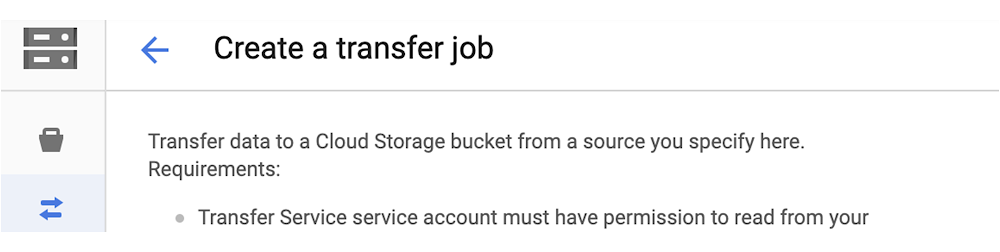
Step 2: Get the name of the service account that will be running the transfer operations.
This service account should be in the GCP Project that will be initiating the transfers. This GCP project will not be in your controlled perimeter by design.
The name of the service account looks like this: project-[ProjectID]@storage-transfer-service.iam.gserviceaccount.com
You can confirm the name of your service account using the API described here.
Step 3: Create an access policy in Access Context Manager.
Note: An organization node can only have one access policy. If you create an access level via the console, it will create an access policy for you automatically.
Or create a policy via the command line, like this:
gcloud access-context-manager policies create
--organization ORGANIZATION_ID --title POLICY_TITLE
When the command is complete, you should see something like this:
Create request issuedWaiting for operation [accessPolicies/POLICY_NAME/create/1521580097614100] to complete...done.Created.
Step 4: Create an access level based on the access policy that limits you to a user or service account.
This is where we create a simple example of an access level based on an access policy. This limits access into the VPC through the service account. Much more complex examples of access level rules can be applied to the VPC. Here, we’ll walk through a simple example that can serve as the “Hello, world” of VPC Service Controls.
Step 4.1: Create a .yaml file that contains a condition that lists the members that you want to provide access to.
- members: - user:sysadmin@example.com - serviceAccount:service@project.iam.gserviceaccount.com
Step 4.2: Save the file
In this example, the file is named CONDITIONS.yaml. Next, create the access level.
gcloud access-context-manager levels create NAME --title TITLE --basic-level-spec CONDITIONS.yaml --combine-function=OR --policy=POLICY_NAME
You should then see output similar to this:
Create request issued for: NAMEWaiting for operation [accessPolicies/POLICY_NAME/accessLevels/NAME/create/1521594488380943] to complete...done.Created level NAME.
Step 5: Bind the access level you created to the VPC Service Control
This step is to make sure that the access level you just created is applied to the VPC that you are creating the hardened perimeter around, as shown here: