Threats come and go, but one thing remains the same: the ability of cybercriminals to adapt to circumstances. A brief decline of interest in ransomware as criminals focused their attention on cryptojacking during the previous year appears to have come to an end, and ransomware attacks are once again escalating.
In this post, we’ll explain what ransomware is, how it spreads, how prevalent it is and what you can do to protect yourself against it.

What is Ransomware?
As the name implies, ransomware is a kind of malware that demands some form of payment from the victim in order to recover control of their computer and/or data. Within that broad definition, there are a few twists and turns that are worth noting.
First, there are variants with regard to exactly what the victim is being held to ransom for. Typically, the attacker encrypts personal files on the victim’s computer in such a way that they cannot be opened unless the victim has a decryption key. Access to the decryption key is what the attacker wants the victim to pay for.
Encryption ransomware has been seen on the mobile platform, too, with SimpleLocker reportedly infecting over 150,000 Android devices.
In other cases, depending on the target, the attacker may threaten to publicise or leak sensitive information found on the victim’s device, giving rise to the names “leakware” and “doxware” for this kind of attack. That could be personally compromising photos or emails, but more likely in the case of targeted attacks against businesses it may be data the company wouldn’t want made public. That could be anything from client data to a movie script.
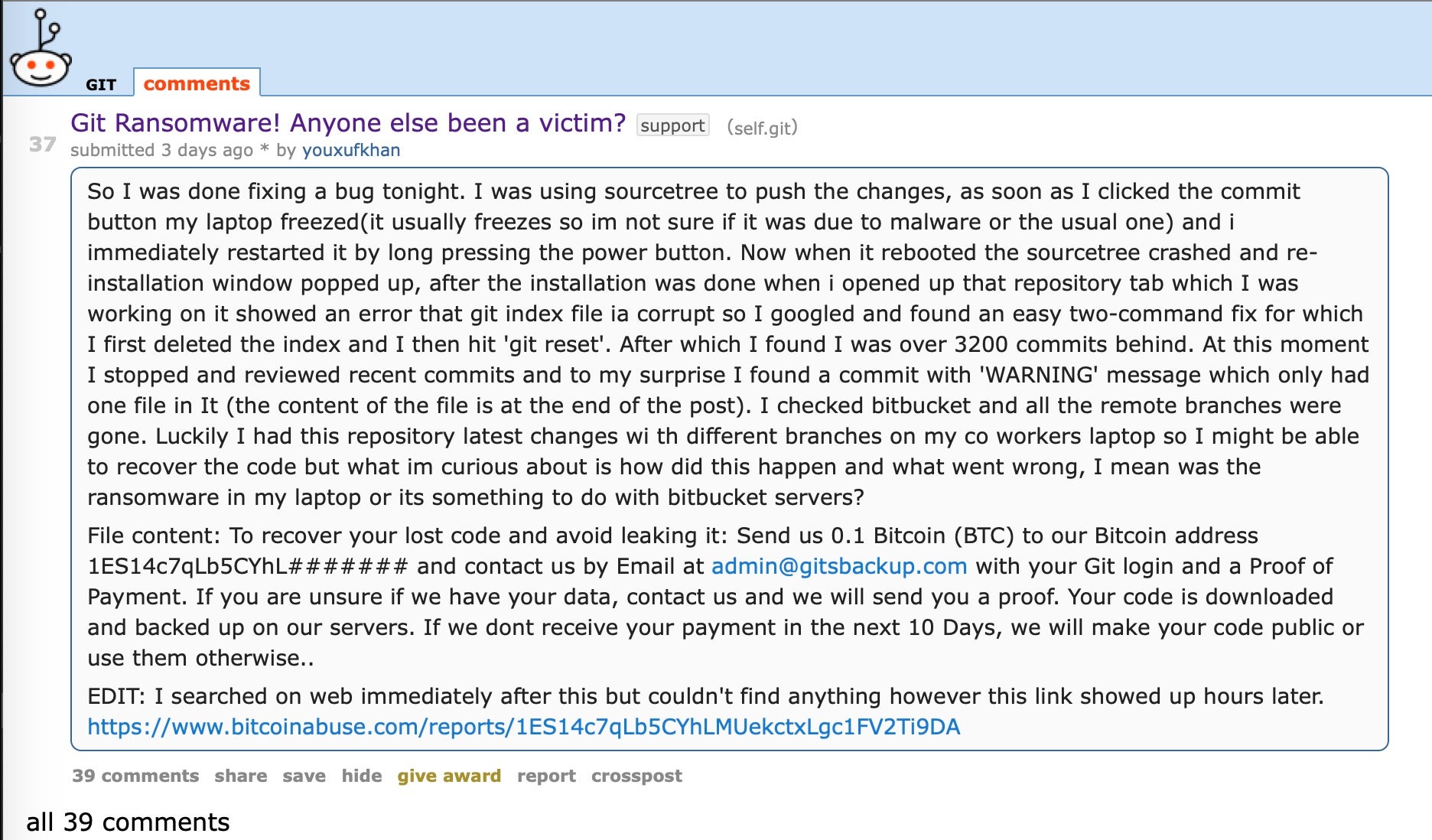
In a leakware attack seen just this past week, criminals targeted developers and threatened to make the hijacked code public or “otherwise use” the developer’s intellectual property if the victim did not pay the ransom.
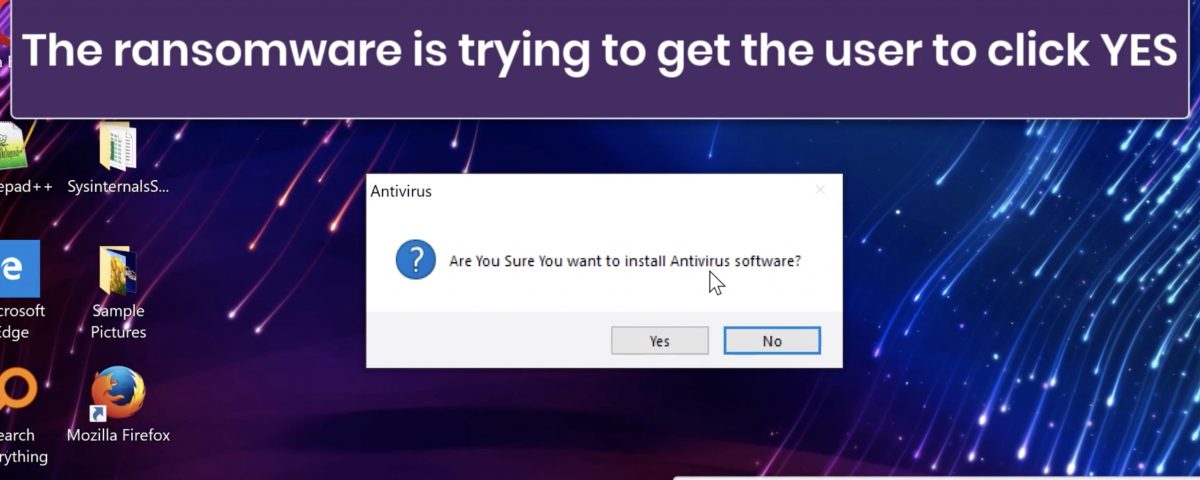
Other forms of ransomware such as the infamous WinLock malware from all the way back in 2010 are a form of denial-of-service attack, only in this case the service being denied is access to the victim’s own device. Such “blocking” attacks have found a new outlet on the iOS and Android mobile platforms. On Apple devices, for example, the technique tries to leverage compromised iCloud credentials to lock users out of their devices unless they pay a ransom.
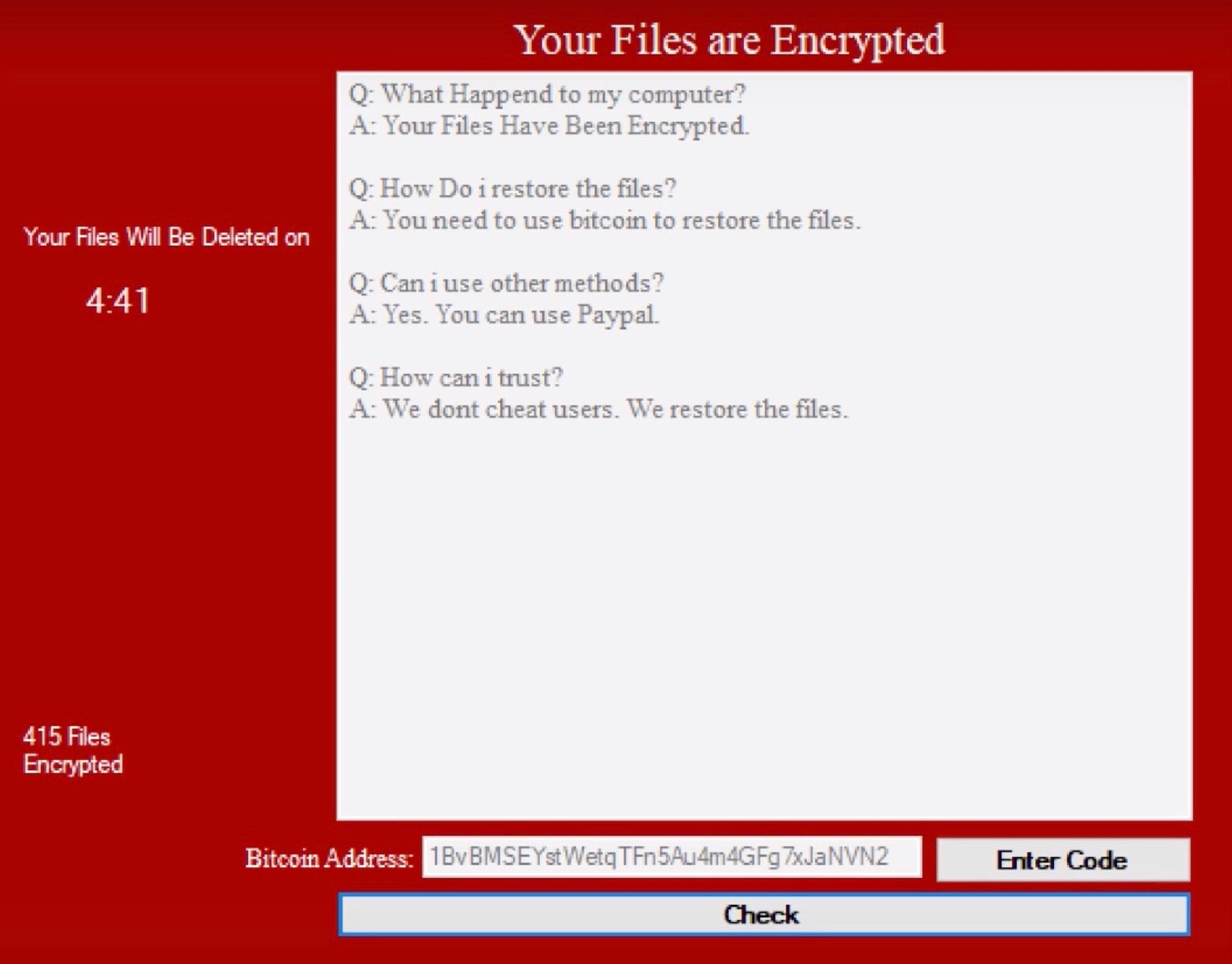
In the more common case where the ransomware has encrypted a user’s files, what happens next is some form of demand accompanied with a threat. Usually, but not always, the demand comes in the form of a ransom note that appears on the screen. This tells the victim what has happened, how much they have to pay, and how they can pay it. Ransom notes themselves can range from simple text files with multiple spelling and grammar errors to graphical layouts with icons designed to ease and encourage the steps necessary for payment:
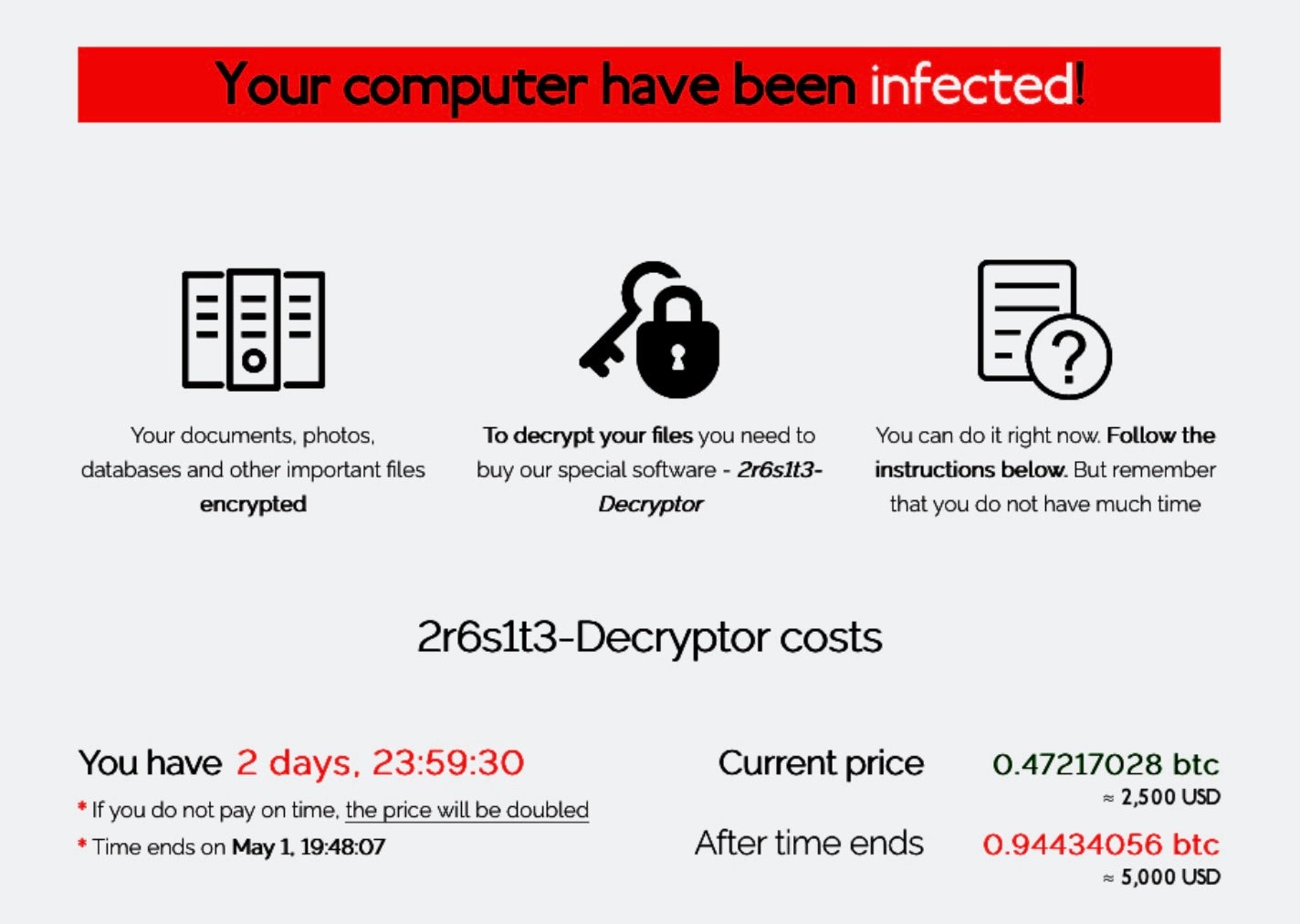
In a recent case of targeted ransomware, rather than asking for a fixed amount, the criminals chose to vary the amount of ransom depending on their attacker’s assessment of the victim’s financial worth.
How Does Ransomware Spread?
You might wonder just where all these ransomware attacks are coming from and how they get on to victims’ machines.
Ransomware isn’t especially complicated to code. The encryption functions exist natively on both Windows and Unix-based machines like macOS and Linux. Some attackers choose to package their own encryption framework to avoid detection by AV software, but there are plenty of open source projects for attackers to choose from. What’s more, with the appearance of Ransomware-as-a-Service such as Cerber RaaS and Shifr Raas, attackers can simply buy off-the-shelf malware to distribute to victims. Reports indicate that portals for accessing these kinds of services are even breaking out of exclusive Dark Net forums to open websites that any would-be hacker can access.
Once an attacker has a ransomware project in hand, they only need to decide how to distribute it. As with other forms of malware, typical infection vectors rely on socially engineering victims into downloading an infected file either from a website or via a phishing email. Often, an MS Office attachment or a malicious PDF file is used which, upon being opened, executes hidden code that in turn downloads the malware payload. In other cases, the ransomware could be the payload delivered by a script on a maliciously-crafted website or downloaded by a fake software installer.
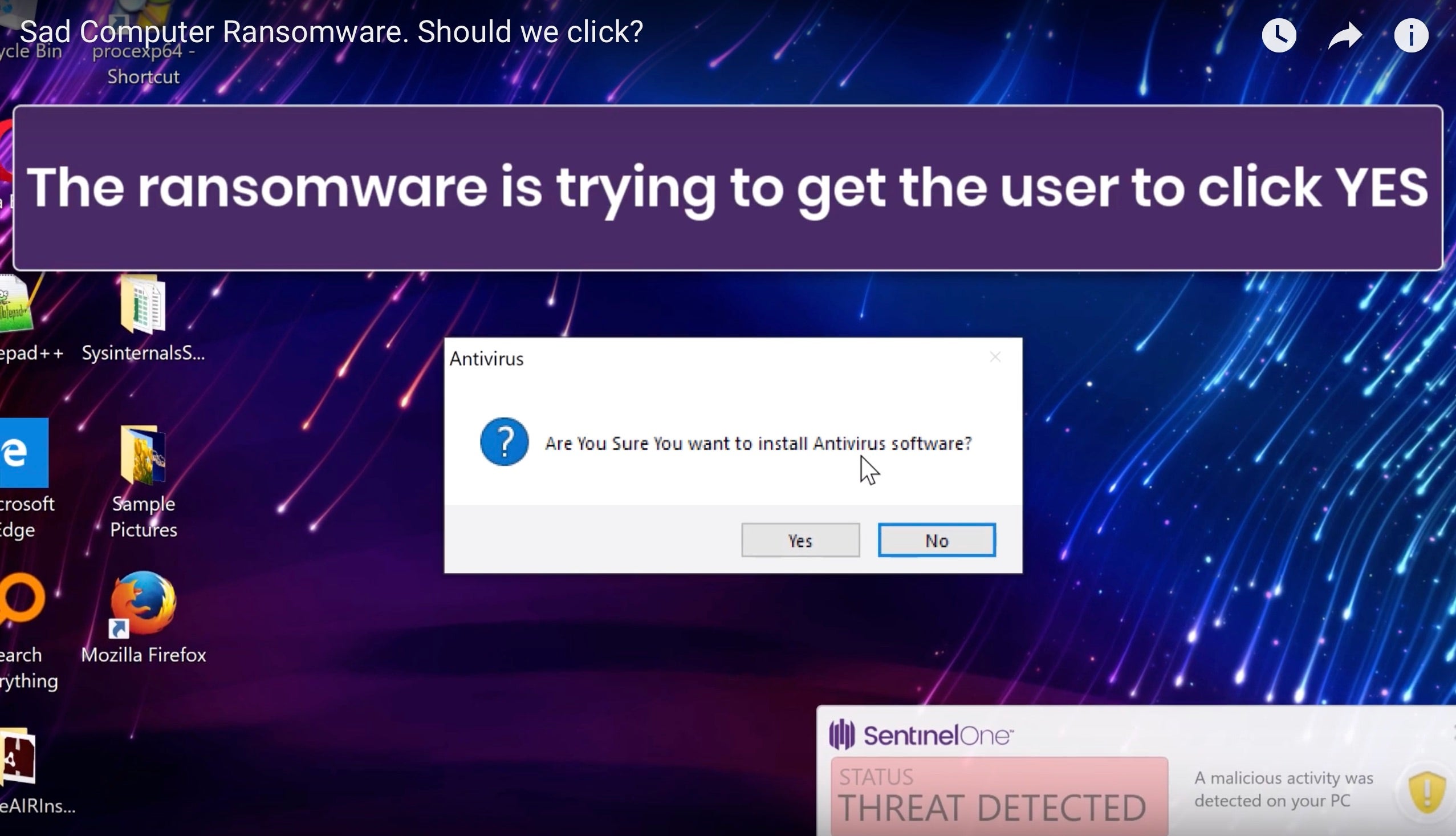
It’s important to note that once the victim has opened the malicious file and given authorisation, everything else happens invisibly behind the scenes. The unsuspecting victim may not know for some minutes, hours or even days that they have been infected, depending on when the malware is coded to trigger the encryption and announce its presence.
In the first ever recorded case of ransomware the program was not set to activate until the victim’s machine had been booted 90 times. Creating a delay between infection and encryption is intended to help cover the attacker’s tracks and make it harder for security researchers to find the infection vector. Criminals are usually in it for the long haul, and they don’t mind waiting for the payday if it helps ensure greater returns.
However, not all ransomware requires user interaction. The SamSam ransomware that was prevalent in 2016 targeted weak passwords on connected devices once it got a foothold on an initial device. In a recent case, a zero-day vulnerability in the popular Oracle WebLogic Server allowed attackers to send ransomware directly to computers and execute itself without any user interaction at all.
Is Ransomware On the Rise?
Yes, it is. As we noted at the beginning of this post, throughout 2018 most threat intel reports were seeing a marked drop-off in ransomware attacks as criminals made a move to cryptojacking. Both web-based and malware-based cryptominers had offered criminals a digital gold mine with virtually no risk. Unlucky for them, with the demise of CoinHive, cryptojacking has been crippled to the point of unprofitability, at least for the time being.
Cue a corresponding uptick in ransomware, with LockerGoga, Troldesh, Golang Shifr and Sad ransomware all making an impact in recent months, hitting infrastructure companies like Norsk Hydro, developers and ordinary end users alike.
Even in the latter half of last year while cryptojacking was in full swing, ransomware never really went away. New variants of Ryuk and KeyPass came to light, the latter coming with features such as manual parameter settings, suggesting that the ransomware could be dropped and tailored to a specific victim by a remote hacker.
How To Defend Against Ransomware
As we’ve seen, reports of ransomware’s untimely demise were overly exaggerated! That means users and enterprise need to be on guard to avoid being infected to start with and to have a response plan if they are.
Backups are a good first line of defense, so long as you backup regularly and rotate backups so that at least one recent backup is offline at all times. Be sure not to rely on Windows built-in Shadow copies, as deleting these is one of the first things most ransomware does.
Secondly, use a security solution that is ransomware-proof. For enterprise, the best defense against ransomware is to use an automated endpoint solution like SentinelOne that can not only block threats on execution, but can also rollback any attacks that do get through without needing to rely on backups.
For users caught out by ransomware with no way to restore or rollback, you are left with some unenviable options. If you are in luck, you may find a public decryptor that will help you to restore your files. If you are not, your choices are accept the data loss, or risk paying off the criminals. Of course, no one wants to reward crime, and there’s no guarantee that the criminals will uphold their end of the deal. In some cases of ransomware, the attackers did not even keep a copy of a decryption key and any victims who had paid up would have been both out of pocket and unable to recover their data.
Conclusion
Ransomware offers an easy pay-day for criminals with low chance of getting caught. It also represents one of the most devastating attacks for victims, who can potentially lose everything from personal data to the very infrastructure that their business relies on. NotPetya and WannaCry remain the two most devastating attacks we’ve seen so far, but there’s every likelihood those will be eclipsed by something worse if businesses don’t learn the lessons of automated protection sooner rather than later. If you would like to see how SentinelOne’s autonomous endpoint solution can protect your business from ransomware, contact us for a free demo.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.