Azure webinar series: Security and Privacy for the Cloud Data Warehouse
March 14, 2019
Azure AD Identity Protection and Privileged Identity Management
March 14, 2019EDR, which stands for Endpoint Detection and Response, was born to compensate for the lack of ability in EPP (Endpoint Protection Platform) and legacy AV security solutions to prevent every attack. In this post, you will read about the kinds of threats that triggered the birth of EDR, how it came to be, what problems it faces today, and where its future lies.

The Threat Landscape Evolved
During the early 2010s, both defensive security and offensive operations realized how to run malicious code, without installing any software, by using an executable to completely evade both network and legacy antivirus software. There are a few common ways to achieve execution of code without bringing anything that defenders can scan into the infected system. Let’s take a look at two pervasive threats that led to the need for EDR.
1. Malicious Documents: Phishing Heaven
Most users understand the difference between an application and an MS Word, Excel, PowerPoint or PDF format file to be something like this: the former can execute code, whereas document files can only be read or written to. While this isn’t exactly true, with that understanding, most users would be willing to open a Word document coming from a well-architected phishing campaign. Convincing a user to open what they expect to be a harmless document is much easier than getting someone to double-click an executable that they know will run code (although this does happen, too).
Given the widespread perception of document files as essentially harmless containers of content, malware authors soon found easy ways to infect a target through these kinds of files. The most well-known way to run code from documents is, of course, using “Macros”.
Many security-minded people might now say: “So, what’s the problem? Just don’t allow Macros and you are safe!” It’s a good point, if not entirely correct. However, it overlooks two important realities about the way modern enterprises work and how security fits into the business model.
Macro-based malware files are still out there, and successful, in part because enterprises still use Macros to get their work done. They were invented to increase productivity, and they are very good at that. As a result, for many users and businesses, disallowing Macros is a productivity sacrifice they’re not willing to make. From VBA macros in Excel used to extract data from other systems or automate calculations to MS Word Macros for inserting a letterhead or creating custom styles and formats, Macros have become essential time-saving tools that it is simply unrealistic for many businesses to block.
The second reason why infected documents are still out there is that it’s easier for attackers to get them onto devices than, say, a malicious binary or application that could be scanned by a security solution. With just a small amount of personalization, the chances of getting a recipient to open a document from a phishing email increases exponentially. Send someone a CV, a payment request or an invoice, and if you hit the appropriate person (recruiter, accounts payable), your chances of getting the “click” are statistically pretty high.
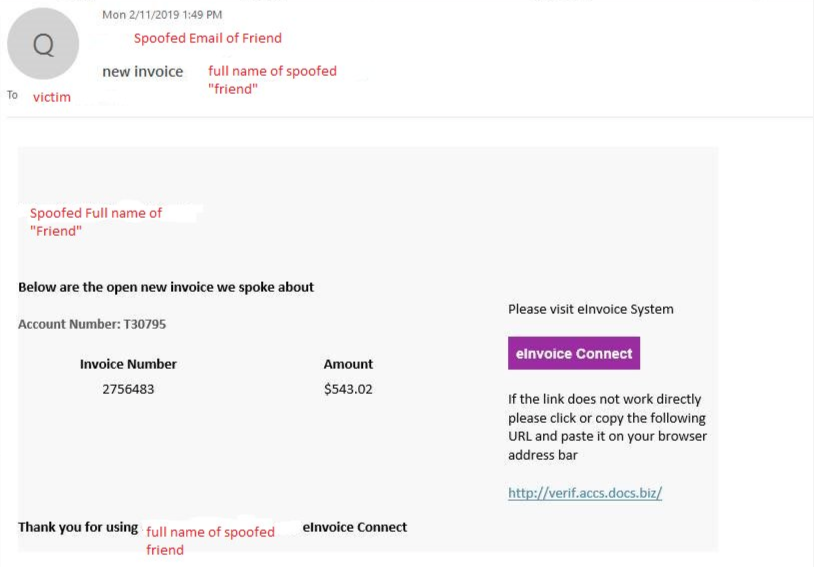
2. EternalBlue: Lateral Movement Comes to Play
Lateral movement techniques are ways for attackers to issue commands, run code and spread across the network. These are not new to most sysadmins, but thanks to a leak of NSA hacking tools, it turns out that some operating system protocols have had vulnerabilities in them for many years that allow attackers to achieve stealthy lateral movement. One notable example is what we now know as “EternalBlue“.
EternalBlue exploits the SMB protocol used for file sharing over the network. This makes the protocol highly attractive to adversaries. EternalBlue was leaked by the Shadow Brokers hacker group on April 14, 2017, and was used as part of the worldwide WannaCry ransomware attack on May 12, 2017. The exploit was also used to help carry out the 2017 NotPetya cyberattack on June 27, 2017 and reportedly is used as part of the Retefe banking trojan since at least September 5, 2017. No Anti-Virus or even next generation EPP can effectively prevent exploitation using EternalBlue.
Fileless malware and system vulnerabilities are just two of a number of common ways that attackers can bypass traditional antivirus (and also more than a few “next-gen” endpoint solutions). So if your company reputation is on the line and you can’t guarantee protection, what can you do? That’s right. You find ways to make sure you are aware of what’s going on with your assets. The new name of the game is Detection.
From Prevention to Detection: EDR Was Born
Back in the day (and to some extent even today), companies hired Incident Response teams to come in and investigate security breaches. In 2013, the most reliable among these was Mandiant. They offered security professionals that were always ready to jump in and find out what had happened. And they were not cheap.
In parallel, some more technical enterprises had begun to invest in visibility tools like Facebook’s osquery and other ways to see into networks. That opened up a new category for the overcrowded market of cybersecurity, and many new solutions were created as a result. Gartner’s Anton Chuvakin coined the term “EDR” to describe this family of new tools focused on visibility.
With that revolution, the inherent problems of EDR solutions started raising their heads.
You needed a highly skilled crew to manage these solutions as they provide so much data, and most of that lacked any context. Enterprises found themselves hiring more and more bodies to solve this problem, but the past couple of years have seen barely a month go by without the news headline of yet another high-profile data breach.
The other critical problem in the area of EDR revolves around “dwell time”. Dwell time represents the time from the infection to the discovery of the malicious activity. Some have suggested an average 90 days dwell time – hardly acceptable to any enterprise – and more recently some products claim they can reduce dwell time to a matter of minutes. Putting aside how reliable self-made claims like these might be for a moment, even 10 seconds is much too long: attackers can run their code, execute their attack, and wrap it up and clean themselves out in a matter of just a few seconds. Any solution that is not detecting in real time is too late in the game.
Cybersecurity firms have tried to solve this problem in several ways.
1. Create a Hunt Chat Bot
In an attempt to simplify the life of the security analyst, one strategy wants the professionally-trained SOC analyst to converse with a chat bot. Getting a chat bot to understand exactly what you mean can often be more challenging than simply writing a SQL query that you do every day, particularly for an experienced threat hunter.
2. Rely On a Custom SOC
If you have a SOC (Security Operations Centre), that’s great! It will allow you to see more and do more to maintain business security. With that said, throwing more uncorrelated data without true context at your team creates alert fatigue and an unhappy team. SOC analysts have advanced skills and should be doing the advanced work. Instead of laboriously trying to piece together the pieces of the picture, they should be working from already-contextualized data that gives them the attack storyline to begin with, so they can use their skills to decide on additional action beyond merely stopping the attack.
3. Provide a Service On Top of the Technology
This is becoming popular (SentinelOne’s Vigilance service is a leader in this field) and it’s a good, sometimes necessary, move: many enterprises don’t have the staff with the needed skillset to hunt and understand the data seen on their own network. Even as valuable as these services can be, there are still aspects of their work you should be automating – like real time response because waiting for a service powered by people may take too long if you don’t. You are again relying on more people to solve a problem, too late. If you had a technology that could see everything that is happening in real time, an on-device AI that could immediately take the needed remediation action, then the problem of dwell time ceases to exist. There’s just real-time detection and response.
The Time is Now: ActiveEDR
Imagine if you had a SOC analyst on each and every endpoint, transforming massive amounts of data into attack stories and raising high-quality, prioritized alerts when threat behavior is observed. That’s the future of ActiveEDR that we at SentinelOne envisioned when we saw the problems other, passive, EDR solutions bring to the enterprise. We were delighted to announce ActiveEDR at RSAC 2019.

At machine speed, ActiveEDR is able to prevent, detect, and respond to advanced attacks regardless of delivery vectors, whether the endpoint is connected to the cloud or not. The SentinelOne solution can provide a security team, small or large, regardless of skill level, with the context to not only understand what is found, but to autonomously block attacks in real time.
We created ActiveEDR as a response to the problems our customers faced, and they have reacted with a resounding “Wow!” to the difference it makes.
The future of EDR is ActiveEDR, and it’s already here! Try a free demo and tell us what you think.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.