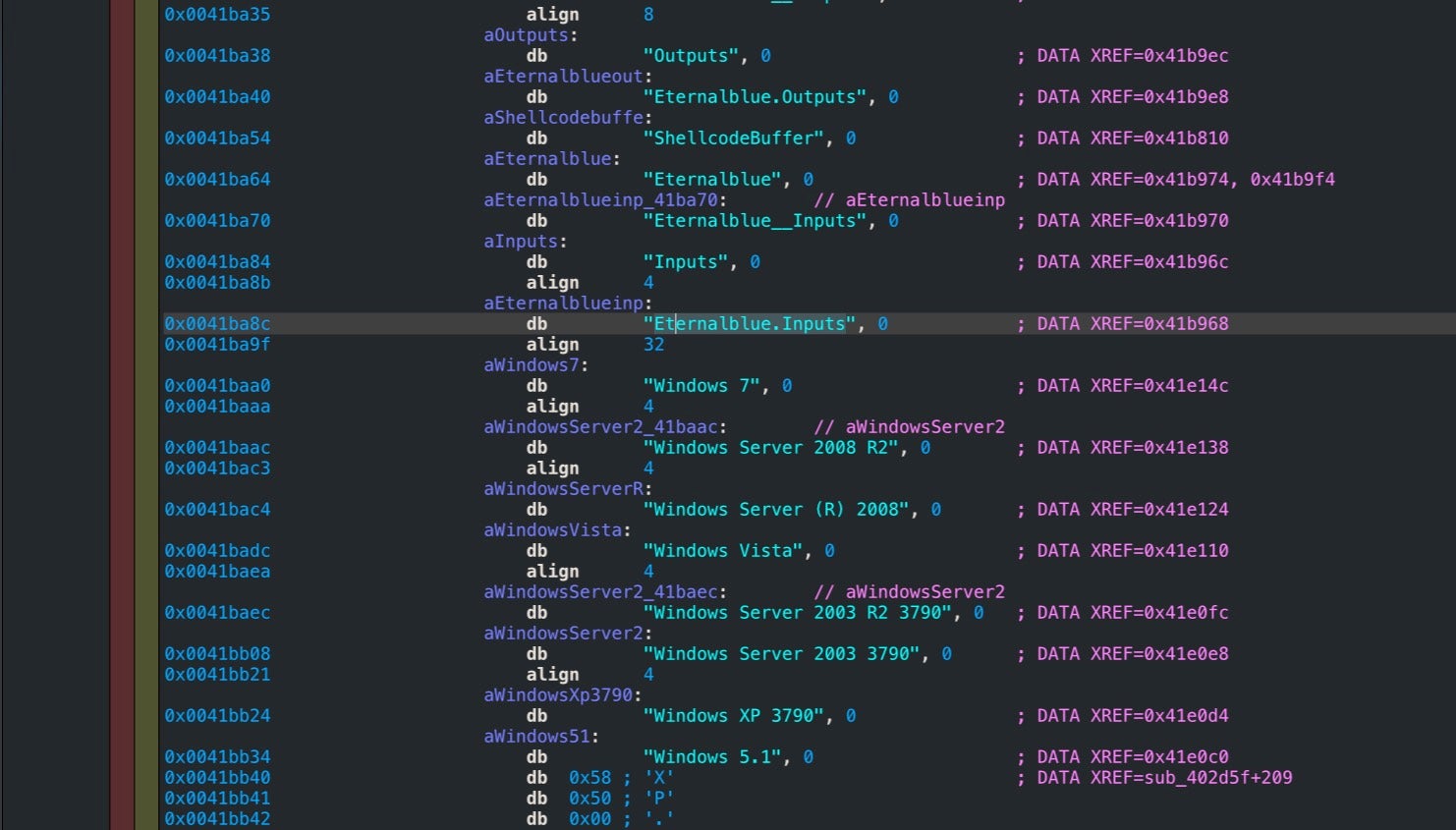
CVE-2017-0143 to CVE-2017-0148 are a family of critical vulnerabilities in Microsoft SMBv1 server used in Windows 7, Windows Server 2008, Windows XP and even Windows 10 running on port 445. Hardcoded strings in the original Eternalblue executable reveal the targeted Windows versions:
?
The vulnerability doesn’t just apply to Microsoft Windows, though; in fact, anything that uses the Microsoft SMBv1 server protocol, such as Siemens ultrasound medical equipment, is potentially vulnerable.
Eternalblue itself concerns CVE-2017-0144, a flaw that allows remote attackers to execute arbitrary code on a target system by sending specially crafted messages to the SMBv1 server. Other related exploits were labelled Eternalchampion, Eternalromance and Eternalsynergy by the Equation Group, the nickname for a hacker APT that is now assumed to be the US National Security Agency.
?
How Widespread is Eternalblue?
The flaws in SMBv1 protocol were patched by Microsoft in March 2017 with the MS17-010 security update. Unfortunately, despite the patch being available for more than 2 years, there are still reportedly around a million machines connected to the internet that remain vulnerable.

?
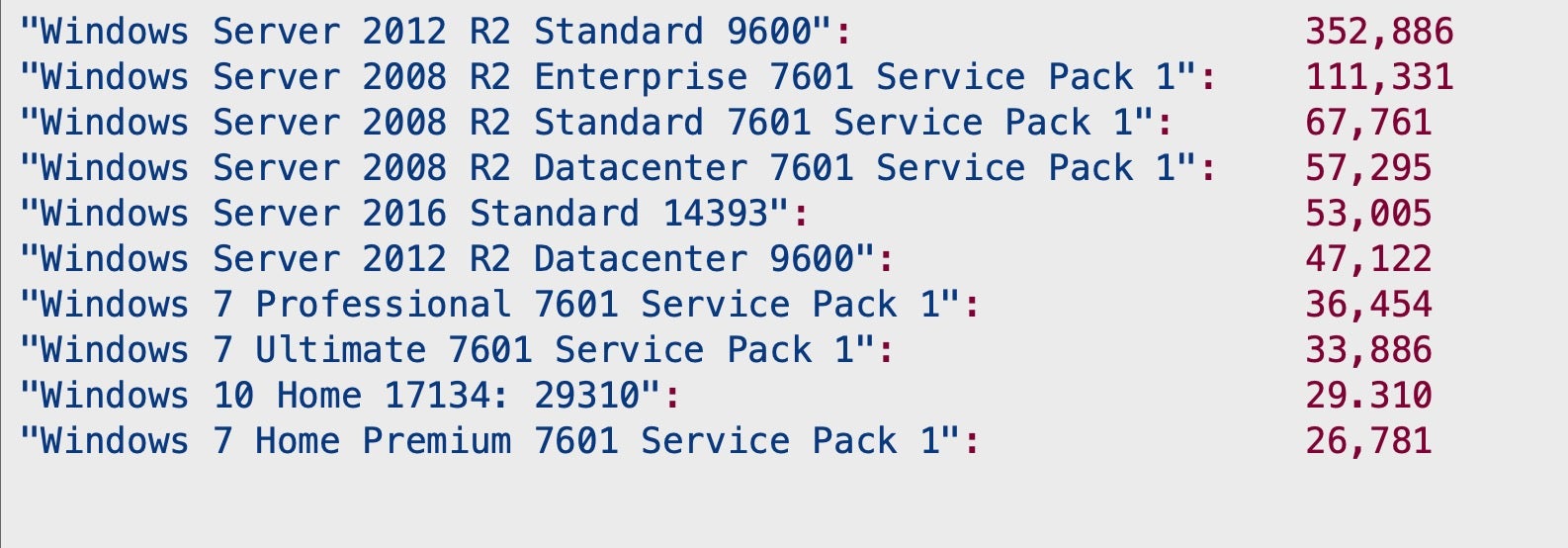
Worldwide, the Windows versions most in need of patching are Windows Server 2008 and 2012 R2 editions.
?
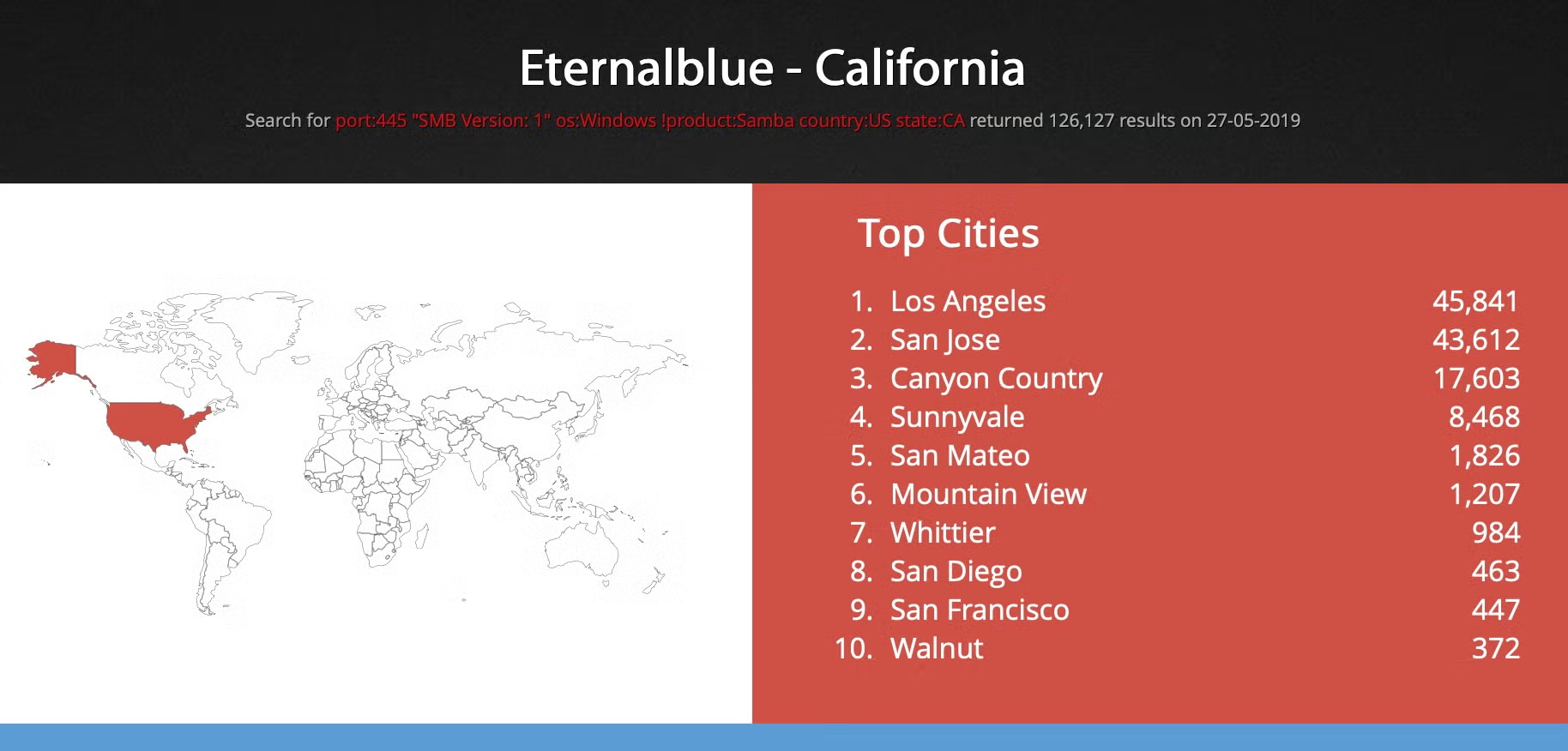
Of the more-than 400,000 machines vulnerable to Eternalblue located in the US, over a quarter of those, some 100,000 plus, can be found in California, at the heart of the US tech industry.
?
And it’s not just ransomware that has been making use of the widespread existence of Eternalblue. Any malware that requires worm-like capabilities can find a use for the exploit. Cryptojackers have been seen targeting enterprises in China through Eternalblue and the Beapy malware since January 2019.
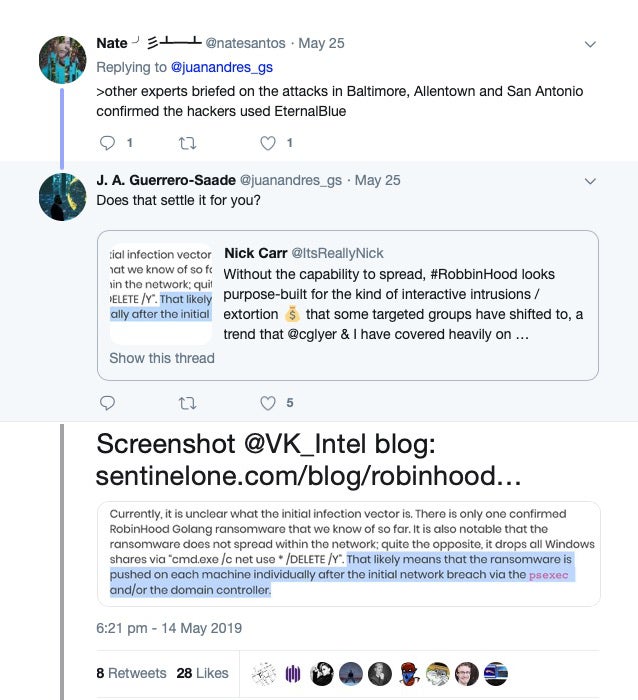
Further, now that ransomware is back in fashion after a brief hiatus during 2018, Eternalblue is making headlines in the US again, too, although the attribution in some cases seems misplaced. Contrary to some reports, the RobinHood Ransomware that has crippled Baltimore doesn’t have the ability to spread and is more likely pushed on to each machine individually.
How Is Eternalblue Used?
As mentioned above, exploiting CVE-2017-0144 with Eternalblue was a technique allegedly developed by the NSA and which became known to the world when their toolkit was leaked on the internet.
 ?
?
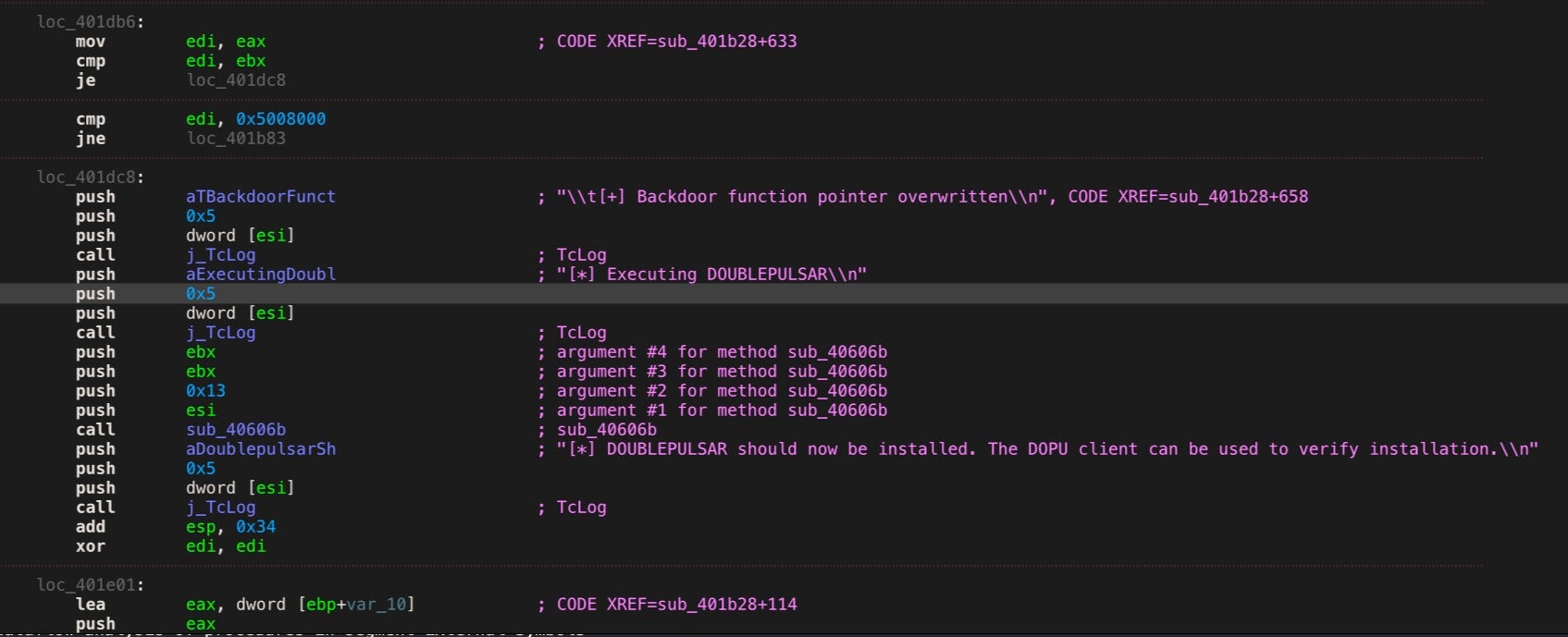
To exploit the vulnerability, an unauthenticated attacker only has to send a maliciously-crafted packet to the server, which is precisely how WannaCry and NotPetya ransomware were able to propagate. Essentially, Eternalblue allowed the ransomware to gain access to other machines on the network. Attackers can leverage DoublePulsar, also developed by the Equation Group and leaked by the Shadow Brokers, as the payload to install and launch a copy of the ransomware on any vulnerable target.
?
How Does Eternalblue Work?
Eternalblue relies on a Windows function named srv!SrvOS2FeaListSizeToNt. To see how this leads to remote code execution, let’s take a quick look at how SMB works.
Primarily, SMB (Server Message Block) is a protocol used to request file and print services from server systems over a network. Among the protocol’s specifications are structures that allow the protocol to communicate information about a file’s extended attributes, essentially metadata about the file’s properties on the file system.
Eternalblue takes advantage of three different bugs. The first is a mathematical error when the protocol tries to cast an OS/2 FileExtended Attribute (FEA) list structure to an NT FEA structure in order to determine how much memory to allocate. A miscalculation creates an integer overflow that causes less memory to be allocated than expected, which in turns leads to a buffer overflow. With more data than expected being written, the extra data can overflow into adjacent memory space.
Triggering the buffer overflow is achieved thanks to the second bug, which results from a difference in the SMB protocol’s definition of two related sub commands: SMB_COM_TRANSACTION2 and SMB_COM_NT_TRANSACT. Both have a _SECONDARY command that is used when there is too much data to include in a single packet. The crucial difference between TRANSACTION2 and NT_TRANSACT is that the latter calls for a data packet twice the size of the former. This is significant because an error in validation occurs if the client sends a crafted message using the NT_TRANSACT sub-command immediately before the TRANSACTION2 one. While the protocol recognizes that two separate sub-commands have been received, it assigns the type and size of both packets (and allocates memory accordingly) based only on the type of the last one received. Since the last one is smaller, the first packet will occupy more space than it is allocated.
Once the attackers achieve this initial overflow, they can take advantage of a third bug in SMBv1 which allows heap spraying, a technique which results in allocating a chunk of memory at a given address. From here, the attacker can write and execute shellcode to take control of the system.
It didn’t take long for penetration testers and red teams to see the value in using these related exploits, and they were soon improved upon and incorporated into the Metasploit framework.
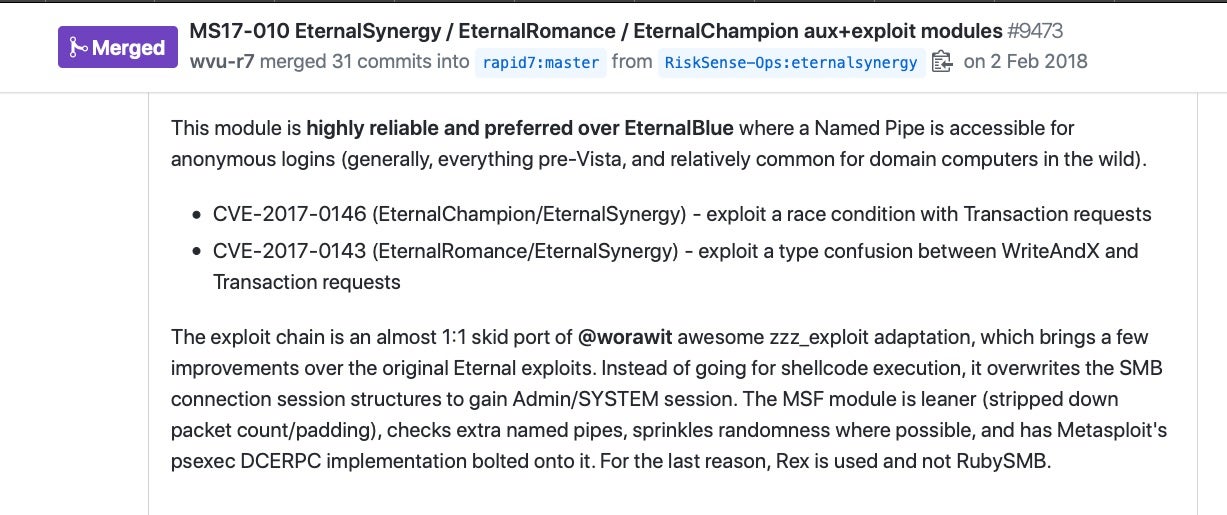
A fairly-straightforward Ruby script written by Sean Dillon and available from within Metasploit can both scan a target to see if it is unpatched and exploit all the related vulnerabilities.
Eternalblue – Here To Stay
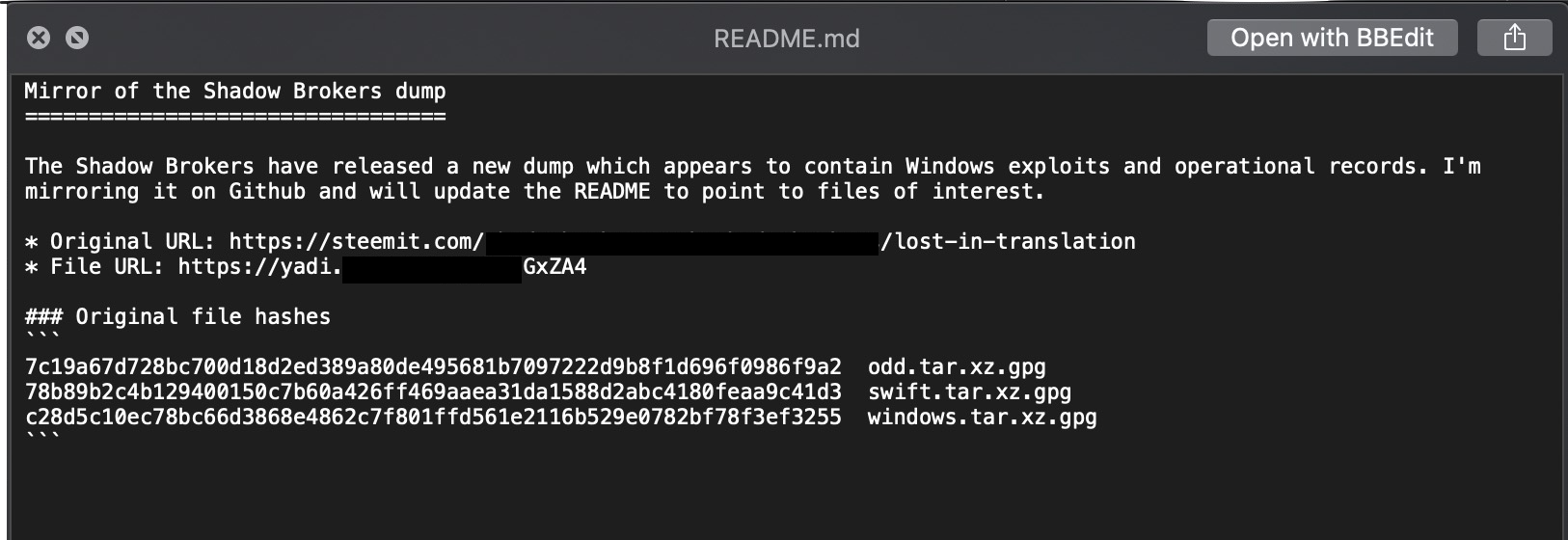
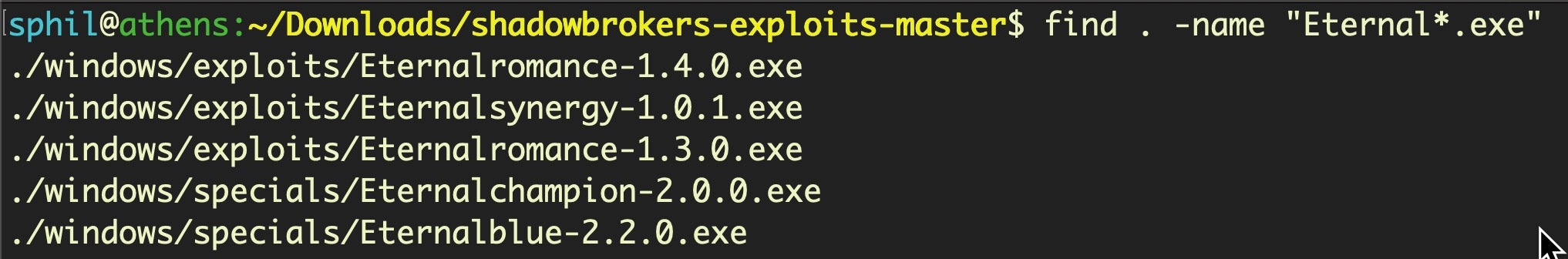
As mentioned earlier, the original code dropped by Shadow Brokers contained three other ‘Eternal’ exploits: Eternalromance, Eternalsynergy and Eternalchampion.
?
Further work after the initial Shadow Brokers dump resulted in a potentially even more potent variant known as EternalRocks, which utilized up to 7 exploits. While the author of that malware shut down his operation after intense media scrutiny, other bad actors may have continued similar work as all the tools required were present in the original leak of Equation Group’s tool kit.
Among “white hats”, research continues into improving on the Equation Group’s work. Only last month, Sean Dillon released SMBdoor, a proof-of-concept backdoor inspired by Eternalblue with added stealth capabilities.
The Equation Group’s choice of prefixing their collection of SMBv1 exploits with the name ‘Eternal’ turned out to be more than apt since the vulnerabilities they take advantage of are so widespread they will be with us for a long time to come.
How To Stay Safe From Eternalblue
By far the most important thing to do to prevent attacks utilizing Eternalblue is to make sure that you’ve updated any older versions of Windows to apply the security patch MS17-10.
If, for some reason, that’s not possible, other mitigations include disabling SMBv1 and not exposing any vulnerable machines to internet access.
Ensuring you have a capable EDR security solution should go without saying, but if your organization is still behind the curve on that one, remember that passive EDR solutions are already behind-the-times.
Conclusion
The whole story of Eternalblue from beginning to where we are now (certainly not “the end”) provides a cautionary tale to those concerned about cybersecurity. From the folly of stockpiling 0-day exploits to that of failing to apply security updates in a timely manner, it does seem with hindsight that much of the damage – from WannaCry and NotPetya to who-knows-what-comes-next – could have been largely avoided.
Whether government agencies will learn their lesson is one thing, but it is certainly within the power of every organization to take the Eternalblue threat seriously in 2019 and beyond. Patching your OS and protecting your data and network with a modern security solution before the next outbreak of Eternalblue-powered malware are not just sensible but essential steps to take.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.







